Is TLS 1.2 still valid
It's the most widely supported protocol — TLS 1.2 is supported by 99.9% of browsers, versus 59.8% that support TLS 1.3, according to SSL Labs.
Is TLS 1.2 not secure
TLS 1.2 is more secure than the previous cryptographic protocols such as SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1. Essentially, TLS 1.2 keeps data being transferred across the network more secure.
Is TLS 1.2 disabled
TLS 1.2 is enabled by default at the operating system level. Once you ensure that the .NET registry values are set to enable TLS 1.2 and verify the environment is properly utilizing TLS 1.2 on the network, you may want to edit the SChannel\Protocols registry key to disable the older, less secure protocols.
Is it recommended to disable TLS 1.1 and replace it with TLS 1.2 or higher
TLS 1.0 and TLS 1.1 are no longer considered secure, due to the fact that they are vulnerable to various attacks, such as the POODLE attack. Disabling TLS 1.0 and TLS 1.1 on your server will force clients to use a more secure protocol (TLS 1.2), which is less vulnerable to attack.
Is TLS 1.3 out yet
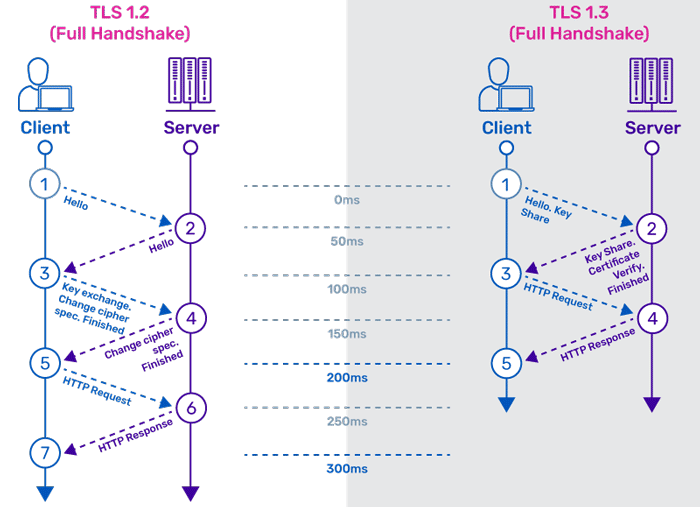
The most recent, TLS 1.3, was released in August 2018. The differences between TLS 1.2 and 1.3 are extensive and significant, offering improvements in both performance and security.
Why TLS 1.3 is not used
TLS 1.3 mandates the use of specific ciphers, which can take a toll on the server side. SSL offload on application delivery controllers (ADCs) and decryption on servers would require costly hardware upgrades and administrative overhead. TLS 1.2 is still relevant and has not yet been compromised.
Which version of TLS is unsafe
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Does TLS 2.0 exist
The history of TLS
SSL 1.0 was never released because it contained serious vulnerabilities. Version 2.0 came out with Netscape Navigator 1.1 in 1995, however it still contained a number of serious flaws. SSL 3.0 was a heavily redesigned version and came out in 1996, with many of the security issues resolved.
Is TLS 1.2 deprecated
Older versions such as TLS 1.0 and TLS 1.1 have been completely deprecated, and using them is a sure shot invitation for attackers. While TLS 1.2 can still be used, it is considered safe only when weak ciphers and algorithms are removed.
Why is TLS 1.0 and 1.1 bad
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Which versions of TLS are obsolete
With the recent finalization of TLS 1.3 by the IETF in August 2018, Apple, Google, Microsoft, and Mozilla announced the end of support for TLS 1.0 and 1.1 in Chrome, Edge, IE, Firefox, and Safari. In line with these industry standards, Ex Libris will deprecate TLS 1.0 and TLS 1.1.
Is TLS 1.3 recommended
TLS 1.3 offers several improvements over earlier versions, most notably a faster TLS handshake and simpler, more secure cipher suites. Zero Round-Trip Time (0-RTT) key exchanges further streamline the TLS handshake. Together, these changes provide better performance and stronger security.
Why is TLS 1.0 weak
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.1 and 1.2 secure
TLS 1.1 allows for the use of insecure padding schemes such as the SSL 3.0/TLS 1.0 padding scheme, which is vulnerable to attacks such as the BEAST attack. TLS 1.2 introduces new padding schemes that are more secure and resistant to attacks.
Why is TLS 1.2 insecure
TLS 1.2 uses a complex cipher suite that includes support for encryption algorithms and ciphers with known cryptographic weaknesses. While the complexity results in the poor choice of the cipher suite, support for weak security mechanisms amplifies the risks of encryption attacks.
Can TLS 1.2 Be Hacked
What Is the Raccoon Attack The Raccoon attack is a newly discovered vulnerability in TLS 1.2 and earlier versions. It allows hackers (in certain situations) to determine a shared session key and use that to decrypt TLS communications between the server and client.
How long has TLS 1.2 been supported
History and development
| Protocol | Published | Status |
|---|---|---|
| TLS 1.0 | 1999 | Deprecated in 2021 ( RFC 8996) |
| TLS 1.1 | 2006 | Deprecated in 2021 ( RFC 8996) |
| TLS 1.2 | 2008 | In use since 2008 |
| TLS 1.3 | 2018 | In use since 2018 |
Is TLS 1.1 a security risk
Risk of outdated TLS protocols
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Why is TLS 1.2 deprecated
TLS 1.2 uses a complex cipher suite that includes support for encryption algorithms and ciphers with known cryptographic weaknesses. While the complexity results in the poor choice of the cipher suite, support for weak security mechanisms amplifies the risks of encryption attacks.
Why is TLS 1.2 still used
One of the main reasons people continue to use TLS 1.2 is compatibility. While TLS 1.3 is more secure, not all devices, browsers, and servers support it.
Why TLS 1.1 is bad
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.1 outdated
TLS 1.0 and 1.1 were deprecated in Mar 2021 with IETF RFC 8996. Today, the baseline TLS version used by most enterprises and businesses is 1.2. Many organizations, particularly those in highly regulated verticals and government agencies, also have to meet their respective compliance requirements.
Why is TLS 1.0 unsafe
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Does TLS 1.2 have weak ciphers
Especially weak encryption algorithms in TLS 1.2 are designated as NULL, RC2, RC4, DES, IDEA, and TDES/3DES; cipher suites using these algorithms should not be used9. TLS 1.3 removes these cipher suites, but implementations that support both TLS 1.3 and TLS 1.2 should be checked for obsolete cipher suites.
Is TLS 1.1 still acceptable
Over time, new TLS versions are developed, and some of the previous versions become outdated for vulnerabilities or technical reasons; and, therefore, should no longer be used to protect data. TLS 1.2 or TLS 1.3 should be used, and any organizations should not use SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1.