Does all vulnerabilities have CVE to it
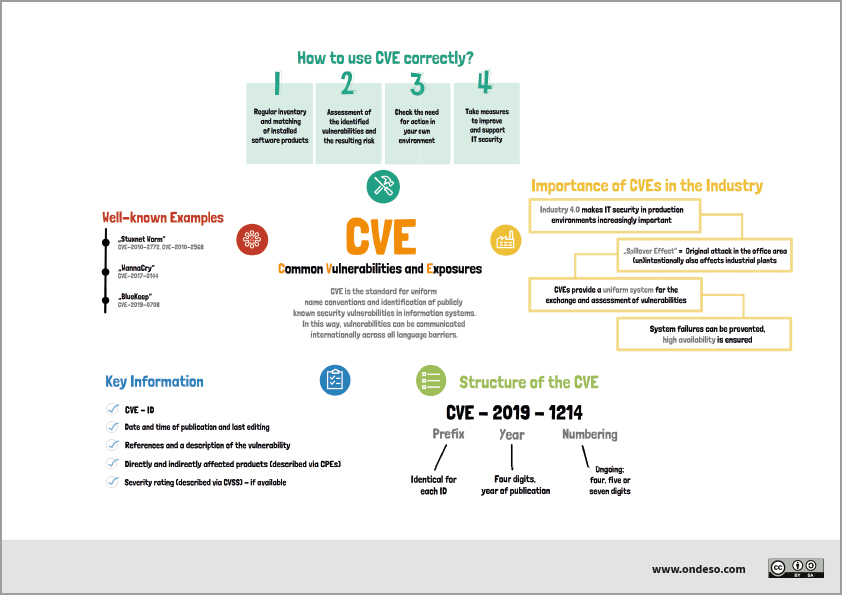
CVE stands for Common Vulnerabilities and Exposures. It is the database of publicly disclosed information on security issues. All organizations use CVEs to identify and track the number of vulnerabilities. But not all the vulnerabilities discovered have a CVE number.
Which vulnerabilities qualify for a CVE
What Qualifies for a CVEIndependently fixable by the end-user.Verified, either by the affected vendor or through other documentation, as negatively impacting security.Relevant to a single affected codebase or product. A vulnerability that affects more than one product gets separate CVEs.
Is CVE a standard
CVE identifiers serve to standardize vulnerability information and unify communication amongst security professionals. Security advisories, vulnerability databases, and bug trackers all employ this standard.
How many CVE vulnerabilities are there
NVD Contains
| CVE Vulnerabilities | 220836 |
|---|---|
| Checklists | 617 |
| US-CERT Alerts | 249 |
| US-CERT Vuln Notes | 4486 |
| OVAL Queries | 10286 |
Can all vulnerabilities be exploited
Most breaches are not due to software vulnerabilities, and most software vulnerabilities are not exploited. To be crystal clear: there are vulnerabilities that must be fixed. And they need to be fixed in a reasonable amount of time to enable end-users to apply mitigations to avoid potential exposure.
What is the difference between CVSS and CVE
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
What is the difference between CVE and CWE
While both standards play a critical role in secure software development, they have different purposes. In summary, CVE is a standard for identifying and naming specific vulnerabilities, while CWE is a standard for classifying and describing the types of weaknesses that can lead to vulnerabilities.
What is CVSS vs CVE
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
Is CVSS the same as CVE
Differences between CVSS and CVE
CVSS is the overall score assigned to a vulnerability. CVE is simply a list of all publicly disclosed vulnerabilities that includes the CVE ID, a description, dates, and comments. The CVSS score is not reported in the CVE listing – you must use the NVD to find assigned CVSS scores.
What is the most common CVE
CVE-2022-22965: The most popular CVE reported in 2022 (also known as Spring4Shell) is an extremely high-impact Injection vulnerability in Spring Framework that allows attackers to make changes remotely to a target system.
What’s the difference between a vulnerability and an exploit
Vulnerability : A vulnerability is a weakness in a system, network or application. Exploit : A tool used to take advantage of the vulnerability. In simple terms, a vulnerability can be defined as a weakness or flaw in a system or software that can potentially be exploited to compromise its security.
What is the difference between vulnerability and exploit in cyber security
A vulnerability is a gap in the armor or weakness that allows people to enter. The exploit is the mechanism that someone uses to get in. For example, a door with a fragile lock has a vulnerability. The exploit uses the keys, hammer, or lockpick to break the lock.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What is difference between CVE and CWE
Whereas the CVE logs real-world instances of vulnerabilities and exposures in specific products, the CWE lists and defines weaknesses commonly seen in digital products. The CWE does not refer to one particular example but provides definitions for widely seen defects.
What is the difference between NVT and CVE
An NVT (network vulnerability test) is a script that is being executed towards a targeted system and does vulnerability checks (remotely or locally), which also includes vulnerabilities that have got a CVE assigned to it. However, there are also NVTs without a referenced CVE.
What is CWE vs CVE
Whereas the CVE logs real-world instances of vulnerabilities and exposures in specific products, the CWE lists and defines weaknesses commonly seen in digital products. The CWE does not refer to one particular example but provides definitions for widely seen defects.
What is CCE vs CVE
CVE provides this capability for information security vulnerabilities, CCE assigns a unique, common identifier to a particular security-related configuration issue. The name of the imported file. The type of the list, that is, if it is a CVE or CCE list.
Why is CVE is very important
It allows organizations to keep track of and prioritize vulnerabilities, compare their severity, and track their cybersecurity posture over time. The CVE has been operating since 1999 and is run by the MITRE Corporation. It is important for risk management, vulnerability identification, and cybersecurity strategy.
Can vulnerability be exploited
Some vulnerabilities can only be exploited by an attacker working locally, either with direct access to the device itself or over a local network. In these cases, the attacker may be an authorized user trying to gain unauthorized privileges or access, or an on-the-spot intruder.
Are vulnerabilities the same as threats
A threat and a vulnerability are not one and the same. A threat is a person or event that has the potential for impacting a valuable resource in a negative manner. A vulnerability is that quality of a resource or its environment that allows the threat to be realized. An armed bank robber is an example of a threat.
Is a vulnerability the same as an exploit
A vulnerability is a gap in the armor or weakness that allows people to enter. The exploit is the mechanism that someone uses to get in. For example, a door with a fragile lock has a vulnerability. The exploit uses the keys, hammer, or lockpick to break the lock.
Can you explain the difference between a vulnerability and an exploit
Vulnerability : A vulnerability is a weakness in a system, network or application. Exploit : A tool used to take advantage of the vulnerability. In simple terms, a vulnerability can be defined as a weakness or flaw in a system or software that can potentially be exploited to compromise its security.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 3 factors that can create vulnerability
Vulnerability relates to a number of factors, including:Physical factors. e.g. poor design and construction of buildings, unregulated land use planning, etc.Social factors.Economic factors.Environmental factors.
What is the difference between a CVSS and CVE
CVSS is the overall score assigned to a vulnerability. CVE is simply a list of all publicly disclosed vulnerabilities that includes the CVE ID, a description, dates, and comments. The CVSS score is not reported in the CVE listing – you must use the NVD to find assigned CVSS scores.