What are the advantages of vulnerability scanning
Assesses your security risk level
Regular vulnerability scans measure your IT hygiene as it identifies how effective your security measures are. Scanning software typically generates a report listing and scoring the detected assets in your network and their risk level.
What is the difference between vulnerability scan and security scan
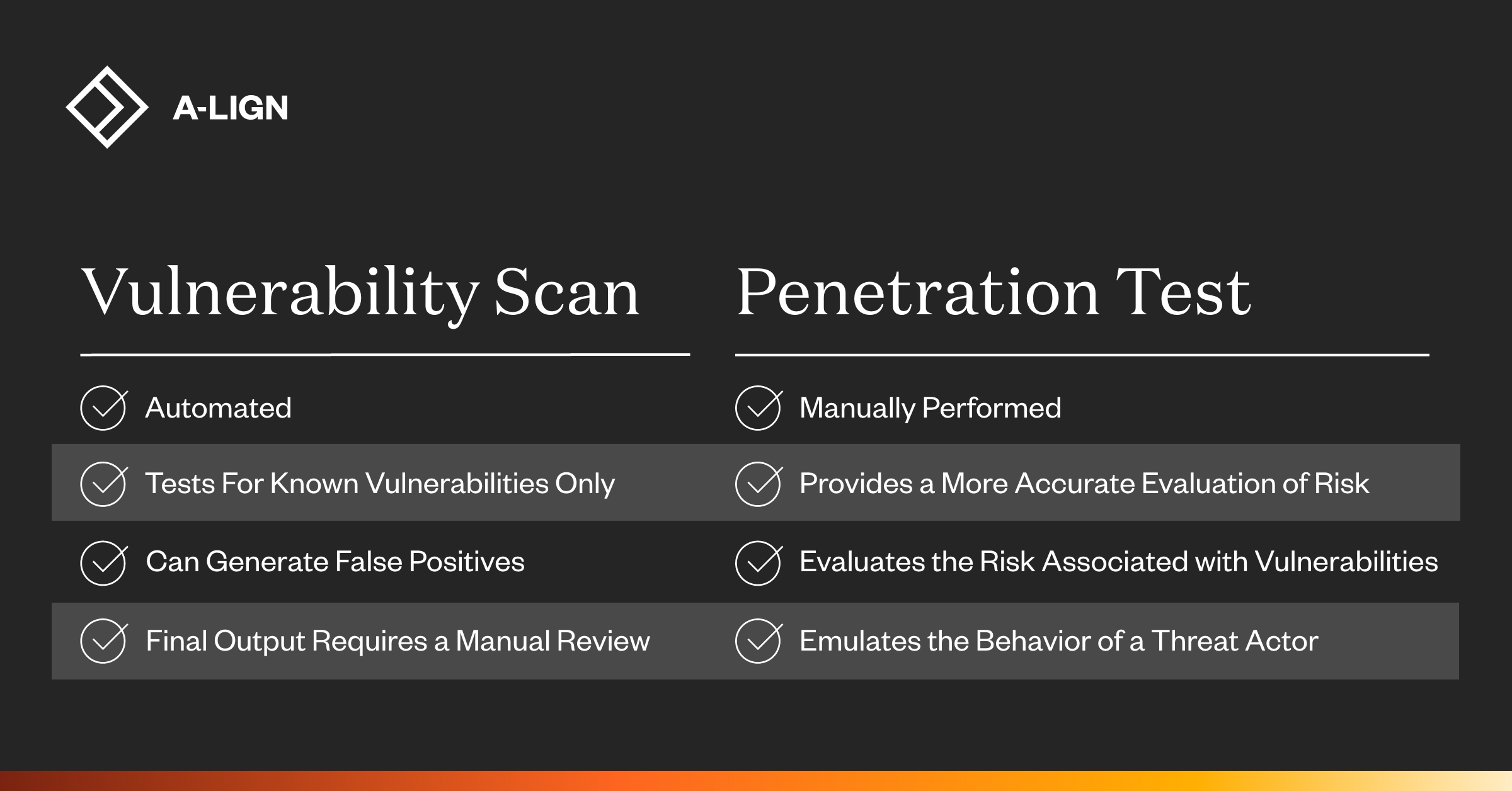
A vulnerability assessment is a component of a security assessment. A security assessment requires manual investigation and testing, but a vulnerability scan is automated. A security assessment looks for current and future vulnerabilities, and a vulnerability scan is only a point-in-time snapshot.
What is the goal of vulnerability scanning
Identifying security threats: Vulnerability scans can help organizations identify potential security threats in their infrastructure, including unpatched software, misconfigured systems, and weak passwords. This information can be used to prioritize remediation efforts and reduce the risk of a successful attack.
