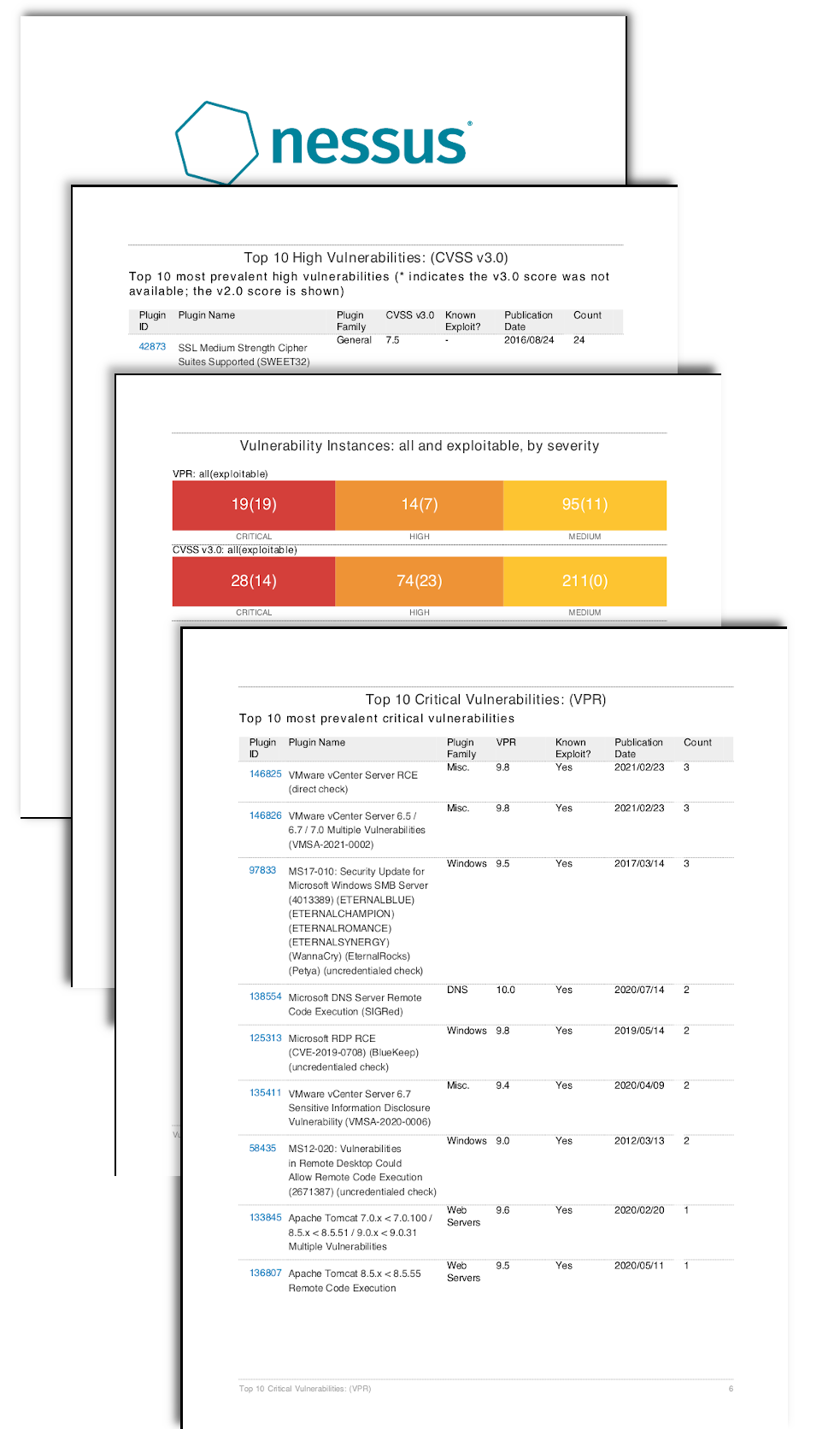
Can Nessus exploit vulnerabilities
Nessus identifies exploitable vulnerabilities present in your scan results. The report contains two tables which bring focus to the exploitable vulnerabilities.
Is Nessus a good vulnerability scanner
Nessus is the most widely-used vulnerability scanner in the world. It looks for more than 57,000 possible security weaknesses from an external viewpoint. These weaknesses are known as “exploits” and they can give hackers a way into a system.
Is Nessus a vulnerability management tool
Nessus provides a fast, user-friendly way to find and fix vulnerabilities in many kinds of IT assets, including cloud-based and virtualized resources. As of April 2023, it covers more than 76,000 Common Vulnerabilities and Exposures.
Can Nessus be used by hackers
Nessus has become the de facto standard in vulnerability scanners, and every white hat hacker should be familiar with it. It is capable of finding known vulnerabilities, but its limitation, like all vulnerability scanners, are false positives.
Who can exploit vulnerability
Some vulnerabilities can only be exploited by an attacker working locally, either with direct access to the device itself or over a local network. In these cases, the attacker may be an authorized user trying to gain unauthorized privileges or access, or an on-the-spot intruder.
