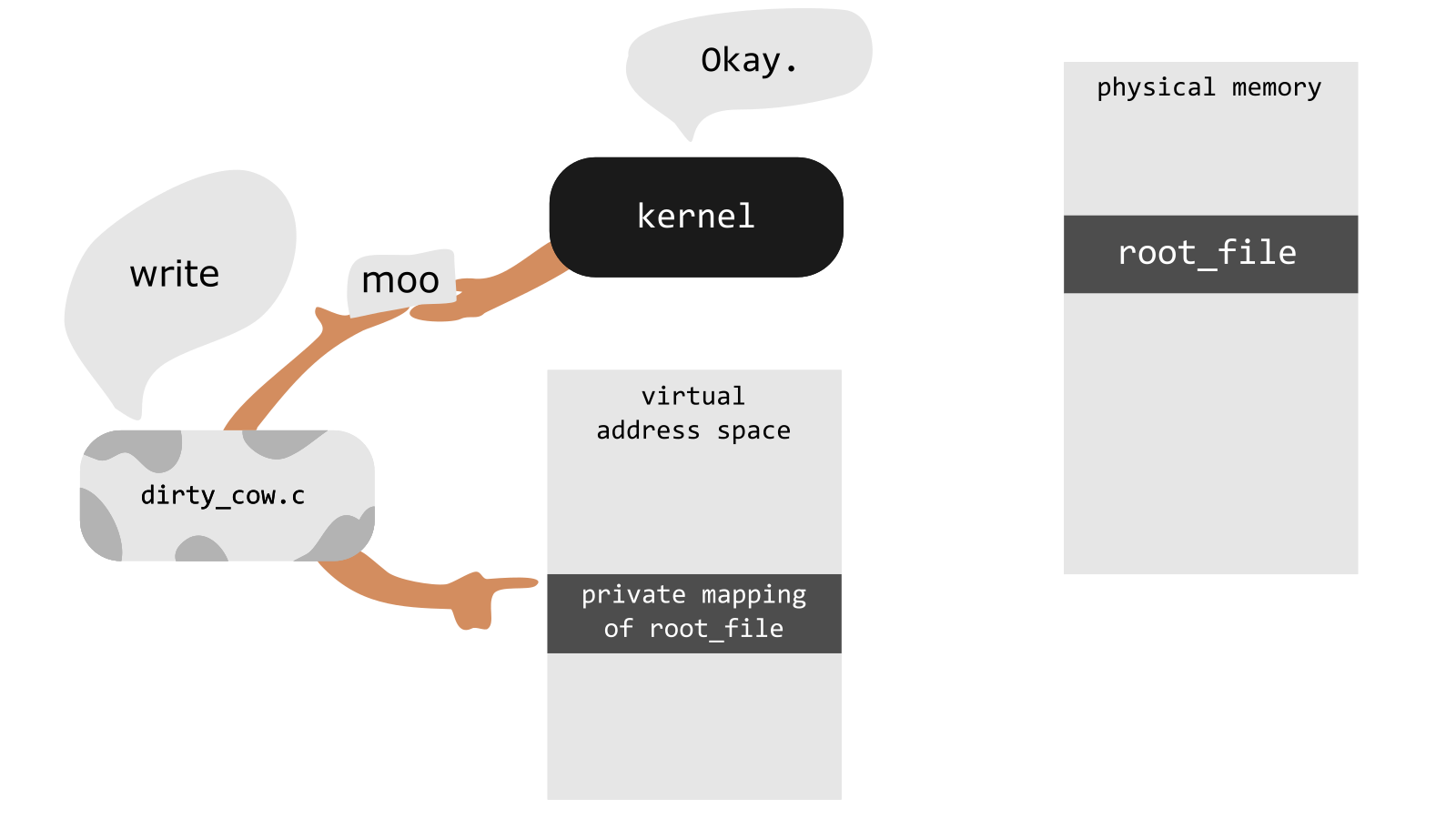
How does the Dirty COW exploit work
Dirty COW was a vulnerability in the Linux kernel. It allowed processes to write to read-only files. This exploit made use of a race condition that lived inside the kernel functions which handle the copy-on-write (COW) feature of memory mappings.
What is the cause of Dirty COW vulnerability
The Dirty COW vulnerability is a privilege escalation vulnerability, and it is caused by a race condition found in the way the Linux kernel's memory subsystem handles the copy-on-write breakage of private, read-only memory mappings.
What is Dirty COW in cyber security
Dirty COW, officially known as "CVE-2016-5195", is a privilege escalation vulnerability found in the Linux Kernel. It is defined as "a race condition that was found in the Linux kernel's memory subsystem handled the copy-on-write (COW) breakage of private read-only memory mappings"
What is the CVE for Dirty COW
Dirty COW (CVE-2016-5195)
Why is it called Dirty COW
Untrusted users can exploit it to gain highly privileged write-access rights to memory mappings that would normally be read-only. More technical details about the vulnerability and exploit are available below. Using the acronym derived from 'copy-onwrite', some researchers have dubbed the vulnerability 'Dirty COW'.
