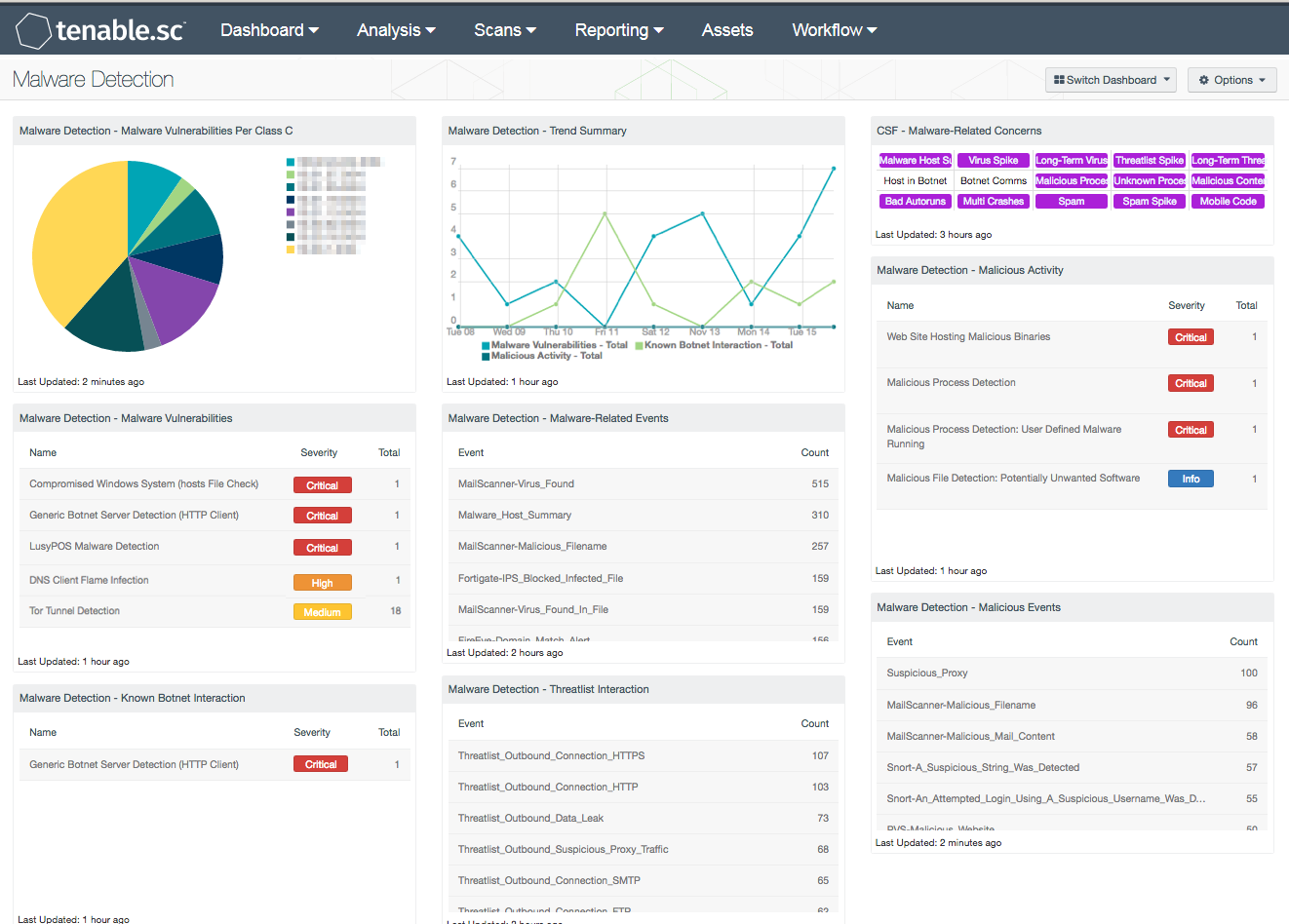
Can Nessus scan for malware
Nessus allows the ability to utilize a text file with custom hashes to identify known bad files so they can be flagged as malicious during scans. Custom files are supported by: Plugin 88962: Malicious File Detection: User Defined Malware.
What can Nessus detect
Nessus identifies software flaws, missing patches, malware, denial-of-service vulnerabilities, default passwords and misconfiguration errors, among other potential flaws.
Can Nessus be used by hackers
Nessus has become the de facto standard in vulnerability scanners, and every white hat hacker should be familiar with it. It is capable of finding known vulnerabilities, but its limitation, like all vulnerability scanners, are false positives.
How does Nessus know if something is vulnerable
Nessus performs its scans by utilizing plugins, which run against each host on the network in order to identify vulnerabilities. Plugins can be thought of as individual pieces of code that Nessus uses to conduct individual scan types on targets.
