What are the 3 A’s in information security
Authentication, authorization, and accounting (AAA) is a security framework that controls access to computer resources, enforces policies, and audits usage.
What are the three 3 aspects of information security
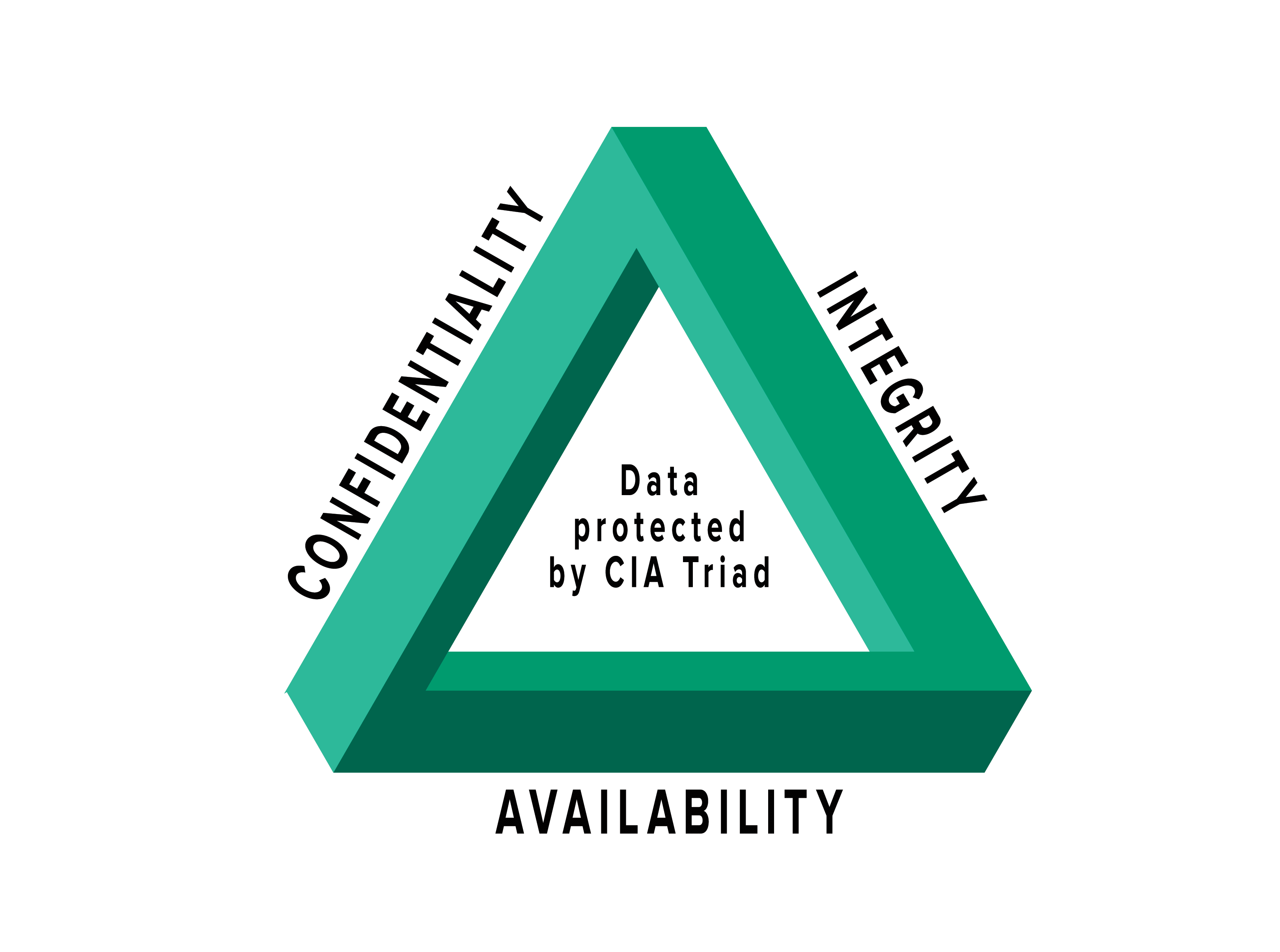
When we discuss data and information, we must consider the CIA triad. The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the three 3 security dimensions
confidentiality, integrity, and availability
The traditional information security objectives are confidentiality, integrity, and availability. Achieving these three objectives does not mean achieving security [1]. It is well known that a formal security policy is a prerequisite of security.
