Is CVE a vulnerability database
CVE stands for Common Vulnerabilities and Exposures. CVE is a free service that identifies and catalogs known software or firmware vulnerabilities. CVE is not, in itself, an actionable vulnerability database. It is, in effect, a standardized dictionary of publicly known vulnerabilities and exposures.
What is the difference between CVE and vulnerability
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
How does CVE compare to CVSS
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
What is the difference between CVE and CWE
While both standards play a critical role in secure software development, they have different purposes. In summary, CVE is a standard for identifying and naming specific vulnerabilities, while CWE is a standard for classifying and describing the types of weaknesses that can lead to vulnerabilities.
What is a CVE equivalent
Definition(s): A vulnerability—known by someone—that has been found in specific software—irrespective of whether that vulnerability is publicly known. CVEs are a subset of CVE equivalents.
What is vulnerability databases in cyber security
Vulnerability Databases
The vulnerability database is the result of an effort to collect information about all known security flaws in software.
How does a vulnerability become a CVE
The reporter requests a CVE ID, which is then reserved for the reported vulnerability. Once the reported vulnerability is confirmed by the identification of the minimum required data elements for a CVE Record, the record is published to the CVE List.
What type of vulnerability is CVE
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that's been assigned a CVE ID number. Security advisories issued by vendors and researchers almost always mention at least one CVE ID.
What are the CVE and CWE databases
In other words, CVE is a list of known instances of vulnerability for specific products or systems, while CWE acts as a dictionary (so to speak) of software vulnerability types. The National Vulnerability Database (NVD) actually uses CWEs to score CVEs.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What is CCE vs CVE
CVE provides this capability for information security vulnerabilities, CCE assigns a unique, common identifier to a particular security-related configuration issue. The name of the imported file. The type of the list, that is, if it is a CVE or CCE list.
Who creates a CVE for vulnerability
The Mitre Corporation
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
Who maintains the CVE database
the MITRE corporation
Founded in 1999, the CVE program is maintained by the MITRE corporation and sponsored by the U.S. Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA).
What are the 4 main types of security vulnerability
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
Who maintains CVE database
the MITRE corporation
Founded in 1999, the CVE program is maintained by the MITRE corporation and sponsored by the U.S. Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA).
What are the two main databases used for storing vulnerability information
Major vulnerability databases such as the ISS X-Force database, Symantec / SecurityFocus BID database, and the Open Source Vulnerability Database (OSVDB) aggregate a broad range of publicly disclosed vulnerabilities, including Common Vulnerabilities and Exposures (CVE).
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 4 stages of identifying vulnerabilities
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.
What is a CCE database
Common Configuration Enumeration (CCE) provides unique identifiers to system configuration issues in order to facilitate fast and accurate correlation of configuration data across multiple information sources and tools.
What is the difference between CVS and CVE
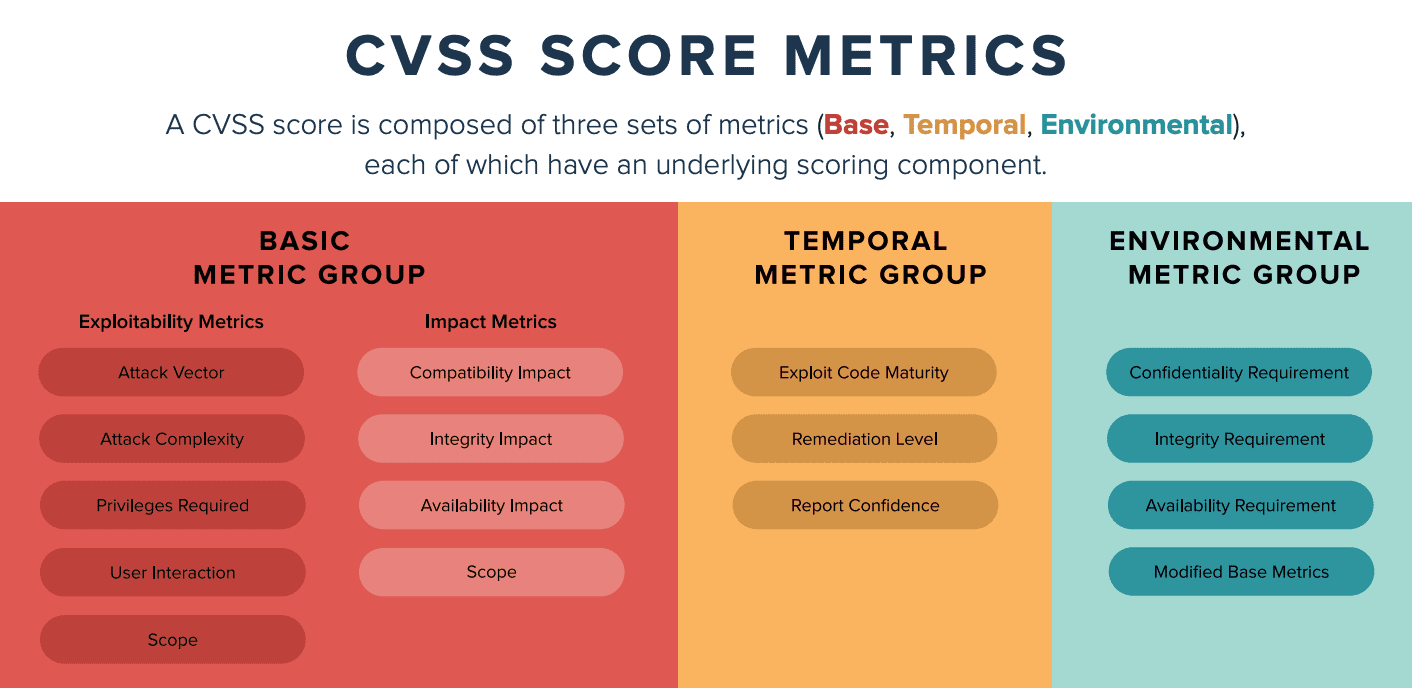
Differences between CVSS and CVE
CVSS is the total score assigned to a vulnerability while CVE is a list of all publicly disclosed vulnerabilities that include the CVE ID, dates, comments and description. The CVSS score is not reported in the CVE listing. You must use the NVD to find assigned CVSS scores.
What does a CVE database provide security researchers
CVE does this by creating a standardized identifier for a given vulnerability or exposure. CVE identifiers (also called CVE names or CVE numbers) allow security professionals to access information about specific cyber threats across multiple information sources using the same common name.
Which database is the CVE currently listed in
Note: The U.S. National Vulnerability Database (NVD) provides fix and other information for records on the CVE List.
What are the three common categories of vulnerabilities
At the broadest level, network vulnerabilities fall into three categories: hardware-based, software-based, and human-based.
What is a vulnerability database
A vulnerability database (VDB) is a platform aimed at collecting, maintaining, and disseminating information about discovered computer security vulnerabilities.
What are the 4 pillars of vulnerability
In there, we argue that there is a connection between vulnerability, empathy, integrity and adaptability (the 4 Pillars) and authentic leadership for trustful working environments.