How are digital certificates validated
To validate the digital signature person authenticating the certificate will take the message of the certificate and then uses the same hash algorithm. If the two hashes match then the digital signature is valid and the certificate is authenticated.
How the digital certificate signature is verified
Verifying a signature will tell you if the signed data has changed or not. When a digital signature is verified, the signature is decrypted using the public key to produce the original hash value. The data that was signed is hashed. If the two hash values match, then the signature has been verified.
How can a digital certificate verify that a site is authentic
A digital certificate is a file or electronic password that proves the authenticity of a device, server, or user through the use of cryptography and the public key infrastructure (PKI). Digital certificate authentication helps organizations ensure that only trusted devices and users can connect to their networks.
What is digital signature certificate and how it can be authenticated and validated
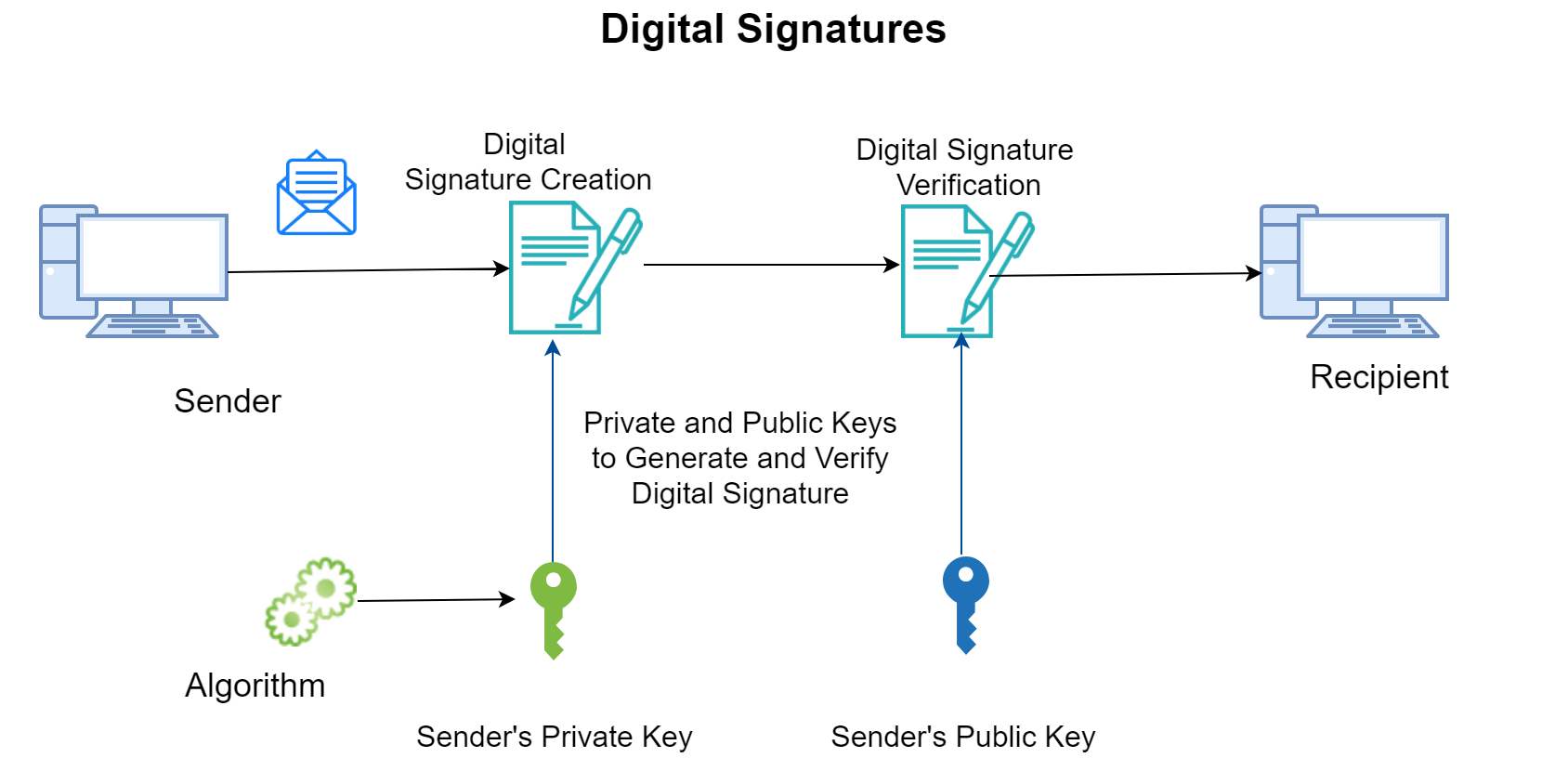
A digital signature provides proof of the message origin and a method to verify the integrity of the message. A digital certificate owner combines the data to be signed with their private key, and then transforms the data with an algorithm.