Why is Nessus not secure
The certificate may not be considered secure because "Nessus Certification Authority" is not a trusted valid certificate authority. Because of this, when Nessus is accessed through port 8834, the browser will produce a warning regarding an unsafe connection.
Is Nessus better than Nmap
Nessus: Best for businesses looking for a complete vulnerability scanning tool, especially for professional security auditing. Nmap: Best for organizations looking for a free scanning tool to identify open ports and services and specific vulnerabilities.
Is Nessus better than Qualys
Qualys WAS rates 4.4/5 stars with 16 reviews. By contrast, Tenable Nessus rates 4.5/5 stars with 267 reviews. Each product's score is calculated with real-time data from verified user reviews, to help you make the best choice between these two options, and decide which one is best for your business needs.
Does Nessus scan for CVE
All Nessus and Passive Vulnerability Scanner plugins receive mappings to CVE, Bugtraq and other identifiers.
What vulnerabilities can Nessus detect
Nessus can scan these vulnerabilities and exposures:Vulnerabilities that could allow unauthorized control or access to sensitive data on a system.Misconfiguration (e.g. open mail relay)Denials of service (Dos) vulnerabilities.Default passwords, a few common passwords, and blank/absent passwords on some system accounts.
Can all vulnerabilities be exploited
Most breaches are not due to software vulnerabilities, and most software vulnerabilities are not exploited. To be crystal clear: there are vulnerabilities that must be fixed. And they need to be fixed in a reasonable amount of time to enable end-users to apply mitigations to avoid potential exposure.
Which vulnerability is exploited the most
The most exploited vulnerabilities are CVE-2022-30190 (Follina); CVE-2022-26134 (Atlassian); CVE-2022-22954 (VMware); CVE-2022-1040 (Sophos Firewall); and CVE-2022-24521 (Windows). The first four all have a Qualys vulnerability score (QVS) of 100; the last scores 95.
Why is Qualys better than Nessus
Qualys and Nessus are two powerful vulnerability scanning tools with some common features and some unique traits. Qualys is more focused on cloud security monitoring while Nessus is a typical web vulnerability assessment tool. Here's a comparison for you to understand how they fare against each other.
Why is Nessus scanner the best
Tenable Nessus is versatile and flexible to use. This software can be used to security scans, network scanning, vulnerability assessment and scanning. It's interface is user friendly and anyone can use it very easily. It has ability to automate scanning and reporting tasks.
Can Nessus detect Log4j vulnerability
When scanning with Credentials and Thorough enabled, Nessus will show the file that are vulnerable. Nessus is not checking all your application code for the use of the log4j function. If you are sure you are not using log4j, then remove it from your environment and reduce your attack surface.
How does Nessus rate vulnerabilities
When you view vulnerabilities in scan results, Tenable Nessus shows severity based on CVSSv2 scores or CVSSv3 scores, depending on your configuration. You can choose whether Tenable Nessus calculates the severity of vulnerabilities using CVSSv2 or CVSSv3 scores by configuring your default severity base setting.
What Cannot be identified by Nessus
Nessus cannot identify incorrect IP addresses.
Who all can exploit cyber vulnerabilities
What is Cyber Security Vulnerabilities Any flaw in an organization's internal controls, system procedures, or information systems is a vulnerability in cyber security. Cybercriminals and Hackers may target these vulnerabilities and exploit them through the points of vulnerability.
Who might exploit vulnerabilities
A vulnerability in security refers to a weakness or opportunity in an information system that cybercriminals can exploit and gain unauthorized access to a computer system. Vulnerabilities weaken systems and open the door to malicious attacks.
Who might exploit vulnerability
cybercriminals
A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. After exploiting a vulnerability, a cyberattack can run malicious code, install malware, and even steal sensitive data.
Which software has the most vulnerabilities
Top 50 Products By Total Number Of "Distinct" Vulnerabilities
| Product Name | Number of Vulnerabilities | |
|---|---|---|
| 1 | Debian Linux | 8190 |
| 2 | Android | 5238 |
| 3 | Fedora | 4517 |
| 4 | Ubuntu Linux | 3962 |
What is the difference between Nessus and Qualys
Qualys and Nessus are two powerful vulnerability scanning tools with some common features and some unique traits. Qualys is more focused on cloud security monitoring while Nessus is a typical web vulnerability assessment tool.
What are the limitations of Nessus scanner
Nessus® Essentials is free to use to scan any environment, but it is limited to 16 IP addresses per scanner.
Who has the strongest cyber security
After looking at the many different studies done on the cybersecurity of nations around the world, we've determined the following five to be the best:United States.Finland.United Kingdom.Republic of Korea.Denmark.
Which vulnerabilities were exploited
List of Top 10 Exploited VulnerabilitiesZeroLogon (CVE-2020-1472)Log4Shell (CVE-2021-44228)ICMAD (CVE-2022-22536)ProxyLogon (CVE-2021-26855)Spring4Shell (CVE-2022-22965)Atlassian Confluence RCE (CVE-2022-26134)VMware vSphere (CVE-2021-21972)Google Chrome Zero-Day (CVE-2022-0609)