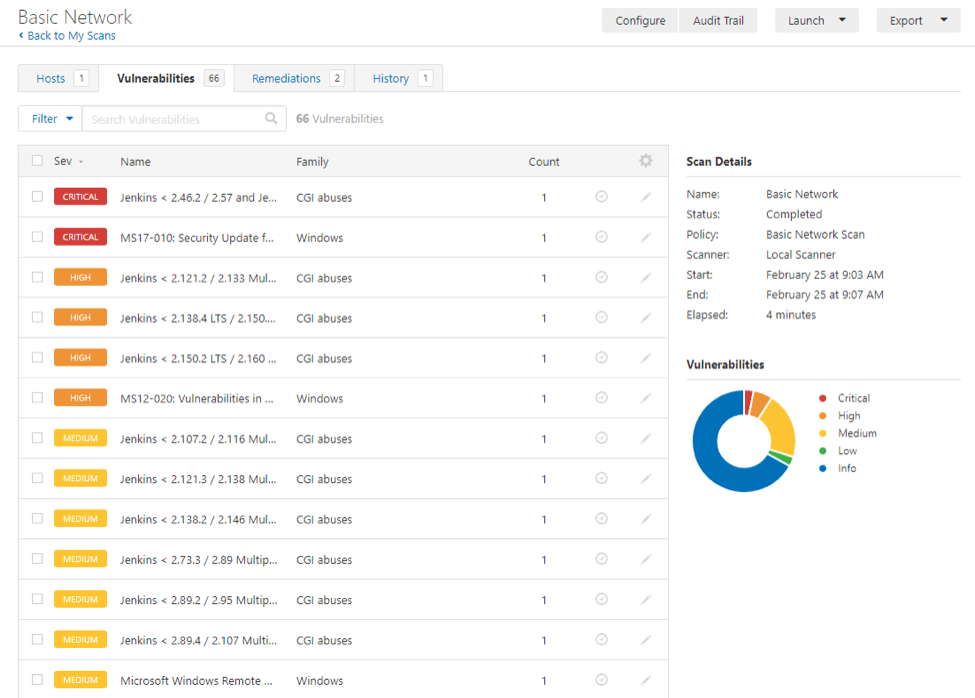
Is Nessus used in Pentesting
Nessus supports penetration testing processes by discovering weaknesses within your attack surface to pinpoint where to pen test and decrease your cyber risk.
Can Nessus detect malware
Nessus allows the ability to utilize a text file with custom hashes to identify known bad files so they can be flagged as malicious during scans. Custom files are supported by: Plugin 88962: Malicious File Detection: User Defined Malware.
Is Nessus safe to use
Nessus is best at performing vulnerability scans, in fact, it gives findings and moreover accurate findings of the assessments. It does not do penetration testing or exploit the vulnerabilities because it is concerned about scanning the systems/applications.
Why is Nessus not secure
The certificate may not be considered secure because "Nessus Certification Authority" is not a trusted valid certificate authority. Because of this, when Nessus is accessed through port 8834, the browser will produce a warning regarding an unsafe connection.
What can Nessus detect
Nessus identifies software flaws, missing patches, malware, denial-of-service vulnerabilities, default passwords and misconfiguration errors, among other potential flaws.
Is Nessus better than Nmap
Nessus: Best for businesses looking for a complete vulnerability scanning tool, especially for professional security auditing. Nmap: Best for organizations looking for a free scanning tool to identify open ports and services and specific vulnerabilities.
Can Nessus scan malware
Nessus allows the ability to utilize a text file with custom hashes to identify known bad files so they can be flagged as malicious during scans. Custom files are supported by: Plugin 88962: Malicious File Detection: User Defined Malware.
Can Nessus exploit vulnerabilities
Nessus identifies exploitable vulnerabilities present in your scan results. The report contains two tables which bring focus to the exploitable vulnerabilities.
What Cannot be identified by Nessus
Nessus cannot identify incorrect IP addresses.
Do hackers use vulnerability scanners
How Scanning Tools Help Hackers. The most commonly used tools are vulnerability scanners that can search for several known vulnerabilities on a target network and potentially detect thousands of vulnerabilities.
What security do hackers use
Two-factor authentication is often used to keep hackers from accessing your personal information. But for hackers, using their real contact information is too risky. Hackers use burner phones, multiple dummy email addresses, and truly encrypted messaging services like Signal to maintain privacy.
How do hackers scan for vulnerabilities
Scanning can be considered a logical extension (and overlap) of active reconnaissance that helps attackers identify specific vulnerabilities. It's often that attackers use automated tools such as network scanners and war dialers to locate systems and attempt to discover vulnerabilities.
What is the most hacked security system
In it's latest tests, Consumer Reports found five home security systems were susceptible to these types of attacks: Adobe Iota, Cove Home Security, Eufy 5-Piece Home Alarm Kit, Ring Alarm, and SimpliSafe the Essentials.
Do hackers need antivirus
In Summary. Antivirus software can help stop hackers, but only to a certain extent. No antivirus offers 100 percent protection, so while antivirus is not the only way to stop hackers, it's still a critical component of your digital security.
Is scanning for vulnerabilities illegal
You should also ensure you have a target site owner's permission to carry out vulnerability scanning before commencing any such activity. Doing so without permission is illegal.
How do hackers find vulnerable sites
Hackers can use scanners to find vulnerable networks by checking exposed ports and then they can exploit vulnerable ports to get control over the device.
What security Cannot be hacked
Local alarm systems, for instance, aren't connected to the internet and thus aren't hackable. Smart home security systems, on the other hand, are connected to the internet, so there is a possibility of hacking, like any other internet-connected product.
Can hackers hack without malware
It's entirely possible to hack a system without malware, you can do this by taking advantage of vulnerabilities in applications/OSs or poor configurations.
Are Nmap scans illegal
When used properly, Nmap helps protect your network from invaders. But when used improperly, Nmap can (in rare cases) get you sued, fired, expelled, jailed, or banned by your ISP. Reduce your risk by reading this legal guide before launching Nmap.
How do hackers access the dark web
To access the dark web, users need a special browser, the most common of which is Tor, short for “The Onion Routing” project, which launched in 2002 and serves millions of users.
What is the hardest device to hack
Most Secure PhonesBittium Tough Mobile 2C. The first device on the list of most secure Phones is the Bittium Tough Mobile 2C.K-iPhone – One of the most secure Phones.Most secure Phones – Solarin From Sirin Labs.Among the most secure Phones – Purism Librem 5.Sirin Labs Finney U1.
What device gets hacked the most
internet-connected security cameras
Then you'd be surprised to know the most commonly device currently used by hackers to access homes and businesses are “internet-connected security cameras”. Are you thinking about the security camera you have at home that lets you watch your dogs every movement directly from your smart phone
Can hackers bypass antivirus
Antivirus software does not have access to operating systems which allow browser-based attacks to bypass them. These attacks infect your device by using malicious scripts and code. To prevent these attacks, some browsers include built-in defensive tools but must be used consistently and correctly to be effective.
Is it illegal to hack a hacker back
U.S. law around active cyber defense
Currently, the Computer Fraud and Abuse Act deems many active cyber defense methods to be illegal, including accessing a computer – such as a hacker's computer – without authorization.
Can hackers use Nmap
Nmap is used to discover free networks around you. Network administrators find Nmap very useful as they always need to map their networks. Hackers also started using Nmap for auditing networks and other purposes.