How many CVE vulnerabilities are there
NVD Contains
| CVE Vulnerabilities | 220836 |
|---|---|
| Checklists | 617 |
| US-CERT Alerts | 249 |
| US-CERT Vuln Notes | 4486 |
| OVAL Queries | 10286 |
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
Can all vulnerabilities be exploited
Most breaches are not due to software vulnerabilities, and most software vulnerabilities are not exploited. To be crystal clear: there are vulnerabilities that must be fixed. And they need to be fixed in a reasonable amount of time to enable end-users to apply mitigations to avoid potential exposure.
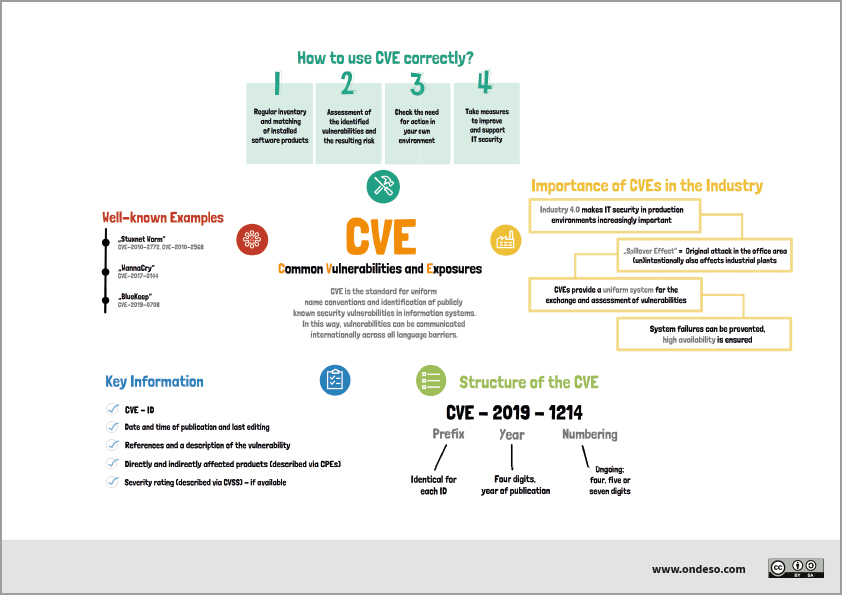
What are CVEs and why are they important
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed information security vulnerabilities and exposures. CVE was launched in 1999 by the MITRE corporation to identify and categorize vulnerabilities in software and firmware.
What is the difference between CVE and vulnerability
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
Does CVE mean vulnerability
Common Vulnerabilities and Exposures
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures. What is the Difference Between CVE and CVSS CVE is the database of known vulnerabilities and exposures.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 13 strands of vulnerability
Dorset Police outline 13 strands of vulnerability which is recognised nationally as:adults at risk.child abuse and neglect.female genital mutilation.honour based abuse.child sexual exploitation.human trafficking and modern day slavery.managing offenders.prostitution.
Are all vulnerabilities considered as bug
A bug is a flaw or vulnerability in the software or hardware design that can be potentially exploited by the attackers. These security bugs can be used to exploit various vulnerabilities by compromising – user authentication, authorization of access rights and privileges, data confidentiality, and data integrity.
Which vulnerability cannot be discovered
Business logic vulnerabilities:
These vulnerabilities cannot be found through automated scanning.
How are CVEs found
CVE reports can come from anywhere. A vendor, a researcher, or just an astute user can discover a flaw and bring it to someone's attention. Many vendors offer bug bounties to encourage responsible disclosure of security issues. If you find a vulnerability in open source software you should submit it to the community.
How does a vulnerability become a CVE
The reporter requests a CVE ID, which is then reserved for the reported vulnerability. Once the reported vulnerability is confirmed by the identification of the minimum required data elements for a CVE Record, the record is published to the CVE List.
Which vulnerabilities qualify for a CVE
What Qualifies for a CVEIndependently fixable by the end-user.Verified, either by the affected vendor or through other documentation, as negatively impacting security.Relevant to a single affected codebase or product. A vulnerability that affects more than one product gets separate CVEs.
What is CVSS vs CVE
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
What are the 4 stages of identifying vulnerabilities
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.
How to be 100% vulnerable
Be in the moment.
Slowing down the thoughts in your head and living in the present moment with someone is ideal for true vulnerability. Simply looking someone in the eye, listening to what they are saying, and giving them your time will surprise you in how much vulnerability it can bring.
What type of vulnerabilities will not be found by a vulnerability scanner
Vulnerability scanners cannot detect vulnerabilities for which they do not have a test, plug-in, or signature. Signatures often include version numbers, service fingerprints, or configuration data.
Are there different types of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What types of vulnerabilities are not identified by non credentialed scans
Credential-based vs.
Unfortunately, non-credentialed scans do not provide deeper insight into application and operating system vulnerabilities not exposed to the network, or those vulnerabilities behind a firewall. It provides a false hope that the system is safe.
What are the limitations of vulnerability scans
Vulnerability scanners are limited in their ability to detect unknown vulnerabilities, as they rely on databases of known vulnerabilities to identify potential threats.
Is CVE a vulnerability
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
Who creates a CVE for vulnerability
The Mitre Corporation
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
What are the 3 types of vulnerability
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
What are the 3 criteria for assessing vulnerability
The assessment framework involves three dimensions: engagement, intent and capability, which are considered separately.
Why can’t I get vulnerable
If someone constantly experiences rejection from programs, jobs, or intimate relationships, they may feel uneasy putting themselves out there again. Fear of vulnerability can also stem from abusive relationships or criticism from family members; such hurt can impact a person's mental health and lead to low self-esteem.