What are the measures of vulnerability
Prevalent Vulnerability Index (PVI) that measures three tangible social-related vulnerability aspects: hazard exposure and physical susceptibility, socioeconomic fragility, and resilience. Risk Management Index (RMI) that measures institutional and community performance on disaster risk management.
What are the 4 levels of vulnerability
The four continuous stages of identification, prioritization, remediation, and reporting are essential for an effective vulnerability management process. A vulnerability is a flaw or weakness in a system that, if exploited, would allow a user to gain unauthorized access to conduct an attack.
What are the 4 dimensions of vulnerability
To ensure better alignment between vulnerability and risk management, we must consider four critical dimensions: severity, exploitability, context and controls.
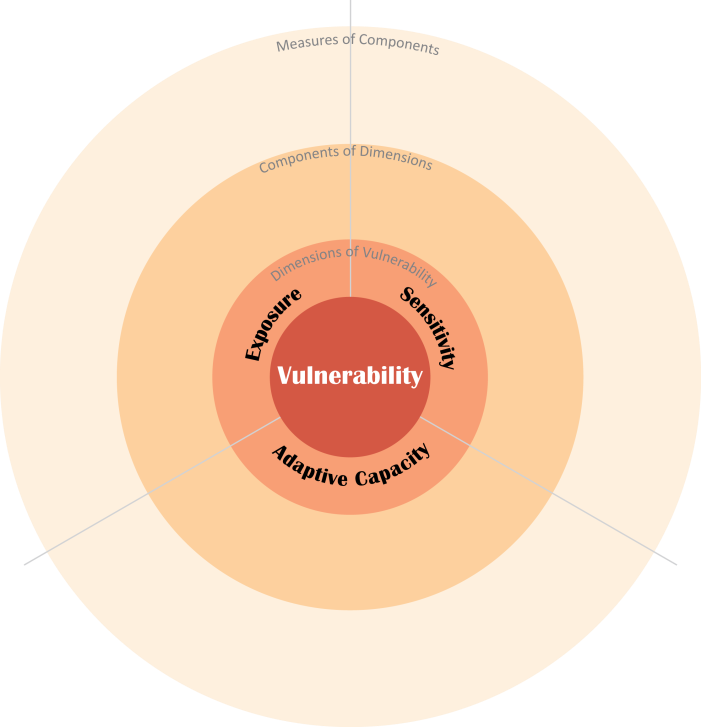
What are the 3 components of vulnerability assessment
There are three dimensions of vulnerability: exposure, sensitivity, and adaptive capacity.
What are the 4 steps in vulnerability assessment
With the right tools in hand, you can perform a vulnerability assessment by working through the following steps:Asset discovery. First, you need to decide what you want to scan, which isn't always as simple as it sounds.Prioritization.Vulnerability scanning.Result analysis & remediation.Continuous cyber security.
What are the 3 criteria for assessing vulnerability
The assessment framework involves three dimensions: engagement, intent and capability, which are considered separately.
What are the 4 pillars of vulnerability
In there, we argue that there is a connection between vulnerability, empathy, integrity and adaptability (the 4 Pillars) and authentic leadership for trustful working environments.
What are the 4 factors of vulnerability
There are many aspects of vulnerability, arising from various physical, social, economic, and environmental factors.
What are the 3 points of vulnerability
Vulnerability is a weakness which allows an attacker to reduce a system's information assurance. Vulnerability is the intersection of three elements : a system susceptibility or defect, attacker access to the defect, and attacker capability to exploit the defect.