Can you hack with Nmap
Nmap is a tool used for network mapping and it is one of the most popular ethical hacking tools in the market. Nmap is used to discover free networks around you. Network administrators find Nmap very useful as they always need to map their networks.
Why should you not scan any outside networks without permission
The scan source ISP may track down the user corresponding to the reported IP address and time, then chide the user or even kick him off the service. Port scanning without authorization is sometimes against the provider's acceptable use policy (AUP).
Is Nmap a port scanner
Nmap is the world's leading port security network scanner. The Nmap hosted security tool can help you determine how well your firewall and security configuration is working.
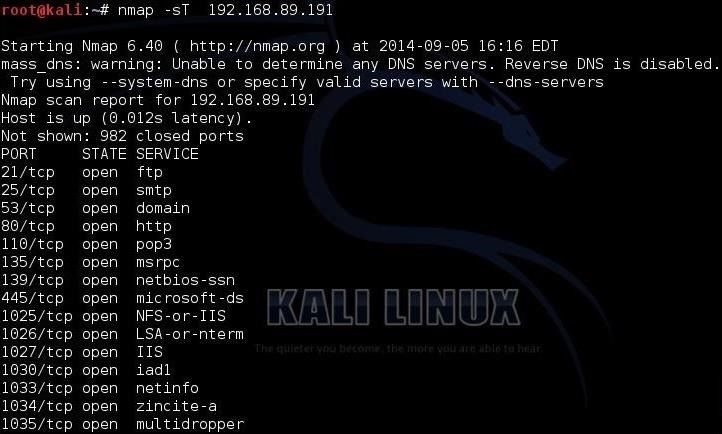
What is the use of port scanning
A port scan is a network reconnaissance technique designed to identify which ports are open on a computer. This can enable the scanner to identify the applications running on the system as certain programs listen on particular ports and react to traffic in certain ways.
Can Nmap be traced
Log monitoring tools such as Logwatch and Swatch can certainly help, but the reality is that system logs are only marginally effective at detecting Nmap activity. Special purpose port scan detectors are a more effective approach to detecting Nmap activity. Two common examples are PortSentry and Scanlogd.
Can Nmap crash a server
It should also be noted that Nmap has occasionally been known to crash poorly written applications, TCP/IP stacks, and even operating systems. While this is extremely rare, it is important to keep in mind. Nmap should never be run against mission critical systems unless you are prepared to suffer downtime.
Are network scans illegal
However – while not explicitly illegal – port and vulnerability scanning without permission can get you into trouble: Civil lawsuits – The owner of a scanned system can sue the person who performed the scan. Even if unsuccessful, the case can waste time and resources on legal costs.
Is vulnerability scanning illegal
You should also ensure you have a target site owner's permission to carry out vulnerability scanning before commencing any such activity. Doing so without permission is illegal.
Who to use Nmap
Here's a breakdown of the primary use of Nmap: Scan every active IP address. You can get detailed information on every IP active on your network to determine whether an IP has been compromised. Nmap will tell you whether a legitimate service or an external hacker is using the IP.
Is Nmap A sniffer
As a network analyzer or packet sniffer, Nmap is extremely versatile. For example, it allows the user to scan any IP active on their network.
Why do hackers scan ports
A port scan is a common technique hackers use to discover open doors or weak points in a network. A port scan attack helps cyber criminals find open ports and figure out whether they are receiving or sending data. It can also reveal whether active security devices like firewalls are being used by an organization.
What can hackers accomplish using malicious port scanning
Port scanning can be used in a malicious way to find out all the openings to a computer's operating system; this is known as the “fingerprint” of the operating system. Port scanning cannot find out the topology of the network, computer names, usernames, or passwords.
How can you tell if someone is using Nmap
Log monitoring tools such as Logwatch and Swatch can certainly help, but the reality is that system logs are only marginally effective at detecting Nmap activity. Special purpose port scan detectors are a more effective approach to detecting Nmap activity. Two common examples are PortSentry and Scanlogd.
Can Nmap detect malware
Nmap is able to detect malware and backdoors by running extensive tests on a few popular OS services like on Identd, Proftpd, Vsftpd, IRC, SMB, and SMTP.
Is Nmap a malware
The Nmap project has been wrongfully labeled as a cybersecurity “threat” by Google Chrome's Safe Browsing service. The incident is the latest example of legitimate security tools becoming categorized in the same way as malware, phishing code, or malicious exploits.
Is it safe to install Nmap
Nmap is a safe tool, and it's also a dependable software that's available for cybersecurity professionals.
Is it legal to use hacked data
No Hacking is Innocent
Many individuals do not view accessing a partner or friend's email or social media account as a criminal act. However, in most countries, doing so without permission is illegal. In one notable case, a man in the US faced a potential 5-year prison sentence for reading his wife's emails.
Do hackers use CVE
Can Hackers Use CVE to Attack My Organization The short answer is yes but many cybersecurity professionals believe the benefits of CVE outweigh the risks: CVE is restricted to publicly known vulnerabilities and exposures.
Do hackers use vulnerability scanners
How Scanning Tools Help Hackers. The most commonly used tools are vulnerability scanners that can search for several known vulnerabilities on a target network and potentially detect thousands of vulnerabilities.
Is Nmap still being used
Despite being created back in 1997, Nmap remains the gold standard against which all other similar tools, either commercial or open source, are judged. Nmap has maintained its preeminence because of the large community of developers and coders who help to maintain and update it.
What are the weaknesses of Nmap
What are the disadvantages of using Nmap Nmap has some drawbacks that should be considered before using it. It can be detected and blocked, as it can generate a lot of traffic and noise on the network which can alert network defenders or trigger intrusion detection and prevention systems.
Do people still use Nmap
Nmap has maintained its preeminence because of the large community of developers and coders who help to maintain and update it. The Nmap community reports that the tool, which anyone can get for free, is downloaded several thousand times every week.
Are port scans illegal
Port scanning is not an illegal activity unless someone can prove that it was used intentionally to breach privacy or obtain unauthorized access.
Is port scanning not illegal
In the U.S., no federal law exists to ban port scanning. At the state and local level, no clear guidelines exist.
What can hackers do with Nmap
This program scans the network your computer is connected to and provides a list of ports, device names, operating systems, and other identifiers to help you understand your connection status. However, hackers can also use Nmap to access uncontrolled ports on a system.