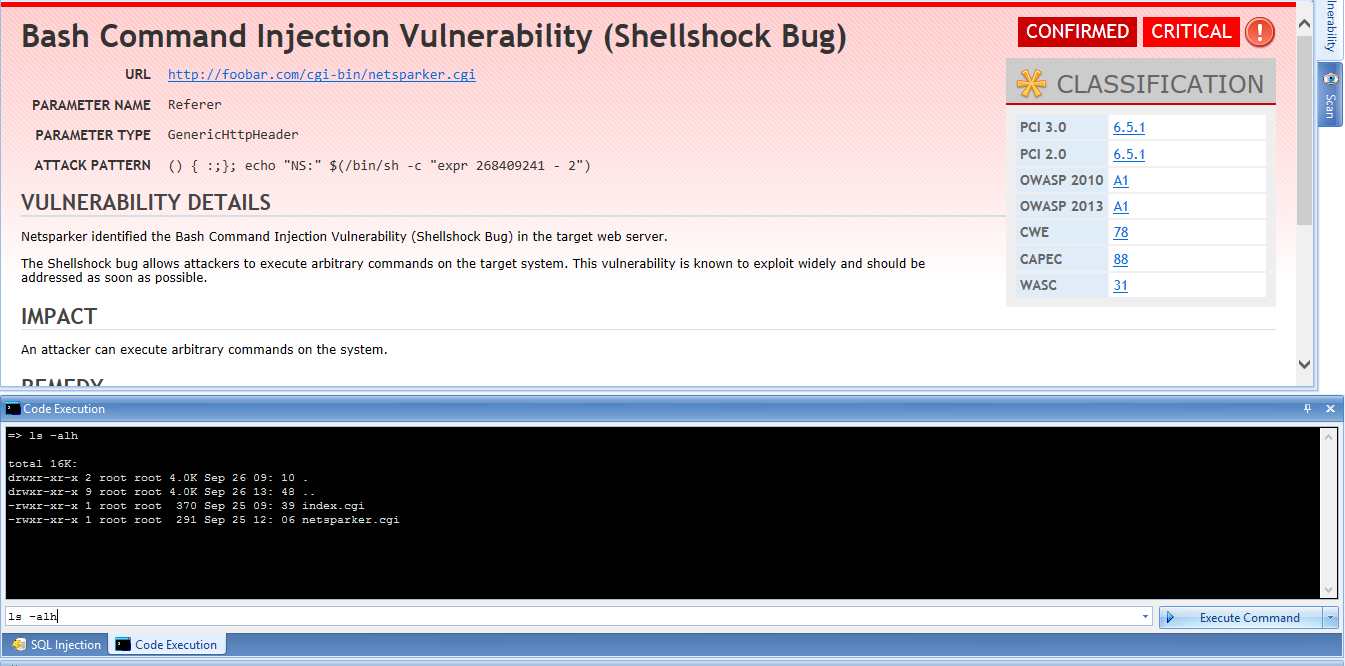
How does Nessus detect vulnerabilities
The Nessus scanning engine uses plug-ins to detect new vulnerabilities. Tenable pushes plug-ins that contain the latest information to customer systems within 24 hours after a vulnerability has gone public. Because new vulnerabilities appear nearly every day, customers receive daily plug-in feeds to stay current.
How are vulnerabilities detected
Vulnerability detection is the identification of software vulnerabilities across your systems. It identifies what the weaknesses are in the environment. These might be detected via database scans, application scans, host-based scans, and other scans.
What are the vulnerability detection methods
There are two approaches: one is detection based on static analysis of the code (source or binary), and the second is penetration testing of the system in operation. Both detection techniques involve an up-to-date and comprehensive catalog of patterns.
What are the 4 stages of identifying vulnerabilities
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.
In which testing vulnerabilities are detected
Static application security testing analyzes program source code to identify security vulnerabilities. These vulnerabilities include SQL injection, buffer overflows, XML external entity (XXE) attacks, and other OWASP Top 10 security risks.
What are the 3 detection methods
Exploring the 3 Major Threat Detection Methods: Signature, Behavior, Machine Learning.