What are the 3 key things that information security is most concerned with
Information security controls are vital to mitigate security risks and to protect the integrity, confidentiality, and availability (also known as the CIA triad) of your IT assets. They are an essential component of effective information security management.
What are the three components of AAA
AAA (Authentication, Authorization, Accounting) –
AAA is a standard-based framework used to control who is permitted to use network resources (through authentication), what they are authorized to do (through authorization), and capture the actions performed while accessing the network (through accounting).
What is meant by 3 level of security
Security level 3 means the level for which further specific protective security measures shall be maintained for a limited period of time when a security incident is probable or imminent, although it may not be possible to identify the specific target.
What are the 3 types of security policy in data and information security
A: Three types of security policies in common use are program policies, issue-specific policies, and system-specific policies.
What is 3S security
3S SECURITY SYSTEM is a wholesale distribution business providing complete range of Electronic Security Systems all over India & abroad. Company's Main Products are CCTV Camera, CCTV System, Switcher, Recorder, CCTV Lens, UTP Video Transceiver, Accessories, CCTV Camera Housing, Fire Alarm System, P.A.
What are the main three 3 objectives of security
Confidentiality, integrity and availability together are considered the three most important concepts within information security. Considering these three principles together within the framework of the "triad" can help guide the development of security policies for organizations.
What are the 3 types of security controls
There are three main types of IT security controls including technical, administrative, and physical.
What do the three AAA stand for
Authentication, authorization, and accounting
Authentication, authorization, and accounting, often called AAA or Triple-A, are sets of services and protocols that enable granular access control over computer networks.
What does AAA stand for
American Automobile AssociationAAA / Full name
AAA stands for the American Automobile Association.
What are the 3 main data protection policies
Therefore, most data protection strategies have three key focuses: Data security – protecting data from malicious or accidental damage. Data availability – Quickly restoring data in the event of damage or loss. Access control – ensuring that data is accessible to those who actually need it, and not to anyone else.
What is digital 3S
3S is the abbreviation for Single Scan Serialization (3S), tracking your product through the point-of-sale process.
What are the 3 important key security concepts explain them all briefly
Confidentiality: controlling who gets to read information; Integrity: assuring that information and programs are changed only in a specified and authorized manner; and. Availability: assuring that authorized users have continued access to information and resources.
What is three level security
Security is the capability of a system to protect information and system resources with respect to confidentiality and integrity. The3 level security system aims to guarantee more security through its three levels–Through Text Password; Through Image based Password, and Through One-Time Automated Password.
What are the 4 forms of security
4 Forms Of Best SecurityPrevention. The best police in the world are effective solely because they prevent crimes before it actually happens.Add a Security System. A security system can work wonders to help enhance your security at home or at the office.Hire a Security Guard.Personal Security.
What are the A’s of cyber security
When using identity and access management, remember the basic three A's: Authentication, Authorization, and Accounting. Authentication is based on the idea that each individual user has unique information that sets him or her apart from other users to provide proof of identity when they identify themselves.
What are the benefits of AAA model
What are the Advantages of AAA The main advantages of the AAA Framework, which enables intelligent management of network security in accessing computer resources, are: It improves the scalability of the network and provides flexibility. It contributes to the establishment of a standard in network protocols.
What does AAA mean in technology
Authentication, authorization, and accounting
Authentication, authorization, and accounting (AAA) is a term for a framework for intelligently controlling access to computer resources, enforcing policies, auditing usage, and providing the information necessary to bill for services.
What does AAA stand for cyber
Authentication, Authorization, and Accounting
Authentication, Authorization, and Accounting (AAA) is a three-process framework used to manage user access, enforce user policies and privileges, and measure the consumption of network resources.
What is the 3 Data Protection Act 1998
The Data Protection Act 1998 was an act of Parliament designed to protect personal data stored on computers or in organised paper filing systems. It enacted the EU Data Protection Directive, 1995's provisions on the protection, processing and movement of personal data.
What is 3S Secure Digital Theft Protection
The 3S Smart Barcode protection, implemented on the product and packaging during production, features individual item tracking and security unique to every item produced. During point of sale, the technology is used to track next level sales data, in turn making items never purchased easily identifiable as well.
What is a 3S barcode
How 3S Works. During Point of Sale, DiSa 3S Smart Barcodes use Single Scan technology to uniquely identify each item, track next level sales data and prevent return fraud.
What are the three security models
There are 3 main types of Classic Security Models.Bell-LaPadula.Biba.Clarke Wilson Security Model.