What is dirty pipe vulnerability
Dirty Pipe vulnerability is a Linux kernel vulnerability that allows the ability of non-privileged users to overwrite read-only files.
What is Dirty COW exploit CVE 2016 5195
CVE-2016-5195 Detail
c in the Linux kernel 2. x through 4. x before 4.8. 3 allows local users to gain privileges by leveraging incorrect handling of a copy-on-write (COW) feature to write to a read-only memory mapping, as exploited in the wild in October 2016, aka "Dirty COW."
How does dirty pipe works
The Dirty Pipe exploit allows apps to manipulate Linux pipes so that the application can insert its data into a page of memory. This makes it easy for the attacker to either replace the contents of a file that the user is trying to access or even get full control of the user's system.
What is the difference between dirty pipe and dirty cow
Dirty Pipe and Dirty COW, the differences
What makes this vulnerability even more risky is the ease with which it can be exploited. In fact, Max Kellermann compared the Dirty Pipe vulnerability to CVE-2016-5195, better known as Dirty COW, specifying that Dirty Pipe is easier to exploit.
What does CVE mean in exploit
Common Vulnerabilities and Exposures (CVE) is a database of publicly disclosed information security issues. A CVE number uniquely identifies one vulnerability from the list.
What is win exploit CVE 2017
Win/Exploit. CVE-2017-11882 is an exploit – it is designed to abuse a vulnerability in Microsoft Office programs to infect the device with malware. The infiltrated malicious program could be a trojan, ransomware, cryptominer, or a different type.
What is a dirty pipe vulnerability
The Dirty Pipe exploit allows apps to manipulate Linux pipes so that the application can insert its data into a page of memory. This makes it easy for the attacker to either replace the contents of a file that the user is trying to access or even get full control of the user's system.
What is the dirty pipe vulnerability
Dirty Pipe vulnerability is a Linux kernel vulnerability that allows the ability of non-privileged users to overwrite read-only files.
What is the impact of dirty pipe
Dirty Pipe danger to containers
According to McCune, the Dirty Pipe exploit allows attackers to violate that security guarantee because they can make changes to the base image from inside a container. This will impact all other containers that are started from the same image.
How is CVE score calculated
CVSS scores are calculated using a formula consisting of vulnerability-based metrics. A CVSS score is derived from scores in these three groups: Base, Temporal and Environmental. Scores range from zero to 10, with zero representing the least severe and 10 representing the most severe.
Do all vulnerabilities have a CVE
CVE stands for Common Vulnerabilities and Exposures. It is the database of publicly disclosed information on security issues. All organizations use CVEs to identify and track the number of vulnerabilities. But not all the vulnerabilities discovered have a CVE number.
How does CVE 2017 0144 work
An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server. To exploit the vulnerability, in most situations, an authenticated attacker could send a specially crafted packet to a targeted SMBv1 server.
What is CVE 2017 11882 exploit malware was detected
CVE-2017-11882 is an exploit – it is designed to abuse a vulnerability in Microsoft Office programs to infect the device with malware. The infiltrated malicious program could be a trojan, ransomware, cryptominer, or a different type.
Am I vulnerable to dirty pipe
The easiest way to check whether your system is vulnerable is to see which version of the Linux kernel it uses by running the command uname -r . A system is likely to be vulnerable if it has a kernel version higher than 5.8, but lower than 5.16.
How do you calculate vulnerability risk
Risk = threat x vulnerability
We can sum up this calculation with the concepts from above: that a single vulnerability multiplied by the potential threat (frequency, existing safeguards, and potential value loss) can give you an estimate of the risk involved.
How does CVE scan work
Systems identify and highlight vulnerabilities, using data contained in the CVE database and other databases of known anomalies. Prioritization. Based on metrics programmed into the scanner, network devices use CVE data, threat intelligence and data science to assess issues and prioritize them for remediation.
What is the difference between CVE and vulnerability
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
Who creates a CVE for vulnerability
The Mitre Corporation
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
How does CVE 2017 0199 work
The CVE-2017-0199 vulnerability is a logic bug and bypasses most mitigations. Upon execution of the malicious script, it downloads and executes malicious payloads, as well as displays decoy documents to the user.
What attacks was CVE-2017-0144 used in
WannaCry leverages CVE-2017-0144, a vulnerability in Microsoft Server Message Block 1.0 (SMBv1), to infect computers. The security flaw is attacked using an exploit leaked by the Shadow Brokers group—the “EternalBlue” exploit, in particular.