Does Log4j 1.2 17 have vulnerability
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
What version of Log4j is not vulnerable
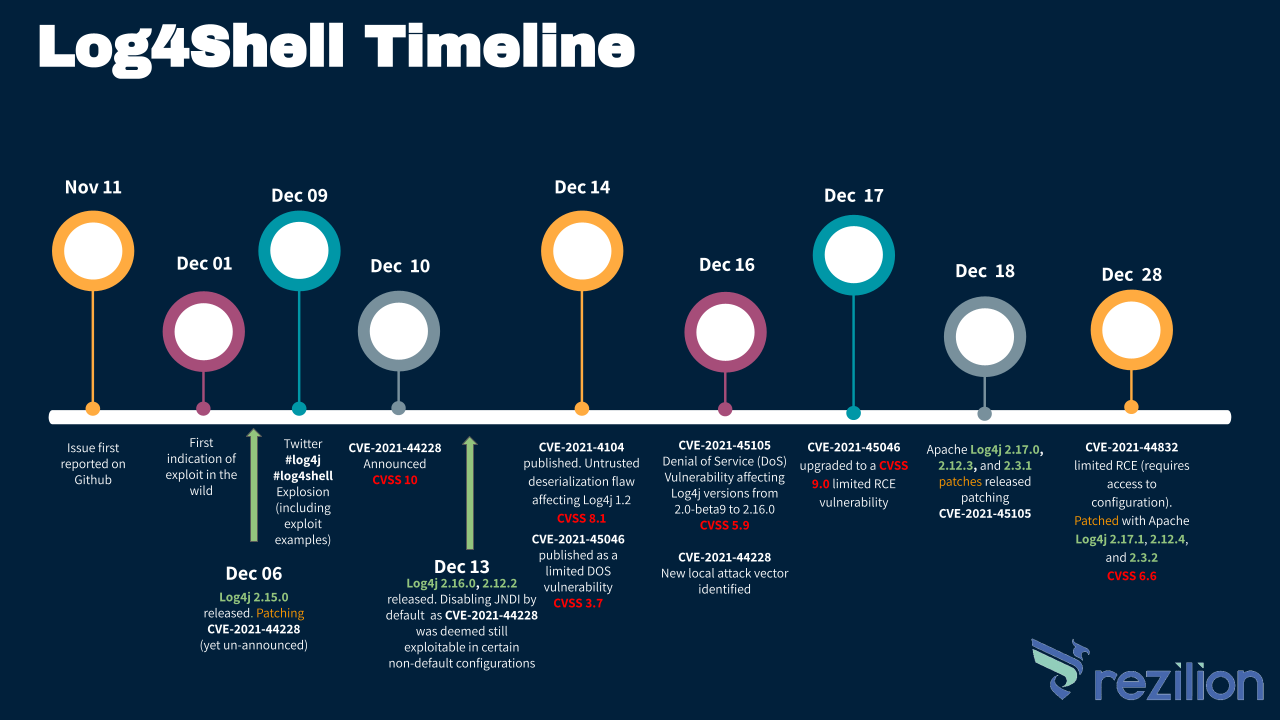
Log4j 1. x is not impacted by this vulnerability. Implement one of the following mitigation techniques: Java 8 (or later) users should upgrade to release 2.16.
What is the vulnerability of Log4j 1.2 12
Affected versions of this package are vulnerable to Man-in-the-Middle (MitM). Improper validation of certificate with host mismatch in Apache Log4j SMTP appender. This could allow an SMTPS connection to be intercepted by a man-in-the-middle attack which could leak any log messages sent through that appender.
What is the safe version of Log4j
x, the best advice us to use the most recent version. At the time of writing this (2021-03-14), https://logging.apache.org/log4j/2.x/security.html says that log4j 2.3. 2 is safe if you are running the code on a Java 6 JVM. But if you intend to run on a more recent JVM, the latest security patch is advisable.
Is Log4j 1 affected
Applications using Log4j 1.x are only vulnerable to this attack when they use JNDI in their configuration. A separate CVE (CVE-2021-4104) has been filed for this vulnerability. To mitigate: Audit your logging configuration to ensure it has no JMSAppender configured.
Is Log4j 1 affected by vulnerability
JMSSink in Log4j 1. x is vulnerable to deserialization of untrusted data. This flaw allows a remote attacker to execute code on the server if the deployed application is configured to use JMSSink and to the attacker's JNDI LDAP endpoint.
Is log4j 1 version vulnerable
x. JMSSink in Log4j 1. x is vulnerable to deserialization of untrusted data. This flaw allows a remote attacker to execute code on the server if the deployed application is configured to use JMSSink and to the attacker's JNDI LDAP endpoint.
Is log4j 1 vulnerable
Applications using Log4j 1. x are only vulnerable to this attack when they use JNDI in their configuration. A separate CVE (CVE-2021-4104) has been filed for this vulnerability. To mitigate: Audit your logging configuration to ensure it has no JMSAppender configured.
Is Log4j version 1 safe
Applications using Log4j 1. x are only vulnerable to this attack when they use JNDI in their configuration. A separate CVE (CVE-2021-4104) has been filed for this vulnerability. To mitigate: Audit your logging configuration to ensure it has no JMSAppender configured.
Is Log4j 1 version vulnerable
x. JMSSink in Log4j 1. x is vulnerable to deserialization of untrusted data. This flaw allows a remote attacker to execute code on the server if the deployed application is configured to use JMSSink and to the attacker's JNDI LDAP endpoint.
Is Log4j 1 Secure
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server.
Is 1.18 1 safe from Log4j
Is My Server Safe All servers running 1.18. 1 and above are completely safe.
What are the differences between Log4j 1 and 2
Community support: Log4j 1. x is not actively maintained, whereas Log4j 2 has an active community where questions are answered, features are added and bugs are fixed. Automatically reload its configuration upon modification without losing log events while reconfiguring.
What versions of Log4j 1 are vulnerable
What happened to log4j recently
| Name | Vulnerability type | Affected log4j versions |
|---|---|---|
| CVE-2021-45046 | Denial of Service (DoS) and RCE | 2.0 through 2.15.0 |
| CVE-2021-4104 | RCE | 1.2* |
| CVE-2021-45105 | Denial of Service (DoS) | 2.0-beta9 to 2.16.0 |
| CVE-2021-44832 | RCE | 2.0 to 2.17.0 |