Can malware hide from scanner
Can malware be undetected Yes, malware can hide itself and antivirus and other protection programs may not catch it.
How do I scan data for malware
FAQsClick on Start.Click on Settings.Click on Update & Security.Choose Windows Security.Click on Virus & Threat Protection.Choose Current Threats.Click on Scan Options/Threat History.Run a new Advanced Scan.
What Cannot be identified by Nessus
Nessus cannot identify incorrect IP addresses.
What is Nessus vs Nmap
Nessus is one of the vulnerability scanners used to find malicious attacks. Whereas, Nmap is not a full vulnerability scanner it is a reporting tool that is used to analyze the service response that is coming in packets and the reporting tool may help to identify vulnerabilities in the network.
Why is Nessus not secure
The certificate may not be considered secure because "Nessus Certification Authority" is not a trusted valid certificate authority. Because of this, when Nessus is accessed through port 8834, the browser will produce a warning regarding an unsafe connection.
Is Nessus a good vulnerability scanner
Nessus is the most widely-used vulnerability scanner in the world. It looks for more than 57,000 possible security weaknesses from an external viewpoint. These weaknesses are known as “exploits” and they can give hackers a way into a system.
Can all malware be detected
Ransomware and adware are usually visible immediately, while spyware wants to stay hidden. The only surefire way to detect all malware before it infects your PC, Mac, or mobile device is with a dedicated antivirus tool.
How do hackers hide malware
Steganography. Steganography is a technique where hackers hide data or communication inside other files, such as images or videos. The hidden data can only be accessed with a special tool or key. What might look like a normal image file could actually contain command and control data for malware on your system.
Can malware be detected
An antivirus scan is the best way to detect and remove malware from your computer or clear a malware infection on your phone. Use a reliable malware removal tool to scan your device, find the malware on it, and clear the infection.
What type of vulnerability will not be found by a vulnerability scanner
Vulnerability scanners cannot detect vulnerabilities for which they do not have a test, plug-in, or signature. Signatures often include version numbers, service fingerprints, or configuration data.
Is Nmap a malware
The Nmap project has been wrongfully labeled as a cybersecurity “threat” by Google Chrome's Safe Browsing service. The incident is the latest example of legitimate security tools becoming categorized in the same way as malware, phishing code, or malicious exploits.
Why do hackers use Nmap
Nmap is a powerful tool for ethical hackers who want to scan and analyze network traffic and logs. It can help you discover hosts, ports, services, vulnerabilities, and other information about your target network. But like any tool, it has its advantages and disadvantages.
Can Nessus exploit vulnerabilities
Nessus identifies exploitable vulnerabilities present in your scan results. The report contains two tables which bring focus to the exploitable vulnerabilities.
Why is Qualys better than Nessus
Qualys and Nessus are two powerful vulnerability scanning tools with some common features and some unique traits. Qualys is more focused on cloud security monitoring while Nessus is a typical web vulnerability assessment tool. Here's a comparison for you to understand how they fare against each other.
Is Nessus better than Nmap
Nessus: Best for businesses looking for a complete vulnerability scanning tool, especially for professional security auditing. Nmap: Best for organizations looking for a free scanning tool to identify open ports and services and specific vulnerabilities.
What are the limitations of Nessus scanner
Nessus® Essentials is free to use to scan any environment, but it is limited to 16 IP addresses per scanner.
What type of malware Cannot be detected
Rootkits. The rootkit malware is dangerous and extremely hard to detect. It hides deep within your infected computer unnoticed and provides administrator privileges (aka root access) to the hacker. This allows the hacker to gain full control over your system without your knowledge.
Can malware be hidden
Malware is usually distributed through malicious websites, emails, and software. Malware can also be hidden in other files, such as image or document files, or even in seemingly innocuous files, such as .exe files.
How do I scan for malware viruses
FAQsClick on Start.Click on Settings.Click on Update & Security.Choose Windows Security.Click on Virus & Threat Protection.Choose Current Threats.Click on Scan Options/Threat History.Run a new Advanced Scan.
How can I detect malware without antivirus
To do that, press Ctrl + Alt + Delete and open the task manager. Then, go to 'Processes' and check for any unfamiliar programs running. To confirm if it is a virus, search online. If confirmed, highlight it and press 'End Process' to stop it.
What types of vulnerabilities are scanned by Nessus
Nessus can scan these vulnerabilities and exposures:Vulnerabilities that could allow unauthorized control or access to sensitive data on a system.Misconfiguration (e.g. open mail relay)Denials of service (Dos) vulnerabilities.Default passwords, a few common passwords, and blank/absent passwords on some system accounts.