How do you identify signs of vulnerability
Vulnerability assessment frameworkAppearance. This can include visible injuries, the state of the individual's clothing and their body language.Behaviour. This can include aggression or denial, or an individual being emotional, nervous, scared or shocked.Communication.Danger.Environment.Other factors.
How do you identify a vulnerability code
Code vulnerability is a term related to the security of your software. It is a flaw in your code that creates a potential risk of compromising security. This flaw will allow hackers to take advantage of your code by attaching an endpoint to extract data, tamper your software or worse, erase everything.
What are two methods to detect threats
3 major threat detection methods explainedSignature-based threat detection. Signature-based detection methods consist of looking for indicators – hashes, names of files, registry of key names, or strings that show up in a file – of malicious activity.Behavior-based threat detection.ML-based threat detection.Conclusion.
What are detection methods
The method detection limit (MDL) is the minimum concentration of a substance that can be measured and reported with 99% confidence that the analyte concentration is greater than zero and is determined from analysis of a sample in a given matrix containing the analyte [2].
How are vulnerabilities found
Penetration testing, also known as pen testing or ethical hacking, is the practice of testing an information technology asset to find security vulnerabilities an attacker could exploit. Penetration testing can be automated with software or performed manually.
What is the threat detection process
Threat detection is the process of analyzing a security ecosystem at the holistic level to find malicious users, abnormal activity and anything that could compromise a network. Threat detection is built on threat intelligence, which involves tools that are strategic, tactical and operational.
What is the method of vulnerability detection
There are two approaches: one is detection based on static analysis of the code (source or binary), and the second is penetration testing of the system in operation. Both detection techniques involve an up-to-date and comprehensive catalog of patterns.
What are the 5 steps of threat modeling
There are five major threat modeling steps:Defining security requirements.Creating an application diagram.Identifying threats.Mitigating threats.Validating that threats have been mitigated.
What are the 4 stages of threat modeling
The threat modelling process typically consists of four steps – identify assets, identify threats, analyse vulnerabilities, and create countermeasures or safeguards to protect against identified risks.
What are the 4 main types of vulnerability in disaster
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
What are the 4 stages of threat analysis
The threat modelling process typically consists of four steps – identify assets, identify threats, analyse vulnerabilities, and create countermeasures or safeguards to protect against identified risks.
What are the 6 steps of threat modeling
How Threat Modeling Protects Your Data AssetsStep 1: Asset Identification. Your first task is to catalog your assets, including data, applications, network components, and many others.Step 2: Attack Surface Analysis.Step 3: Attack Vectors.Step 4: Analysis.Step 5: Prioritization.Step 6: Security Controls.
What is threat modeling and vulnerability identification
Threat modeling is a structured process with these objectives: identify security requirements, pinpoint security threats and potential vulnerabilities, quantify threat and vulnerability criticality, and prioritize remediation methods. Threat modeling methods create these artifacts: An abstraction of the system.
How is vulnerability determined
Physical Vulnerability may be determined by aspects such as population density levels, remoteness of a settlement, the site, design and materials used for critical infrastructure and for housing (UNISDR). Example: Wooden homes are less likely to collapse in an earthquake, but are more vulnerable to fire.
What are the 6 phases of threat intelligence
The Threat Intelligence Lifecycle consists of 6 phases: requirements Identification, collection, processing, analysis, dissemination, and feedback.
What are the 4 threat modeling steps
Step 1: diagram the application. In this step, you gain a comprehensive understanding of the mechanics of your application.Step 2: identify threats with STRIDE.Step 3: mitigate identified vulnerabilities.Step 4: validate.
What is vulnerability identification
Vulnerability identification (testing)
Security analysts test the security health of applications, servers or other systems by scanning them with automated tools, or testing and evaluating them manually.
What is threat modeling used to detect
Identifying the Differences in Threat Modeling Methodologies
Threat modeling identifies threats by focusing on potential attacks, system assets or the software itself. Asset-centric threat modeling focuses on system assets and the business impact of the loss of each targeted asset.
How is vulnerability measured in disaster management
Physical Vulnerability may be determined by aspects such as population density levels, remoteness of a settlement, the site, design and materials used for critical infrastructure and for housing (UNISDR). Example: Wooden homes are less likely to collapse in an earthquake, but are more vulnerable to fire.