What are the 3 types of scanning in cyber security
Scanning could be basically of three types:Port Scanning – Detecting open ports and running services on the target host.Network Scanning – Discovering IP addresses, operating systems, topology, etc.Vulnerability Scanning – Scanning to gather information about known vulnerabilities in a target.
What is scanning in cyber security
What is scanning Scanning can be considered a logical extension (and overlap) of active reconnaissance that helps attackers identify specific vulnerabilities. It's often that attackers use automated tools such as network scanners and war dialers to locate systems and attempt to discover vulnerabilities.
How many types of information is available in cyber security
Cybersecurity can be categorized into five distinct types: Critical infrastructure security. Application security. Network security.
What are the phases of scanning
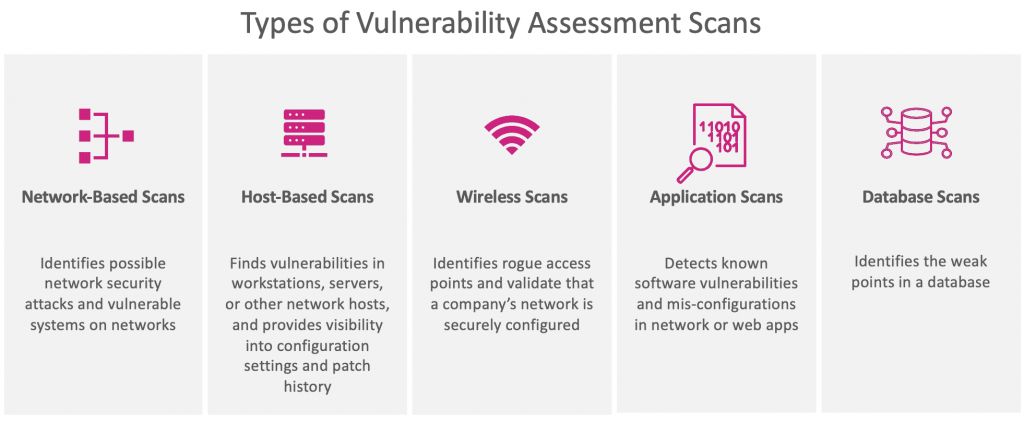
Scanning
There are three methods of scanning: pre-attack, port scanning/sniffing, and information extraction. Each of these phases demonstrates a specific set of vulnerabilities that the hacker can utilize to exploit the system's weaknesses.
What are the 4 modes of scanning
There are four modes of scanning that can be used by companies, depending on their beliefs and philosophy of operations:Searching.Enacting.Conditioned viewing.Undirected viewing.
What are the 3 levels of scanning
There are three major categories or levels of scanning: patient, encounter and order level.
How many types of scanning are there in cyber security Mcq
Explanation: The vulnerability, port, and network scanning are three types of scanning.
What are the 7 types of cyber security
It can be divided into seven main pillars:Network Security. Most attacks occur over the network, and network security solutions are designed to identify and block these attacks.Cloud Security.Endpoint Security.Mobile Security.IoT Security.Application Security.Zero Trust.
What are the 4 types of information security
There are four types of information technology security you should consider or improve upon:Network Security.Cloud Security.Application Security.Internet of Things Security.
What are the 4 different types of scans
This includes X-rays, a CT scan, an MRI scan and ultrasound scans.Angiography. Information on angiograms, a type of X-ray used to examine blood vessels.CT scan. Learn about CT scans and when they're used.Echocardiogram.Electrocardiogram (ECG)MRI scan.PET scan.Ultrasound scan.X-ray.
How many types of scanning do we have
Today's most cutting-edge imaging techniques include X-rays, CT scans, PET scans, ultrasounds, and MRIs. But where do you begin To start with, each radiology technique or modality is unique in terms of the images it gathers, equipment it uses, and tissue changes it may help find.
How many types of scanning are there
This includes X-rays, a CT scan, an MRI scan and ultrasound scans.
What are the 5 types of cyber security
The 5 Types of Cybersecurity and What You Need to KnowCritical infrastructure security.Application security.Network security.Cloud security.Internet of Things (IoT) security.
What are the 4 security types
Types#1 – Equity securities. It refers to a stock – common or preferred, held by investors, who are referred to as equity shareholders.#2 – Debt securities. Debt instruments are a type of loan that carries a low risk.#3 – Hybrid securities.#4 – Derivatives.Example #1.Example #2.
What are the 3 types of security
There are three primary areas or classifications of security controls. These include management security, operational security, and physical security controls.
What are the 4 steps of security
The unpredictability of modern threats is causing security professionals to re-assess their approach to site protection.
What are the 5 types of scanner
Types of ScannerFlatbed Scanners. The most popular type of optical scanner is a flatbed scanner, which scans documents on a flat surface.Sheetfed Scanners. A scanner that allows the only paper to be scanned, known as sheetfed scanners.Handheld Scanner.Drum Scanner.Photo Scanner.Film Scanner.Portable Scanners.
What are the 7 stages of cyber security
7 stages of the cyber attack lifecycleReconnaissance. The preliminary stage of any cyber attack sees the threat actor gathering intelligence and research on their target(s).Weaponisation.Delivery.Exploitation.Installation.Command and control.Actions on objectives.
What are the 4 main types of security vulnerability
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What are the 4 forms of security
4 Forms Of Best SecurityPrevention. The best police in the world are effective solely because they prevent crimes before it actually happens.Add a Security System. A security system can work wonders to help enhance your security at home or at the office.Hire a Security Guard.Personal Security.
What are 3 security concepts
Three basic security concepts important to information on the internet are confidentiality, integrity, and availability. Concepts relating to the people who use that information are authentication, authorization, and nonrepudiation.
What are 4 examples of scanning devices
Below I have listed 8 types of scanner in computer they areDrum Scanner.Handheld Scanner.Flatbed Scanner.Optical Character Recognition.Magnetic Ink Character Recognition.Image Scanner.Light Pen.Barcode Reader.
What are the 4 parts of a scanner
| Item | Purpose | |
|---|---|---|
| 1. | Stepper Motor | Powers the transmission belt |
| 2. | Logic Board | Relays information to and from the scanner and the computer |
| 3. | Scanning Unit/Carriage | Contains a light source and CCD sensors |
| 4. | Transmission Belt | Moves the scanning unit across the image |
What are the 5 stages of cyber security
Phases of the Cybersecurity Lifecycle. As defined by the National Insitute of Standards and Technology (NIST), the Cybersecurity Framework's five Functions: Identify, Protect, Detect, Respond, and Recover, are built upon the components of the framework model.
What are the 4 levels of security
The best way to keep thieves at bay is to break down security into four layers: deterrence, access control, detection and identification.