How are certificates authenticated
The process is generally as follows: A user makes a request to access a protected resource. The server presents its certificate to the browser, and the browser validates the public certificate. An authentication request is made from the server for the user to authenticate themselves.
What does it mean to authenticate a certificate
Certificate-Based Authentication Definition
Generally speaking, client certificate-based authentication refers to an end user's device proving its own identity by providing a digital certificate that can be verified by a server in order to gain access to a network or other resources.
What is an example of certificate authentication
By asking information only the user should know (a password or a passphrase) By asking something only the user should have in his possession (use a private key and a public key, SSL certificate or card, or a digital certificate) By asking for something that's physically part of the user (a thumbprint or retinal scan)
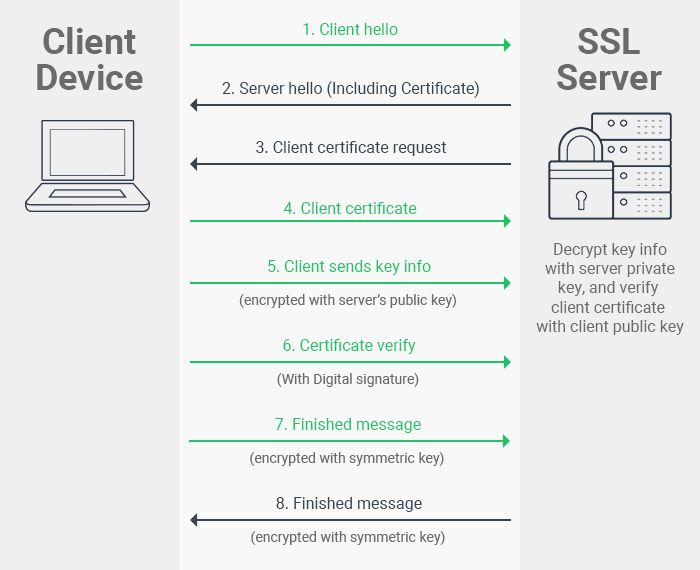
How does SSL certificate authentication work
The web server sends the browser/server a copy of its SSL certificate. The browser/server checks to see whether or not it trusts the SSL certificate. If so, it sends a message to the web server. The web server sends back a digitally signed acknowledgement to start an SSL encrypted session.
Can you verify the authenticity of a certificate
You can also contact the provider or the issuer to confirm the authenticity of the certificate, or use online tools or platforms that allow you to verify certificates digitally. Finally, you can ask for feedback or recommendations from other learners, employers, or experts who have taken or accepted the certificate.
What is authenticated vs certified
A certification is used for verifying a notary. Authentications are used for verifying recorders of deeds, circuit clerks, judges, county clerks and the State Registrar (i.e., birth certificate, marriage statement and divorce statement).
What is the best way to authenticate
Implement two-factor authentication (2FA)
Two-factor authentication is probably the best way to improve the security of an authentication process. It is safe to say that a properly implemented 2FA method can help you prevent a severe vulnerability in the authentication process.
What are three examples of authentication
There are three basic types of authentication. The first is knowledge-based — something like a password or PIN code that only the identified user would know. The second is property-based, meaning the user possesses an access card, key, key fob or authorized device unique to them. The third is biologically based.
What are there are three main examples of authentication
Introduction to General Security Concepts
There are three authentication factors that can be used: something you know, something you have, and something you are.
How to validate SSL certificate
How do I view an SSL certificate in Chrome or FirefoxClick the padlock icon in the address bar for the website.Click on Certificate (Valid) in the pop-up.Check the Valid from dates to validate the SSL certificate is current.
How to validate SSL certificate and key
You can verify the SSL Certificate information by comparing either with CSR or Private Key. To match SSL with CSR, select CSR file option. Now copy the encrypted data of SSL certificate & CSR & add them into their respective box and press Check button. To match SSL with Private Key, select the Private Key option.
How do you authenticate a document
Authentication involves having the documents in question notarized (a sealed certificate that confirms the authority of a public official, usually a notary public), reviewed by state or county officials, then certified by State Department officials.
How do I verify a trusted certificate
To verify that a certificate is installedOpen the Certificates console.In the navigation pane, expand Trusted Root Certification Authorities, and then click Certificates. The CA that you created appears in the list.
What are 4 ways to authenticate
Usually, authentication by a server entails the use of a user name and password. Other ways to authenticate can be through cards, retina scans, voice recognition, and fingerprints.
What are the 4 types of authentication
5 Common Authentication TypesPassword-based authentication. Passwords are the most common methods of authentication.Multi-factor authentication.Certificate-based authentication.Biometric authentication.Token-based authentication.
What are the three 3 main types of authentication techniques
There are three authentication factors that can be used: something you know, something you have, and something you are. Something you know would be a password, a PIN, or some other personal information.
What are the three requirements for authentication
The three authentication factors are:Knowledge Factor – something you know, e.g., password.Possession Factor – something you have, e.g., mobile phone.Inherence Factor – something you are, e.g., fingerprint.
What are basic authentication methods
Basic Authentication is a method for an HTTP user agent (e.g., a web browser) to provide a username and password when making a request. When employing Basic Authentication, users include an encoded string in the Authorization header of each request they make.
What is Type 3 authentication method
Type 3 – Something You Are – includes any part of the human body that can be offered for verification, such as fingerprints, palm scanning, facial recognition, retina scans, iris scans, and voice verification.
How to validate SSL certificate and private key
You can check if an SSL certificate matches a Private Key by using the 3 easy commands below.For your SSL certificate: openssl x509 –noout –modulus –in <file>.crt | openssl md5.For your RSA private key: openssl rsa –noout –modulus –in <file>.key | openssl md5.
How do I validate an SSL certificate in Chrome
Navigate to chrome://settings and scroll down to 'Advanced'.Under "Privacy and Security," click "Manage Certificates."On the popup that was launched, select "Trusted Root Certification Authorities'. The certificate will be displayed there.
How to verify SSL certificate in client side
The server authenticates the client by receiving the client's certificate during the SSL handshake and verifying the certificate is valid. Validation is done by the server the same way the client validates the server's certificate. The client sends a signed certificate to the server.
How do you verify the authenticity of a document or ID
Identity Document Verification providers may also check characteristics of a document to ensure it has not been forged or altered. This can include checking the background print, micro text, whether the document photo has been replaced, whether the fonts used are consistent and correct, and other authenticity checks.
How do you validate SSL certificate and key
You can verify the SSL Certificate information by comparing either with CSR or Private Key. To match SSL with CSR, select CSR file option. Now copy the encrypted data of SSL certificate & CSR & add them into their respective box and press Check button. To match SSL with Private Key, select the Private Key option.
How is digital certificate verified
When you send this certificate to a receiver, the receiver performs two steps to verify your identity: Uses your public key that comes with the certificate to check your digital signature. Verifies that the CA that issued your certificate is legitimate and trustworthy.