Does TLS 1.3 have vulnerabilities
Many of the major vulnerabilities in TLS 1.2 had to do with older cryptographic algorithms that were still supported. TLS 1.3 drops support for these vulnerable cryptographic algorithms, and as a result it is less vulnerable to cyber attacks.
Is TLS 1.3 recommended
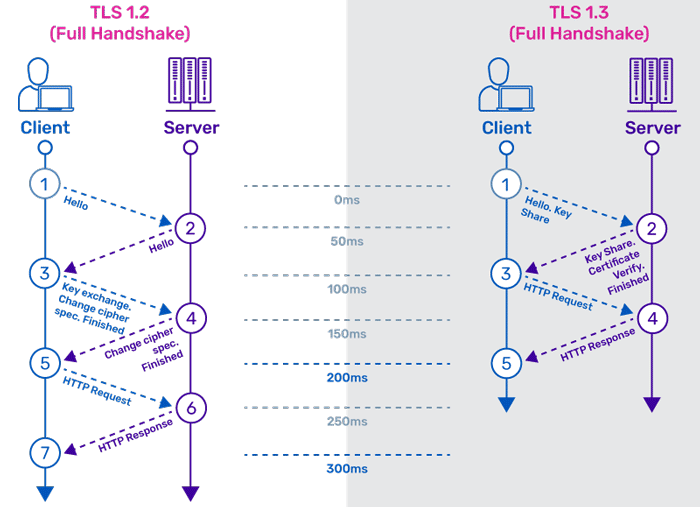
TLS 1.3 offers several improvements over earlier versions, most notably a faster TLS handshake and simpler, more secure cipher suites. Zero Round-Trip Time (0-RTT) key exchanges further streamline the TLS handshake. Together, these changes provide better performance and stronger security.
Why TLS 1.3 is not used
TLS 1.3 mandates the use of specific ciphers, which can take a toll on the server side. SSL offload on application delivery controllers (ADCs) and decryption on servers would require costly hardware upgrades and administrative overhead. TLS 1.2 is still relevant and has not yet been compromised.
Which version of TLS is vulnerable
While TLS 1.0 & TLS 1.1 are known to be very vulnerable, the TLS 1.2 protocol is considered to be much more secure and is thus recommended for use.
Does TLS 1.3 encrypt the certificate
Important Certificate Considerations
One caveat is that in TLS 1.2 the certificate exchanged between the client and server is unencrypted, while in TLS 1.3, the certificate is encrypted.
Is TLS 1.2 not secure
TLS 1.2 is more secure than the previous cryptographic protocols such as SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1. Essentially, TLS 1.2 keeps data being transferred across the network more secure.
Should TLS 1.3 be disabled
However, if some apps you are using in Windows 10 do not support TLS 1.3, the apps possibly do not work properly by TLS 1.3 is enabled, and you should disable TLS 1.3 in Windows 10.
Why is TLS 1.3 important
TLS 1.3 offers some great improvements over TLS 1.2. Vulnerable optional parts of the protocol have been removed, there's support for stronger ciphers that are required to implement perfect forward secrecy (PFS), and the handshake process has been significantly shortened.
Is TLS 1.2 a security risk
While TLS 1.2 can still be used, it is considered safe only when weak ciphers and algorithms are removed. On the other hand, TLS 1.3 is new; it supports modern encryption, comes with no known vulnerabilities, and also improves performance.
Does TLS 1.3 have forward secrecy
TLS 1.3 leaves ephemeral Diffie–Hellman (finite field and elliptic curve variants) as the only remaining key exchange mechanism, in order to ensure forward secrecy.
Is TLS 1.0 vulnerable
While no longer the default security protocol in use by modern OSes, TLS 1.0 is still supported for backwards compatibility. Evolving regulatory requirements as well as new security vulnerabilities in TLS 1.0 provide corporations with the incentive to disable TLS 1.0 entirely.
Is it recommended to disable TLS 1.1 and replace it with TLS 1.2 or higher
TLS 1.0 and TLS 1.1 are no longer considered secure, due to the fact that they are vulnerable to various attacks, such as the POODLE attack. Disabling TLS 1.0 and TLS 1.1 on your server will force clients to use a more secure protocol (TLS 1.2), which is less vulnerable to attack.
What does TLS 1.3 do
TLS 1.3 is the latest version of the internet's most deployed security protocol, which encrypts data to provide a secure communication channel between two endpoints. TLS 1.3 eliminates obsolete cryptographic algorithms, enhances security over older versions, and aims to encrypt as much of the handshake as possible.
What are vulnerabilities of TLS
One of the most common TLS security risks is the use of weak ciphers. Attackers can crack weak ciphers easily, thereby allowing them to gain access to sensitive data. Some other TLS vulnerabilities include Padding Oracle on Downgraded Legacy Encryption (POODLE), man-in-the-middle (MITM), and so on.
Is TLS 1.3 handshake encrypted
TLS 1.3 is one step ahead of TLS 1.2 in sending an encrypted message. It means less information a hacker can steal in the handshake process. sends its Change Cipher Spec and Finished message.
Is TLS 1.1 and 1.2 secure
TLS 1.1 allows for the use of insecure padding schemes such as the SSL 3.0/TLS 1.0 padding scheme, which is vulnerable to attacks such as the BEAST attack. TLS 1.2 introduces new padding schemes that are more secure and resistant to attacks.
Why is TLS 1.0 and 1.1 bad
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Which TLS should be disabled
As a system administrator, you should enable TLS 1.2 and TLS 1.3 on your Windows Server to enhance the security of your infrastructure, but wait, that's not enough. You should disable TLS 1.0 and TLS 1.1 on Windows Server as they are deprecated for their weak security.
Is TLS 1.0 a vulnerability
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Why is TLS 1.2 insecure
TLS 1.2 uses a complex cipher suite that includes support for encryption algorithms and ciphers with known cryptographic weaknesses. While the complexity results in the poor choice of the cipher suite, support for weak security mechanisms amplifies the risks of encryption attacks.