How many CVEs are there total
NVD Contains
| CVE Vulnerabilities | 220290 |
|---|---|
| Checklists | 614 |
| US-CERT Alerts | 249 |
| US-CERT Vuln Notes | 4486 |
| OVAL Queries | 10286 |
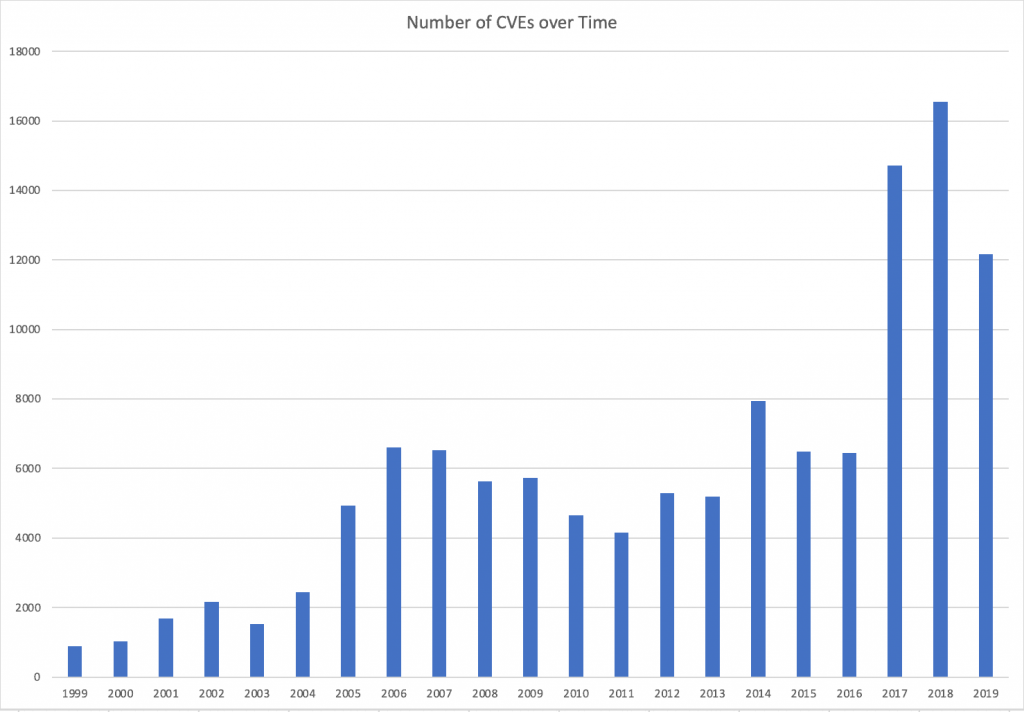
How many CVEs are there a year
Can you guess the product with the most CVEs in 2022 A record 26,448 software security flaws were reported in 2022, with the number of critical vulnerabilities up 59% on 2021 to 4,135, according to analysis by The Stack of Common Vulnerabilities and Exposures (CVEs) data.
What is the CVE list
CVE® is a list of publicly disclosed cybersecurity vulnerabilities that is free to search, use, and incorporate into products and services, per the terms of use. The CVE List is built by CVE Numbering Authorities (CNAs). Every CVE Record added to the list is assigned and published by a CNA.
What is the most common CVE
CVE-2022-22965: The most popular CVE reported in 2022 (also known as Spring4Shell) is an extremely high-impact Injection vulnerability in Spring Framework that allows attackers to make changes remotely to a target system.
Do all vulnerabilities have a CVE
CVE stands for Common Vulnerabilities and Exposures. It is the database of publicly disclosed information on security issues. All organizations use CVEs to identify and track the number of vulnerabilities. But not all the vulnerabilities discovered have a CVE number.
What is CVEs vs CVSS
Differences between CVSS and CVE
CVSS is the overall score assigned to a vulnerability. CVE is simply a list of all publicly disclosed vulnerabilities that includes the CVE ID, a description, dates, and comments. The CVSS score is not reported in the CVE listing – you must use the NVD to find assigned CVSS scores.
Does every vulnerability have a CVE
In simple terms, we can state that 'All CVEs are vulnerabilities, but not all vulnerabilities have CVEs.
Who creates CVEs
MITRE
CVE IDs are primarily assigned by MITRE, as well as by authorized organizations known as CVE Numbering Authorities (CNAs)—an international group of vendors and researchers from numerous countries.
Do hackers use CVE
Can Hackers Use CVE to Attack My Organization The short answer is yes but many cybersecurity professionals believe the benefits of CVE outweigh the risks: CVE is restricted to publicly known vulnerabilities and exposures.
Are CVE numbers unique
A CVE ID is a unique, alphanumeric identifier assigned by the CVE Program. Each identifier references a specific vulnerability. The “Year” portion is the year that the CVE ID was reserved or the year the vulnerability was made public. The year portion is not used to indicate when the vulnerability was discovered.
Does CVE use CVSS
CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
What is the first CVE
The very first CVE List contained 321 vulnerabilities, chosen after careful deliberation and consideration of duplicates. In September 1999, the first CVE List was made public.
Who controls CVEs
the MITRE corporation
Founded in 1999, the CVE program is maintained by the MITRE corporation and sponsored by the U.S. Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA).
Who controls CVE
The Mitre Corporation
The Mitre Corporation functions as Editor and Primary CNA. Various CNAs assign CVE numbers for their own products (e.g. Microsoft, Oracle, HP, Red Hat, etc.) A third-party coordinator such as CERT Coordination Center may assign CVE numbers for products not covered by other CNAs.
What is CVSS vs CVE
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
Who invented CVE
Overview. The original concept for what would become the CVE List was presented by the co-creators of CVE, The MITRE Corporation's David E. Mann and Steven M.
Are CVEs public
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed information security vulnerabilities and exposures.
What is CVSS and CVSS v3
CVSS is composed of three metric groups, Base, Temporal, and Environmental, each consisting of a set of metrics, as shown in Figure 1. Figure 1: CVSS v3.0 Metric Groups. The Base metric group represents the intrinsic characteristics of a vulnerability that are constant over time and across user environments.
What is the very first CVE
The very first CVE List contained 321 vulnerabilities, chosen after careful deliberation and consideration of duplicates. In September 1999, the first CVE List was made public.
Should I use CVSS v2 or v3
Cisco conducted a study on this topic and found that the average base score increased from 6.5 in CVSSv2 to 7.4 in CVSSv3. This means that the average vulnerability increased in qualitative severity from “Medium” to “High.” The same study concluded that far more vulnerabilities increased in severity than decreased.
Is CVSS the same as CVE
Differences between CVSS and CVE
CVSS is the overall score assigned to a vulnerability. CVE is simply a list of all publicly disclosed vulnerabilities that includes the CVE ID, a description, dates, and comments. The CVSS score is not reported in the CVE listing – you must use the NVD to find assigned CVSS scores.
When was CVSS 3.1 released
June 17, 2019
Version 3.1
A minor update to CVSS was released on June 17, 2019.
What is Cves vs CVSS
Differences between CVSS and CVE
CVSS is the overall score assigned to a vulnerability. CVE is simply a list of all publicly disclosed vulnerabilities that includes the CVE ID, a description, dates, and comments. The CVSS score is not reported in the CVE listing – you must use the NVD to find assigned CVSS scores.
What is CWE vs CVE
Whereas the CVE logs real-world instances of vulnerabilities and exposures in specific products, the CWE lists and defines weaknesses commonly seen in digital products. The CWE does not refer to one particular example but provides definitions for widely seen defects.