Who verifies digital certificates
certificate authorities
Digital certificates are issued by trusted parties, called certificate authorities, to verify the identity of an entity, such as a client or server. The digital certificate serves two purposes: it verifies the owner's identity and it makes the owner's public key available.
How do I verify a certificate
Chrome has made it simple for any site visitor to get certificate information with just a few clicks:Click the padlock icon in the address bar for the website.Click on Certificate (Valid) in the pop-up.Check the Valid from dates to validate the SSL certificate is current.
How is digital signature validated and secured
When a signer electronically signs a document, the signature is created using the signer's private key, which is always securely kept by the signer. The mathematical algorithm acts like a cipher, creating data matching the signed document, called a hash, and encrypting that data.
How can you verify the originality of the certificates
It is highly recommended to take a look at samples for certificates issued by the given institution to verify if they are original or photocopied and be sure that most of the genuine educational institutions will have some physical authentication features such as micro-text lines, UV invisible ink, watermark, security …
How do you authenticate a certificate
Authentication Certificate Requirements Notarize each document in front of a notary public: Using a notary commissioned by the county All seals and signatures must be originals. All documents in a foreign language must be translated into English by a certified translator and notarized as a true translation.
How does certificate authority verify identity
How do certification authorities workValidation: Some companies use email to verify identity.Generation: You'll generate a cryptographic set of keys, one public and one private.Verification: The company will check your paperwork and keys.Stored: You'll place your certificate and the proper keys on your website.
Who generates a digital certificate
Certificate Authorities
Digital certificates facilitate secure electronic communication and data exchange between people, systems, and devices online. They are issued by Certificate Authorities (CAs) and perform two primary functions: Verifying the identity of the sender/receiver of an electronic message.
What is certificate verification system
Certificate verification system is a system designed to computerize the process of adding certificates and verifying the certificates records considering the problems faced by doing this manually.
What key is required to verify digital signature
public key
In the case of digital signatures, the public key is used to verify a digital signature that was signed using the corresponding private key.
Does digital signature provide authenticity
Digital signatures provide authenticity protection, integrity protection, and non-repudiation, but not confidentiality protection. The result of a cryptographic transformation of data that, when properly implemented, provides origin authentication, assurance of data integrity and signatory non-repudiation.
Can you verify the authenticity of a certificate
You can also contact the provider or the issuer to confirm the authenticity of the certificate, or use online tools or platforms that allow you to verify certificates digitally. Finally, you can ask for feedback or recommendations from other learners, employers, or experts who have taken or accepted the certificate.
How do you verify the authenticity of a document or ID
Identity Document Verification providers may also check characteristics of a document to ensure it has not been forged or altered. This can include checking the background print, micro text, whether the document photo has been replaced, whether the fonts used are consistent and correct, and other authenticity checks.
What are 4 ways to authenticate
Usually, authentication by a server entails the use of a user name and password. Other ways to authenticate can be through cards, retina scans, voice recognition, and fingerprints.
How do certificates of authenticity work
A Certificate of authenticity is an official document that proves that the artwork sold is genuine and authentic. It includes technical details of the artwork and is signed by the artist.
How are certificates checked
The signature on the certificate can be verified using normal public key cryptography. If the signature is invalid, then the certificate is considered to be modified after its issuance and is therefore rejected.
How are certificate authorities authenticated
The CA's certificates are signed by another CA. Each CA is authenticated using its certificate and trust rolls up to a root CA that uses self-signed certificates and is, therefore, the root-of-trust.
How are digital certificates generated
You usually start by generating a private key / public key pair, followed by a CSR (Certificate Signing Request). The CSR would contain a copy of the public key and some basic information about the subject. Once you've generated a CSR, you would then submit that CSR to a CA.
What is needed to verify a certificate
To verify a certificate, a browser will obtain a sequence of certificates, each one having signed the next certificate in the sequence, connecting the signing CA's root to the server's certificate. This sequence of certificates is called a certification path.
What are the five 5 requirements of digital signature
Digital signature software requirements or principles include authentication, integrity, non-repudiation, and confidentiality. All of which ensure security and would be easily compromisable with wet signatures.
Which key is used to verify the certificate
A self-signed certificate is a certificate that is signed by the same entity to whom it is assigned. Most certificates can be self-signed and are verified by their own public key.
How do they authenticate signatures
Autograph Authentication Process
PSA authenticators conduct ink analysis, autograph structure analysis, object evaluation and side-by-side comparisons. Authenticators may also use a video spectral comparator to further evaluate the autograph.