Is TLS 1.2 still ok
While TLS 1.2 can still be used, it is considered safe only when weak ciphers and algorithms are removed. On the other hand, TLS 1.3 is new; it supports modern encryption, comes with no known vulnerabilities, and also improves performance.
Is TLS 1.2 disabled
TLS 1.2 is enabled by default at the operating system level. Once you ensure that the .NET registry values are set to enable TLS 1.2 and verify the environment is properly utilizing TLS 1.2 on the network, you may want to edit the SChannel\Protocols registry key to disable the older, less secure protocols.
Is TLS 1.3 out yet
The most recent, TLS 1.3, was released in August 2018. The differences between TLS 1.2 and 1.3 are extensive and significant, offering improvements in both performance and security.
Is TLS 1.2 not secure
TLS 1.2 is more secure than the previous cryptographic protocols such as SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1. Essentially, TLS 1.2 keeps data being transferred across the network more secure.
Why is TLS 1.2 still used
One of the main reasons people continue to use TLS 1.2 is compatibility. While TLS 1.3 is more secure, not all devices, browsers, and servers support it.
Does TLS 2.0 exist
The history of TLS
SSL 1.0 was never released because it contained serious vulnerabilities. Version 2.0 came out with Netscape Navigator 1.1 in 1995, however it still contained a number of serious flaws. SSL 3.0 was a heavily redesigned version and came out in 1996, with many of the security issues resolved.
How do I know if TLS 1.2 is active
How to check if TLS 1.2 is enabled If the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client\DisabledByDefault is present, the value should be 0.
Why TLS 1.3 is not used
TLS 1.3 mandates the use of specific ciphers, which can take a toll on the server side. SSL offload on application delivery controllers (ADCs) and decryption on servers would require costly hardware upgrades and administrative overhead. TLS 1.2 is still relevant and has not yet been compromised.
When was TLS 1.2 deprecated
2 End of Life. It appears the maximum number of years is 22years and the average is approximately 15 years. TLS 1.2 being published in 2008 would then have an expected life of 22years to 2023 however we expect it to be longer than this.
Is TLS 1.1 outdated
TLS 1.0 and 1.1 were deprecated in Mar 2021 with IETF RFC 8996. Today, the baseline TLS version used by most enterprises and businesses is 1.2. Many organizations, particularly those in highly regulated verticals and government agencies, also have to meet their respective compliance requirements.
Should SSL 3.0 be enabled
Therefore, we do not recommend at this time that TLS 1.0 be disabled on a server, unless you know that your users' browsers will not be affected. In short, a surprising number of web servers still use SSL 3.0. Stop using SSL 3.0! It's not secure, and it's not needed.
Why was SSL replaced by TLS
The two public versions of SSL have been deprecated mainly because of the known weaknesses in their security. That's why SSL is not a completely secure, reliable protocol. Fortunately, TLS is secure, as it is the more up-to-date version of SSL, and the latest versions of TLS offer a number of improvements.
Why is TLS 1.1 bad
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.3 fully supported
TLS 1.3 on Chrome is fully supported on 70-114, partially supported on None of the versions, and not supported on 4-69 Chrome versions.
How long has TLS 1.2 been supported
History and development
| Protocol | Published | Status |
|---|---|---|
| TLS 1.0 | 1999 | Deprecated in 2021 ( RFC 8996) |
| TLS 1.1 | 2006 | Deprecated in 2021 ( RFC 8996) |
| TLS 1.2 | 2008 | In use since 2008 |
| TLS 1.3 | 2018 | In use since 2018 |
When was TLS 1.0 end of life
As of October 31, 2018, the Transport Layer Security (TLS) 1.0 and 1.1 protocols are deprecated for the Microsoft 365 service.
Why are TLS v1 0 and v1 1 no longer recommended
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is SSL 3.0 still being used
SSL 3.0: Launched in 1996 but deprecated in 2015. Known to have security flaws. TLS 1.0: Released as an SSL 3.0 upgrade in 1999 and deprecated in 2021.
Is SSL 3.0 insecure
SSL version 1 and 2, SSLv2 and SSLv3 are now insecure. It is also recommended to phase out TLS 1.0 and TLS 1.1. We recommend that you disable SSLv2, SSLv3, TLS 1.0 and TLS 1.1 in your server configuration so that only the newer TLS protocols can be used. It is recommended to only enable TLS 1.3 for maximum security.
Why is TLS 1.3 better
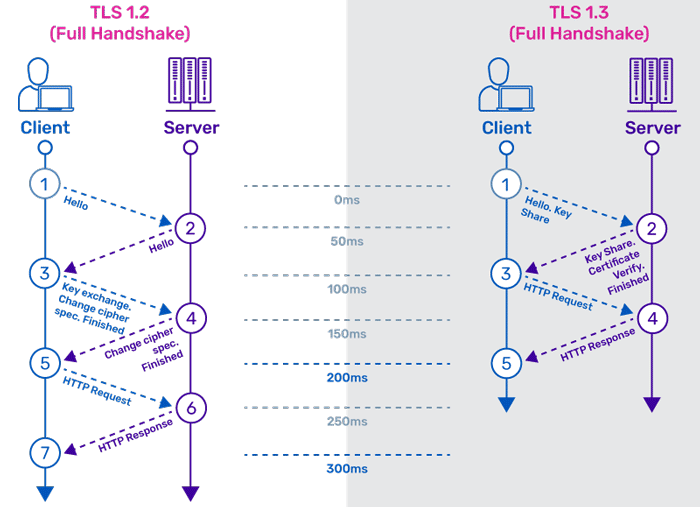
In a nutshell, TLS 1.3 is faster and more secure than TLS 1.2. One of the changes that makes TLS 1.3 faster is an update to the way a TLS handshake works: TLS handshakes in TLS 1.3 only require one round trip (or back-and-forth communication) instead of two, shortening the process by a few milliseconds.
Is TLS 1.3 widely supported
Transport Layer Security (TLS) is a widely used protocol for securing internet communications. It has undergone several revisions over the years, with TLS 1.2 and 1.3 being the most widely used versions today.
Is TLS 1.0 still safe
Over time, new TLS versions are developed, and some of the previous versions become outdated for vulnerabilities or technical reasons; and, therefore, should no longer be used to protect data. TLS 1.2 or TLS 1.3 should be used, and any organizations should not use SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1.
Why SSL 3.0 is not provided
It was not limited to one or two types of machines, but all websites and Windows Virtual machines got vulnerable. To ensure the safety of the users, Microsoft completely disabled SSL 3.0 in Azure Websites by default to protect customers from the vulnerability.
Is TLS 1.3 vulnerability
Many of the major vulnerabilities in TLS 1.2 had to do with older cryptographic algorithms that were still supported. TLS 1.3 drops support for these vulnerable cryptographic algorithms, and as a result it is less vulnerable to cyber attacks.
Why is TLS 1.3 not widely used
This is because TLS 1.3 introduces new security measures that can be challenging to implement and configure correctly. This can lead to increased costs and longer deployment times, making it a less desirable option for some organizations.