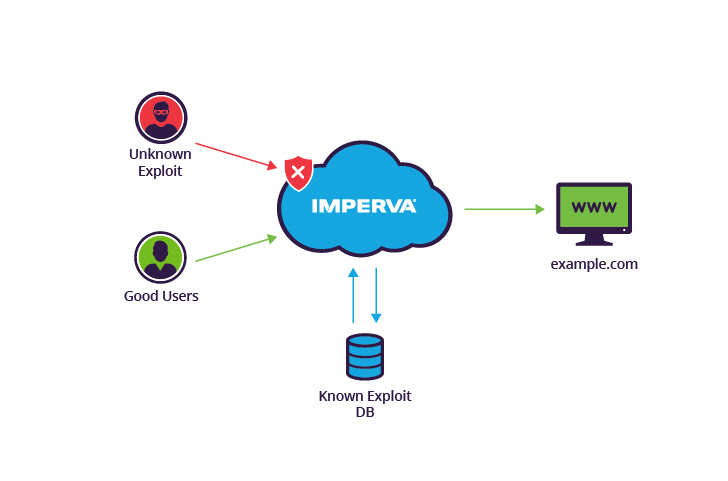
Is zero-day attack a virus
A zero-day virus (also known as zero-day malware or next-generation malware) is a previously unknown computer virus or other malware for which specific antivirus software signatures are not yet available. Traditionally, antivirus software relied upon signatures to identify malware.
Is zero-day exploit a malware
Zero day malware is malware that exploits unknown and unprotected vulnerabilities. This novel malware is difficult to detect and defend against, making zero day attacks a significant threat to enterprise cybersecurity.
Is zero-day attack an attack
Definition(s): An attack that exploits a previously unknown hardware, firmware, or software vulnerability.
Is a zero-day 0 day a vulnerability or an exploit
A zero-day vulnerability is a vulnerability in a system or device that has been disclosed but is not yet patched. An exploit that attacks a zero-day vulnerability is called a zero-day exploit.
What is zero-day hacker
Zero-day meaning and definition
"Zero-day" is a broad term that describes recently discovered security vulnerabilities that hackers can use to attack systems. The term "zero-day" refers to the fact that the vendor or developer has only just learned of the flaw – which means they have “zero days” to fix it.
Can zero day attacks be stopped
Preventing zero day attacks is a multistage process. Organizations need the threat intelligence required to identify a potential campaign, tools for acting on this intelligence, and a unified platform that supports rapid, coordinated threat response. Modern cyberattacks are widespread and automated.
Is exploit a malware
Once it identifies a vulnerability, the exploit kit will use the appropriate exploit code and attempt to install and execute malware. Unlike malware, exploits are not inherently malicious, but they are still likely to be used for nefarious purposes.
How do hackers find zero-day exploits
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability. Attackers have found a new route by exploiting a zero-day vulnerability in Google's Android mobile operating system.
Is Stuxnet a zero-day exploit
Windows infection
Stuxnet attacked Windows systems using an unprecedented four zero-day attacks (plus the CPLINK vulnerability and a vulnerability used by the Conficker worm).
What is the most likely hacker attack
Malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any other type of malware attack that leverages software in a malicious way.
What is a 0day vulnerability
A zero-day vulnerability is an undiscovered flaw in an application or operating system, a gap in security for which there is no defense or patch because the software maker does not know it exists—they've had “zero days” to prepare an effective response.
What is zero-day exploit risk
A zero-day (0day) exploit is a cyber attack targeting a software vulnerability which is unknown to the software vendor or to antivirus vendors. The attacker spots the software vulnerability before any parties interested in mitigating it, quickly creates an exploit, and uses it for an attack.
What is 0day
The term "zero-day" refers to the fact that the vendor or developer has only just learned of the flaw – which means they have “zero days” to fix it. A zero-day attack takes place when hackers exploit the flaw before developers have a chance to address it. Zero-day is sometimes written as 0-day.
What is zero-day Chrome
Zero-day vulnerabilities are often exploited by sophisticated state-sponsored threat actors, aiming primarily at high-profile figures within government, media, or other vital organizations. Therefore, it is strongly recommended that all Chrome users install the available security update as soon as possible.
Why is zero-day malware a strong weapon for hackers
Zero-day attacks are especially dangerous because the only people who know about them are the attackers themselves. Once they have infiltrated a network, criminals can either attack immediately or sit and wait for the most advantageous time to do so.
What is the most famous zero-day exploit
Stuxnet, dubbed as “Operation Olympic Games” was the world's first digital weapon, which was created to target the Iranian nuclear program; it leveraged zero-day exploits to infect Windows machines. The malicious computer worm was a product of the concerted efforts of NSA, the CIA, and Israeli intelligence.
Is exploit a Trojan
Exploit Trojan: As the name implies, these Trojans identify and exploit vulnerabilities within software applications in order to gain access to the system. Downloader Trojan: This type of malware typically targets infected devices and installs a new version of a malicious program onto the device.
Can malware spy on you
Spyware is a form of malware that hides on your device, monitors your activity, and steals sensitive information like bank details and passwords.
How are 0days found
Vulnerability scanning can detect some zero-day exploits. Security vendors who offer vulnerability scanning solutions can simulate attacks on software code, conduct code reviews, and attempt to find new vulnerabilities that may have been introduced after a software update.
How common are zero-day attacks
According to the Ponemon Institute, 80% of successful breaches were Zero-Day attacks.
Who cracked Stuxnet
Ralph Langner
When first discovered in 2010, the Stuxnet computer worm posed a baffling puzzle. Beyond its sophistication loomed a more troubling mystery: its purpose. Ralph Langner and team helped crack the code that revealed this digital warhead's final target.
Is Stuxnet virus still alive
A decade after Stuxnet, SafeBreach Labs researchers discovered new zero-day vulnerabilities connected to the threat, which they unveiled at Black Hat USA 2020. The threat of Stuxnet is still alive, thanks to the discovery of new zero-day vulnerabilities connected to an old Microsoft Windows flaw.
What is the top 1 hacker
Kevin Mitnick holds the title as the world's most famous hacker ever, with this title dating back to 1995 by the US Department of Justice. Kevin Mitnick started hacking at an early age.
Where is the best hacker
It has been observed that countries with the most advanced technology and digitally connected infrastructure produce the best hackers. China and USA are clear examples of digitally advanced nations which both deploy tools and specialists for intelligence gathering, and for the protection of their national interests.
How do people find zero-day exploits
However, there are a few ways to identify suspicious behavior that might indicate a zero-day exploit: Statistics-based monitoring—anti-malware vendors provide statistics on exploits they previously detected. Organizations can feed these data points into a machine learning system to identify current attacks.