What is a zero-day vulnerability
6 ngày trước
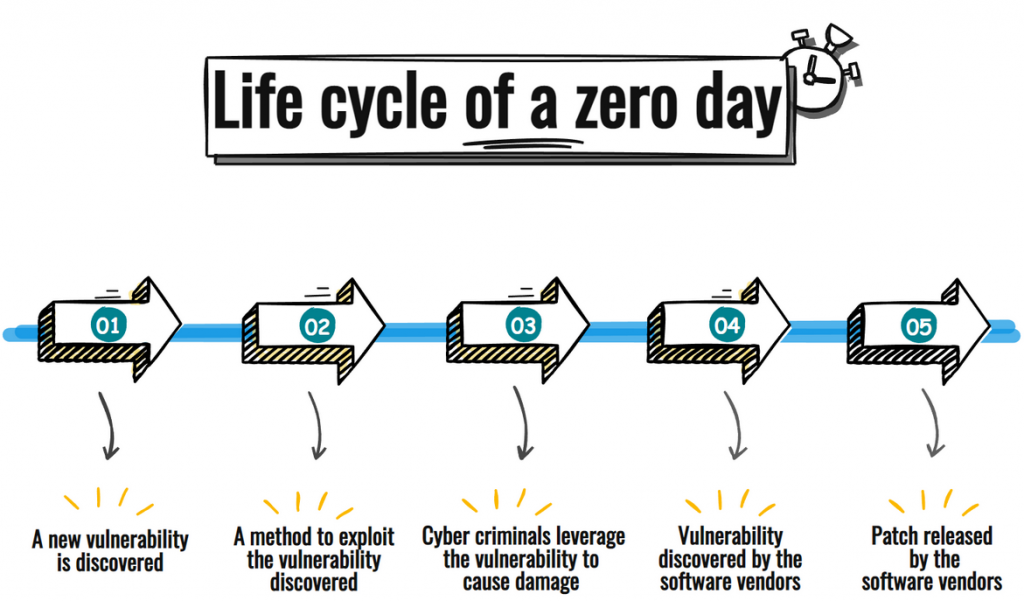
Zero-day attacks begin with zero-day vulnerabilities, meaning flaws or holes in security software. These can result from improper computer or security configurations or programming errors by developers themselves. Cyberattackers exploit these vulnerabilities without developers knowing.
Is zero-day the same as vulnerability
A zero-day vulnerability is a vulnerability in a system or device that has been disclosed but is not yet patched. An exploit that attacks a zero-day vulnerability is called a zero-day exploit.
Why is it called zero-day vulnerability
The term “Zero-Day” is used when security teams are unaware of their software vulnerability, and they've had “0” days to work on a security patch or an update to fix the issue. “Zero-Day” is commonly associated with the terms Vulnerability, Exploit, and Threat.
Is zero-day a threat
A zero-day threat or attack is an unknown vulnerability in your computer or mobile device's software or hardware. The term is derived from the age of the exploit, which takes place before or on the first (or “zeroth”) day of a security vendors' awareness of the exploit or bug.
Is Log4j a zero-day vulnerability
Log4j is just a recent zero-day attack example. There have been many in the past. Many more will no doubt happen in the future.
What is the opposite of zero-day vulnerability
Whereas zero-days are a class of vulnerability that is unknown to a software developer or hardware manufacturer, an N-day is a flaw that is already publicly known but may or may not have a security patch available.
How do hackers find zero-day vulnerability
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability. Attackers have found a new route by exploiting a zero-day vulnerability in Google's Android mobile operating system.
What vulnerability does zero-day exploit
The zero-day exploit abused a local privilege vulnerability in Microsoft Windows to run arbitrary code and install applications and view and change the data on compromised applications. Once the attack was identified and reported to the Microsoft Security Response Center, a patch was developed and rolled out.
What is 0day vulnerability in Log4j
Per Nozomi Networks attack analysisOpens a new window , the “new zero-day vulnerability in the Apache Log4jOpens a new window logging utility that has been allowing easy-to-exploit remote code execution (RCE).” Attackers can use this security vulnerability in the Java logging library to insert text into log messages …
Is Log4j still a threat
Log4j remains a threat in 2023
The highest concentration of critical findings linked to Log4j were found within the first 48 hours of the vulnerability becoming known. At the time, findings often originated in the core of an application and later findings migrated to the dependences those applications rely on.
Why are zero-day vulnerabilities so difficult to defend against
A zero-day (or 0-day) vulnerability is a software vulnerability that is discovered by attackers before the vendor has become aware of it. By definition, no patch exists for zero day vulnerabilities and user systems have no defenses in place, making attacks highly likely to succeed.
Do most attackers use zero-day attacks
Zero-day attacks consist of almost 80% of all malware attacks. Take a look at some recent attacks and learn how to prevent them.
How are zero-day vulnerabilities found
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability.
Is Log4j safe to use now
The widespread vulnerability that first appeared in Apache Log4j in 2021 will continue to be exploited, potentially even in worse ways than we've seen to date. The more worrisome aspect of these threats is that there's a good chance they'll continue to be exploited months or years into the future.
Is Log4j still being exploited
Log4j remains a threat in 2023
As the Log4j library is widely used it is likely to still be embedded in large systems and organizations that are not keeping track what is in their software supply chain are most at risk.
How we can defend zero-day vulnerability
Vulnerability scanning: Regular scanning is a primary technique for cybersecurity teams to identify security flaws in the software code of applications. Monitoring activities: We can prevent systems from zero-day attacks by monitoring the network and checking unexpected traffic.
Why do zero-day vulnerabilities pose a risk
Zero-day vulnerabilities pose a high risk to organizations because they are typically discovered before security researchers or software developers are aware of them and a patch can be released, allowing threat actors to exploit flaws and profit from their schemes.
What is a real life example of zero-day vulnerability
Via zero-day exploits, an APT can gain access to a large number of computing systems at high profile organizations. A prominent example was the SolarWinds supply chain attack, in which an organized cybercrime group exploited a zero-day vulnerability to breach to US government agencies and a majority of the Fortune 500.
What is Log4j zero day vulnerability
Per Nozomi Networks attack analysisOpens a new window , the “new zero-day vulnerability in the Apache Log4jOpens a new window logging utility that has been allowing easy-to-exploit remote code execution (RCE).” Attackers can use this security vulnerability in the Java logging library to insert text into log messages …
How bad is Log4j vulnerability
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
Is Log4j still vulnerable
With 40% of Log4j Downloads Still Vulnerable, Security Retrofitting Needs to Be a Full-Time Job. Vulnerabilities like Log4j remain responsible for security breaches a full year after the discovery of the flaw.
Is Log4j zero-day vulnerability
Log4j is just a recent zero-day attack example. There have been many in the past. Many more will no doubt happen in the future.
Has Log4j been fixed
No, the original Log4j vulnerability has essentially mutated into three newer forms as Apache has issued patches, though all were addressed by the end of 2021. Apache patched the original vulnerability, CVE-2021-44228, on December 6, 2021. However, it turned out that this patch did not entirely fix the issue.
What type of vulnerability is Log4j
The Log4j issue is a type of remote code execution vulnerability, and a very serious one that allows an attacker to drop malware or ransomware on a target system.
How serious is the Log4j issue
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.