What are the limitations of vulnerability scans
Vulnerability scanners are limited in their ability to detect unknown vulnerabilities, as they rely on databases of known vulnerabilities to identify potential threats.
What are the cons of vulnerability scanning
Drawbacks of vulnerability scanning tools
Because a vulnerability scanning tool also misses vulnerabilities, you have no guarantee that your systems are not vulnerable. This is one of the biggest limitations of all scanning tools, because there can still be vulnerabilities that hackers can exploit.
Do hackers use vulnerability scanners
How Scanning Tools Help Hackers. The most commonly used tools are vulnerability scanners that can search for several known vulnerabilities on a target network and potentially detect thousands of vulnerabilities.
What can vulnerability scanners identify
Network based vulnerability scanners identify possible network security attacks and vulnerable systems on wired or wireless networks.
When should you do vulnerability scanning
As such, they recommend performing vulnerability scans once daily. But to determine if this is the best for your unique use case, you should first define your risk appetite and understand the value of every asset and network device that makes up your digital ecosystem.
How are vulnerabilities detected
The vulnerability scanner uses a database to compare details about the target attack surface. The database references known flaws, coding bugs, packet construction anomalies, default configurations, and potential paths to sensitive data that can be exploited by attackers.
Are vulnerability scans legal
You should also ensure you have a target site owner's permission to carry out vulnerability scanning before commencing any such activity. Doing so without permission is illegal.
What type of vulnerabilities will not be found by a vulnerability scanner
Vulnerability scanners cannot detect vulnerabilities for which they do not have a test, plug-in, or signature. Signatures often include version numbers, service fingerprints, or configuration data.
What are the disadvantages of CVSS
The Shortcomings of CVSS Scoring as a Risk-Management ToolCVSS score is not a measure of actual risk. The main issue is that the vulnerability itself, when taken out of context, should not be equated to risk.Not taking your Environment into Account.The importance of threat intelligence.
What are the disadvantages of vulnerability scanners
Another limitation of vulnerability scanners is they are only able to detect the vulnerabilities that are present on the system at the time of the scan. If a vulnerability is introduced after the scan has been completed, the scanner, obviously, won't detect it.
How do hackers find vulnerabilities
Exploitation is a piece of programmed software or script which can allow hackers to take control over a system, exploiting its vulnerabilities. Hackers normally use vulnerability scanners like Nessus, Nexpose, OpenVAS, etc. to find these vulnerabilities.
Which potential risk cannot be checked by running a vulnerability scan
A vulnerability scanner can scan for vulnerabilities, but it won't necessarily be able to check for a password used to protect an archive file.
Is IT illegal to run a vulnerability scanning
It's not legal to test a website for a vulnerability without permission from the owner. While there may many reasons, here are a few to consider: While testing for a vulnerability, you might bring the website down if an unsuccessful exploitation left the application in unknown state.
How do hackers scan for vulnerabilities
Scanning can be considered a logical extension (and overlap) of active reconnaissance that helps attackers identify specific vulnerabilities. It's often that attackers use automated tools such as network scanners and war dialers to locate systems and attempt to discover vulnerabilities.
Do hackers use CVE
Can Hackers Use CVE to Attack My Organization The short answer is yes but many cybersecurity professionals believe the benefits of CVE outweigh the risks: CVE is restricted to publicly known vulnerabilities and exposures.
Are Nmap scans illegal
When used properly, Nmap helps protect your network from invaders. But when used improperly, Nmap can (in rare cases) get you sued, fired, expelled, jailed, or banned by your ISP. Reduce your risk by reading this legal guide before launching Nmap.
Are vulnerability scans illegal
You should also ensure you have a target site owner's permission to carry out vulnerability scanning before commencing any such activity. Doing so without permission is illegal.
What is a common drawback or weakness of a vulnerability scanner
Drawbacks of Vulnerability Scanning
Only known risks can be found: a vulscan tool can only be expected to detect threats that are known to its database. Zero-day, or previously unknown, threats require an active threat monitoring solution, typically a SOC that is powered by AI.
Is scanning for vulnerabilities illegal
You should also ensure you have a target site owner's permission to carry out vulnerability scanning before commencing any such activity. Doing so without permission is illegal.
How do hackers pick their victims
Cybercriminals rarely choose their victims at random. The first stage of the cyber kill chain is reconnaissance, where an attacker narrows down a list of targets based on organization profile, security posture, and vulnerable individuals.
What is the limitation of vulnerability scan
Another limitation of vulnerability scanners is they are only able to detect the vulnerabilities that are present on the system at the time of the scan. If a vulnerability is introduced after the scan has been completed, the scanner, obviously, won't detect it.
Can a vulnerability scan create problems
Running a vulnerability scan can pose its own risks as it is inherently intrusive on the target machine's running code. As a result, the scan can cause issues such as errors and reboots, reducing productivity.