Can you hack with Nmap
Nmap is a tool used for network mapping and it is one of the most popular ethical hacking tools in the market. Nmap is used to discover free networks around you. Network administrators find Nmap very useful as they always need to map their networks.
Is it legal to use Nmap
When used properly, Nmap helps protect your network from invaders. But when used improperly, Nmap can (in rare cases) get you sued, fired, expelled, jailed, or banned by your ISP. Reduce your risk by reading this legal guide before launching Nmap.
What is aggressive scan in Nmap
An aggressive scan provides far better information than a regular scan, but is more likely to be detected. It is performed by using the -A option and enables the following: OS detection ( -O ) Version detection ( -sV )
What is the use of Nmap
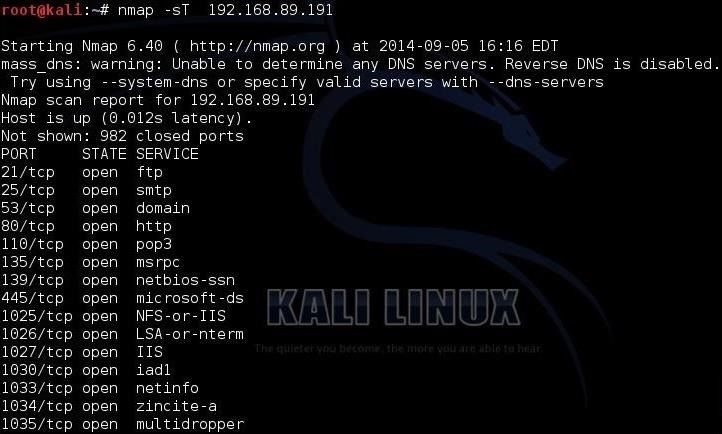
Nmap is now one of the core tools used by network administrators to map their networks. The program can be used to find live hosts on a network, perform port scanning, ping sweeps, OS detection, and version detection.
Can Nmap detect malware
Nmap is able to detect malware and backdoors by running extensive tests on a few popular OS services like on Identd, Proftpd, Vsftpd, IRC, SMB, and SMTP.
Is Nmap a malware
The Nmap project has been wrongfully labeled as a cybersecurity “threat” by Google Chrome's Safe Browsing service. The incident is the latest example of legitimate security tools becoming categorized in the same way as malware, phishing code, or malicious exploits.
Is it illegal to scan the Internet
In the U.S., no federal law exists to ban port scanning. At the state and local level, no clear guidelines exist.
Why do hackers use Nmap
Nmap is a powerful tool for ethical hackers who want to scan and analyze network traffic and logs. It can help you discover hosts, ports, services, vulnerabilities, and other information about your target network. But like any tool, it has its advantages and disadvantages.
Is Nmap a security risk
However, hackers can also use Nmap to access uncontrolled ports on a system. They can run Nmap on a targeted approach, identify vulnerabilities, and exploit them. But Nmap is not only used by hackers – IT security companies also use it to simulate potential attacks that a system may face.
What are the weaknesses of Nmap
What are the disadvantages of using Nmap Nmap has some drawbacks that should be considered before using it. It can be detected and blocked, as it can generate a lot of traffic and noise on the network which can alert network defenders or trigger intrusion detection and prevention systems.
Why is Nmap so good
There are a number of reasons why security pros prefer Nmap over other scanning tools. First, Nmap helps you to quickly map out a network without sophisticated commands or configurations. It also supports simple commands (for example, to check if a host is up) and complex scripting through the Nmap scripting engine.
How do hackers scan ports
Ping scans: A ping scan is considered the simplest port scanning technique. They are also known as internet control message protocol (ICMP) requests. Ping scans send a group of several ICMP requests to various servers in an attempt to get a response.
Is Nmap a vulnerability
Nmap (network mapper) can be used for vulnerability scanning to identify known vulnerabilities. While Nmap is not primarily a vulnerability scanner, Nmap's scripts can help cybersecurity experts perform scans for safety.
Should I delete Nmap
Removing Nmap is a good idea if you are changing install methods (such as from source to RPM or vice versa) or if you are not using Nmap anymore and you care about the few megabytes of disk space it consumes. How to remove Nmap depends on how you installed it initially (see previous sections).
Can the dark web be scanned
There is no way for any company to search the entire dark web. A scan can uncover when your data has been exposed. But it can't find every instance of this because not all personal data is exposed in data breaches.
Is vulnerability scanning illegal
You should also ensure you have a target site owner's permission to carry out vulnerability scanning before commencing any such activity. Doing so without permission is illegal.
Can I Nmap my own IP
All you need is an IP Address and it's best to try it out on your own IP (unless you have the required permissions to do so on any other IP). So, how to begin, very simple just refer to the manual above and try out the different types of scans! There are a plethora of flags that one can use while typing nmap.
Are port scans illegal
Port scanning is not an illegal activity unless someone can prove that it was used intentionally to breach privacy or obtain unauthorized access.
Is it illegal to port scan a network
However – while not explicitly illegal – port and vulnerability scanning without permission can get you into trouble: Civil lawsuits – The owner of a scanned system can sue the person who performed the scan. Even if unsuccessful, the case can waste time and resources on legal costs.
Can Nmap be tracked
Log monitoring tools such as Logwatch and Swatch can certainly help, but the reality is that system logs are only marginally effective at detecting Nmap activity. Special purpose port scan detectors are a more effective approach to detecting Nmap activity.
Is it safe to use Nmap on Windows
Nmap is a safe tool, and it's also a dependable software that's available for cybersecurity professionals. However, it's understandable that nothing is really safe. Even Windows and builds of Linux contact vulnerabilities. There may be some restricted environment where it's against the rules to install it.
Can Google see dark web
"Google One's dark web report helps you scan the dark web for your personal info — like your name, address, email, phone number and Social Security number — and will notify you if it's found," said Google One Director of Product Management Esteban Kozak in March when the feature was first announced.
Can hackers track you on the dark web
By using the Tor browser, internet users can access the Dark Web to communicate and share data in confidence, without the risk of being traced. Most users on the Dark Web are logged into a Virtual Private Network (VPN) to further conceal themselves.
Do hackers use vulnerability scanners
How Scanning Tools Help Hackers. The most commonly used tools are vulnerability scanners that can search for several known vulnerabilities on a target network and potentially detect thousands of vulnerabilities.
Do hackers use CVE
Can Hackers Use CVE to Attack My Organization The short answer is yes but many cybersecurity professionals believe the benefits of CVE outweigh the risks: CVE is restricted to publicly known vulnerabilities and exposures.