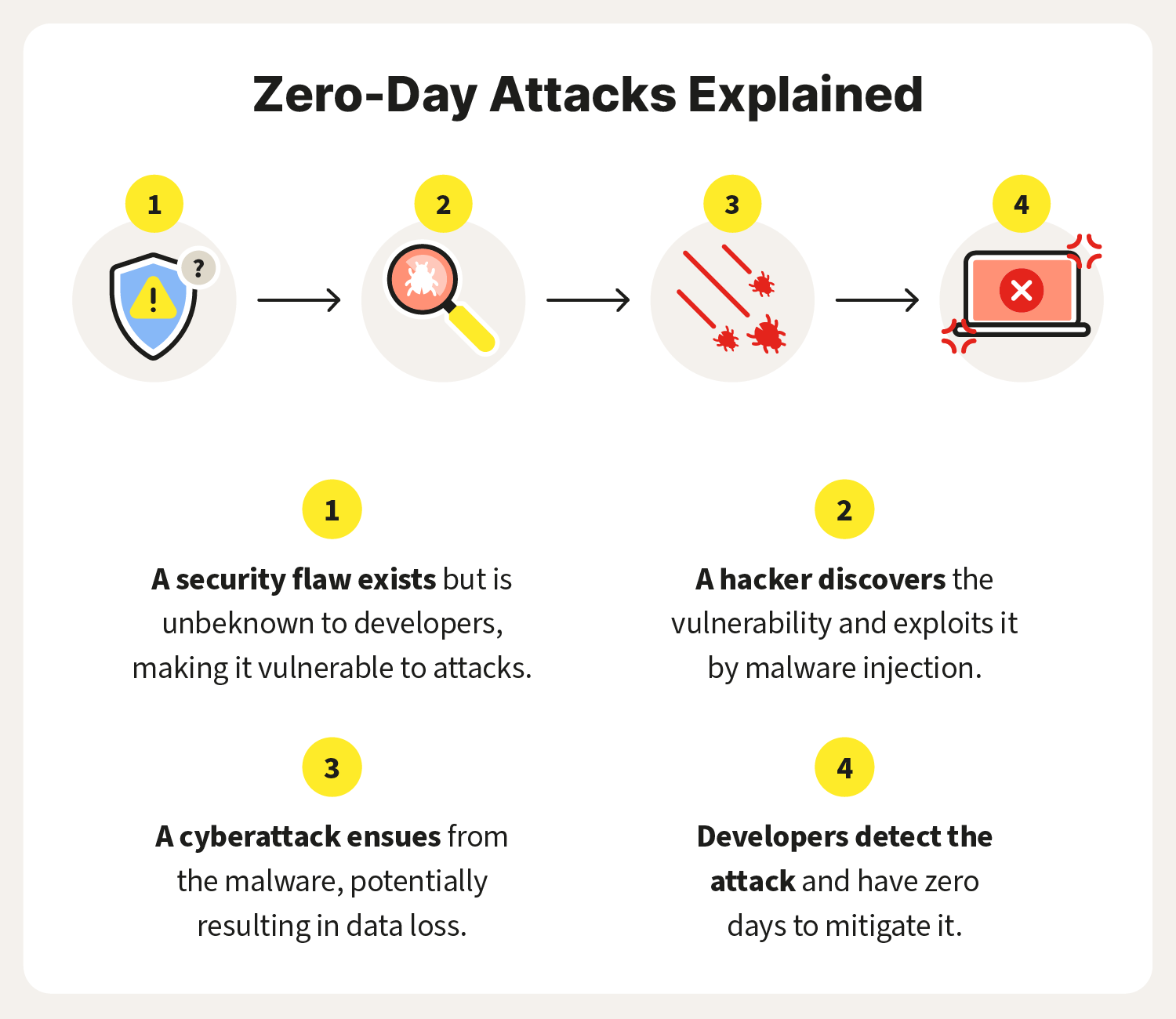
Can you stop a zero-day attack
Preventing zero day attacks is a multistage process. Organizations need the threat intelligence required to identify a potential campaign, tools for acting on this intelligence, and a unified platform that supports rapid, coordinated threat response. Modern cyberattacks are widespread and automated.
What is a zero-day vulnerability can this be stopped
A zero-day vulnerability is a vulnerability in a system or device that has been disclosed but is not yet patched. An exploit that attacks a zero-day vulnerability is called a zero-day exploit.
How we can defend zero-day vulnerability
Vulnerability scanning: Regular scanning is a primary technique for cybersecurity teams to identify security flaws in the software code of applications. Monitoring activities: We can prevent systems from zero-day attacks by monitoring the network and checking unexpected traffic.
How zero-day attack can be detected and prevented
Use a firewall: A firewall can block unauthorized access to your network and help prevent zero-day exploits. Conduct regular security assessments: These can help identify vulnerabilities in your systems before they can be exploited.
