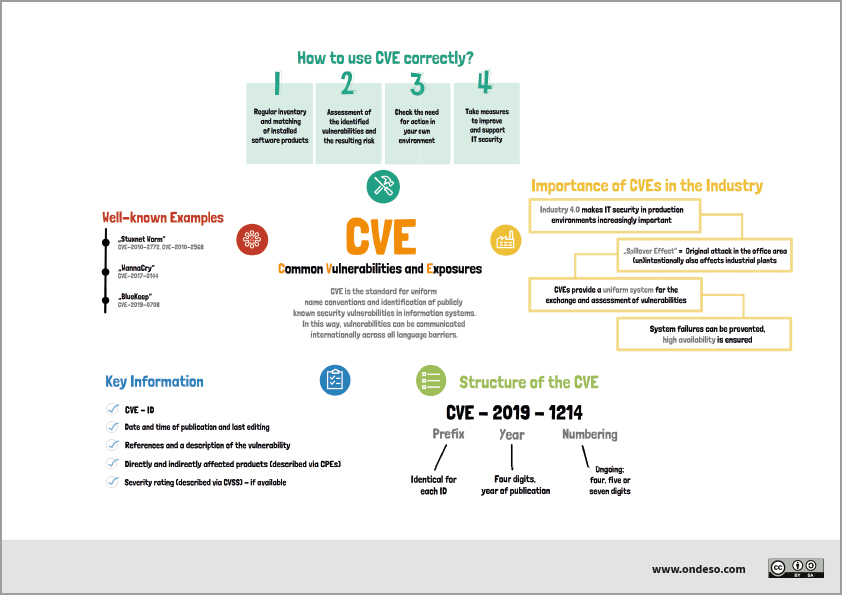
How does CVE naming work
A CVE identifier takes the form of CVE-[Year]-[Number]. Year represents the year in which the vulnerability was reported. The number is a sequential number assigned by the CNA.
What are CVEs common identifiers
CVE Identifiers (also called "CVE names," "CVE numbers," "CVE-IDs," and "CVEs") are unique, common identifiers for publicly known information security vulnerabilities. Each CVE Identifier includes the following: – CVE identifier number (i.e., "CVE-1999-0067"). – Indication of "entry" or "candidate" status.
How many CVEs are there
Published CVE Records
| Year | 2023 | 2022 |
|---|---|---|
| Qtr3 | N/A | 6,448 |
| Qtr2 | N/A | 6,365 |
| Qtr1 | 7,015 | 6,015 |
| TOTAL | 7,015 | 25,059 |
WHO publishes CVEs
the MITRE corporation
Founded in 1999, the CVE program is maintained by the MITRE corporation and sponsored by the U.S. Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA).
How are CVE numbers assigned
CVE identifiers are assigned by a CVE Numbering Authority (CNA). There are about 100 CNAs, representing major IT vendors—such as Red Hat, IBM, Cisco, Oracle, and Microsoft—as well as security companies and research organizations. MITRE can also issue CVEs directly.
Who assigns CVE numbers
The Mitre Corporation
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
How are CVEs discovered
There is one CVE Record for each vulnerability on the CVE List. Vulnerabilities are first discovered, then reported to the CVE Program. The reporter requests a CVE ID, which is then reserved for the reported vulnerability.
What is CVE vulnerability naming standard
The Common Vulnerabilities and Exposures (CVE) vulnerability naming scheme is a dictionary of common names for publicly known IT system vulnerabilities. It is an emerging industry standard that has achieved wide acceptance by the security industry and a number of government organizations.
Are CVE numbers unique
A CVE ID is a unique, alphanumeric identifier assigned by the CVE Program. Each identifier references a specific vulnerability. The “Year” portion is the year that the CVE ID was reserved or the year the vulnerability was made public. The year portion is not used to indicate when the vulnerability was discovered.
What is the name of CVE
Common Vulnerabilities and Exposures (CVE) is a dictionary of common names (i.e., CVE Identifiers) for publicly known information security vulnerabilities.
Where do CVE numbers come from
CVE identifiers are assigned by a CVE Numbering Authority (CNA). There are about 100 CNAs, representing major IT vendors—such as Red Hat, IBM, Cisco, Oracle, and Microsoft—as well as security companies and research organizations. MITRE can also issue CVEs directly.
How do you identify a vulnerability code
Code vulnerability is a term related to the security of your software. It is a flaw in your code that creates a potential risk of compromising security. This flaw will allow hackers to take advantage of your code by attaching an endpoint to extract data, tamper your software or worse, erase everything.
How does a CVE get created
There is one CVE Record for each vulnerability on the CVE List. Vulnerabilities are first discovered, then reported to the CVE Program. The reporter requests a CVE ID, which is then reserved for the reported vulnerability.
How does a vulnerability become a CVE
The reporter requests a CVE ID, which is then reserved for the reported vulnerability. Once the reported vulnerability is confirmed by the identification of the minimum required data elements for a CVE Record, the record is published to the CVE List.
How are security vulnerabilities identified
What are the sources to identify security vulnerability within an application Security scan of an application using third party tools. Regularly monitoring security vulnerabilities in related applications or environments (Operating System, Database, Third party libraries etc).
What does CVE mean code
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
What are the 4 stages of identifying vulnerabilities
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.
What is CVE ID and CVSS
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
Who determines CVE
CVE Numbering Authority
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
What are the 4 main types of security vulnerability
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
Do all vulnerabilities have a CVE
CVE stands for Common Vulnerabilities and Exposures. It is the database of publicly disclosed information on security issues. All organizations use CVEs to identify and track the number of vulnerabilities. But not all the vulnerabilities discovered have a CVE number.
What are the 5 phases of vulnerability assessment
The Five Phases of Penetration Testing. There are five penetration testing phases: reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Let's take a closer look at the 5 Penetration Testing phases.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
How are CVEs created
The process of creating a CVE Record begins with the discovery of a potential cybersecurity vulnerability. The information is then assigned a CVE ID by a CVE Numbering Authority (CNA), a Description and References are added by the CNA, and then the CVE Record is posted on the CVE website by the CVE Program Secretariat.
What is the 4 C’s in security
These four layers are Code security, Container security, Cluster security, and Cloud security. Let's take a deep dive into each of the C's to understand them better and also answer some of the most asked questions about the 4C's.