What is zero-day weakness
A zero-day (or 0-day) attack is a software vulnerability exploited by attackers before the vendor has become aware of it. At that point, no patch exists, so attackers can easily exploit the vulnerability knowing that no defenses are in place. This makes zero-day vulnerabilities a severe security threat.
What are the 7 ways to help prevent zero-day attacks
For best results, zero-day attack prevention steps you should take include the following:Monitor Reported Vulnerabilities.Install Next-Gen Antivirus Solutions (NGAV)Perform Rigorous Patch Management.Install a Robust Web Application Firewall.Practice the Principle of Least Privilege.
How you can mitigate and remediate zero-day threats
5 zero day vulnerability remediation tipsPatch your systems. Vendors and makers usually act fast to issue a patch once the zero-day vulnerability is discovered.Assess risk exposure.Update your requirements.Strengthen your posture.Track, report, and conclude.
What is the opposite of zero-day vulnerability
Whereas zero-days are a class of vulnerability that is unknown to a software developer or hardware manufacturer, an N-day is a flaw that is already publicly known but may or may not have a security patch available.
Why are zero-day vulnerabilities so difficult to defend against
Since, by definition, a zero-day vulnerability can't be known in advance, there is no way to guard against a specific exploit before it happens. However, there are some things that companies can do to reduce their level of risk exposure.
Can zero-day be detected
A zero-day exploit tends to be difficult to detect. Antimalware software, intrusion detection systems (IDSes) and intrusion prevention systems (IPSes) can't recognize the attack signature because one doesn't yet exist. This is why the best way to detect a zero-day attack is user behavior analytics.
How common are zero-day attacks
According to the Ponemon Institute, 80% of successful breaches were Zero-Day attacks.
Is zero-day a threat
A zero-day threat or attack is an unknown vulnerability in your computer or mobile device's software or hardware. The term is derived from the age of the exploit, which takes place before or on the first (or “zeroth”) day of a security vendors' awareness of the exploit or bug.
How common are zero-day vulnerabilities
According to the Ponemon Institute, 80% of successful breaches were Zero-Day attacks.
How do hackers find zero-day exploits
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability. Attackers have found a new route by exploiting a zero-day vulnerability in Google's Android mobile operating system.
What is the most famous zero-day exploit
Stuxnet, dubbed as “Operation Olympic Games” was the world's first digital weapon, which was created to target the Iranian nuclear program; it leveraged zero-day exploits to infect Windows machines. The malicious computer worm was a product of the concerted efforts of NSA, the CIA, and Israeli intelligence.
How do hackers find zero-day vulnerability
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability. Attackers have found a new route by exploiting a zero-day vulnerability in Google's Android mobile operating system.
How hard is it to find zero-days
A zero-day exploit tends to be difficult to detect. Antimalware software, intrusion detection systems (IDSes) and intrusion prevention systems (IPSes) can't recognize the attack signature because one doesn't yet exist. This is why the best way to detect a zero-day attack is user behavior analytics.
How common are zero day attacks
According to the Ponemon Institute, 80% of successful breaches were Zero-Day attacks.
Why is zero-day malware a strong weapon for hackers
Zero-day attacks are especially dangerous because the only people who know about them are the attackers themselves. Once they have infiltrated a network, criminals can either attack immediately or sit and wait for the most advantageous time to do so.
How do you solve a zero-day exploit
One of the most effective ways to prevent zero-day attacks is deploying a web application firewall (WAF) on the network edge. A WAF reviews all incoming traffic and filters out malicious inputs that might target security vulnerabilities.
Will an anti virus stop a hacker
Software such as Bitdefender, McAfee, Norton Antivirus, and VIPRE prevents hackers. There is no way to guarantee that hackers won't penetrate your devices, but these methods significantly decrease the likelihood of a hacking.
What are the 7 ways to help prevent zero day attacks
For best results, zero-day attack prevention steps you should take include the following:Monitor Reported Vulnerabilities.Install Next-Gen Antivirus Solutions (NGAV)Perform Rigorous Patch Management.Install a Robust Web Application Firewall.Practice the Principle of Least Privilege.
How many zero-day exploits are there
So far this year, a total of 18 security vulnerabilities have been exploited as unpatched zero-days in the wild, according to an analysis – and half of those were preventable flaws.
What do hackers hate the most
4 Things Hackers HateKeep Your Secrets… well…Only Take What You Need.Choose Passwords Wisely.Select a Smart Staff.Know what to look for!Make it tough on the hackers – do all of the Things that Hackers Hate!
Can you get rid of a hacker
Yes, you should be able to remove a hacker by doing a factory reset on your phone. Keep in mind that this solution will remove all of your data, including contacts, third-party apps, photos, and other files. You will need to set up your phone entirely from scratch.