What are the 3 data protection measures
These are known as 'confidentiality, integrity and availability' and under the UK GDPR, they form part of your obligations.
What is principle 3 of the general data protection regulation
The third principle requires that the personal data you are processing is adequate, relevant and not excessive. This means the data must be limited to what is necessary for the purpose(s) you are processing it. The fourth data protection principle is about accuracy.
What are the 5 data protection principles
Lawfulness, fairness and transparency. Purpose limitation. Data minimisation. Accuracy.
What are the 8 rules of the Data Protection Act
What Are the Eight Principles of the Data Protection ActFair and Lawful Use, Transparency. The principle of this first clause is simple.Specific for Intended Purpose.Minimum Data Requirement.Need for Accuracy.Data Retention Time Limit.The right to be forgotten.Ensuring Data Security.Accountability.
What are the three 3 data principles
To make it easier, both for users as well as for companies and public officials, it helps to look at the 3 core principles of Data Privacy: Transparency, Legitimate Purpose, and Proportionality.
What are the 3 types of security policy in data and information security
A: Three types of security policies in common use are program policies, issue-specific policies, and system-specific policies.
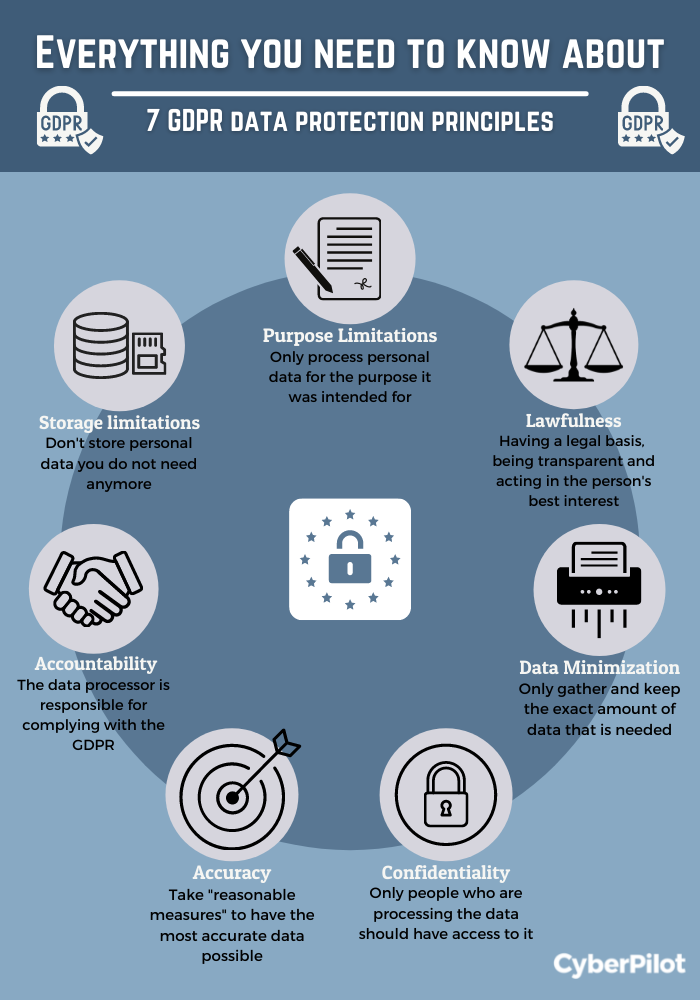
What are the 7 principles of data protection
The principles are: Lawfulness, Fairness, and Transparency; Purpose Limitation; Data Minimisation; Accuracy; Storage Limitations; Integrity and Confidentiality; and Accountability. We take you through an example of creating an online newsletter to illustrate how each principle works.
What is principle 7 of the Data Protection Act
7Appropriate technical and organisational measures shall be taken against unauthorised or unlawful processing of personal data and against accidental loss or destruction of, or damage to, personal data.
What are the 4 principles of the Data Protection Act
The UK GDPR sets out seven key principles:Lawfulness, fairness and transparency.Purpose limitation.Data minimisation.Accuracy.Storage limitation.Integrity and confidentiality (security)Accountability.
What are the three types of data
In this article, we explore the different types of data, including structured data, unstructured data and big data.
What are the three basic states of data
Three states of data is a way of categorizing structured and unstructured data. The three states of data are data at rest, data in motion and data in use. Data can change states quickly and frequently, or it may remain in a single state for the entire life cycle of a computer.
What are the three 3 major areas of security
THREE MAJOR AREAS OF SECURITYPhysical Security.Personnel Security.Document and Information Security.
What are the three 3 primary concepts in information security
Three basic security concepts important to information on the internet are confidentiality, integrity, and availability.
What is the 6 principle of the Data Protection Act
The sixth data protection principle is that personal data processed for any of the law enforcement purposes must be so processed in a manner that ensures appropriate security of the personal data, using appropriate technical or organisational measures (and, in this principle, “appropriate security” includes protection …
What is principle 4 of data protection
The fourth data protection principle is that personal data undergoing processing must be accurate and, where necessary, kept up to date.
Why is the 8 principles for Data Protection Act important
The 8 principles of the Act guided its purpose and the data protection policies of organisations. At its core, the DPA 1998 has eight principles which were used by organisations to design their own data protection policies. Complying with these was essential for organisations to meet their obligations.
What is principle 6 of the general data protection regulation
Integrity and confidentiality. processed in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures”.
What are the 7 golden rules of data protection
Necessary, proportionate, relevant, adequate, accurate, timely and secure: Ensure that information you share is necessary for the purpose for which you Page 2 are sharing it, is shared only with those individuals who need to have it, is accurate and up-to-date, is shared in a timely fashion, and is shared securely (see …
What are the 3 most common data types
Common data types
| Data Type | Definition |
|---|---|
| String (str or text) | Sequence of characters, digits, or symbols—always treated as text |
| Boolean (bool) | True or false values |
| Enumerated type (enum) | Small set of predefined unique values (elements or enumerators) that can be text-based or numerical |
What are the three 3 kinds of data analysis
Three key types of analytics businesses use are descriptive analytics, what has happened in a business; predictive analytics, what could happen; and prescriptive analytics, what should happen.
What are the 3 main types of data classification
Data classification generally includes three categories: Confidential, Internal, and Public data. Limiting your policy to a few simple types will make it easier to classify all of the information your organization holds so you can focus resources on protecting your most critical information.
What are the 3 principles of security list them
When we discuss data and information, we must consider the CIA triad. The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What is the 3 line of defense security
First line of defense: Owns and manages risks/risk owners/managers. Second line of defense: Oversees risks/risk control and compliance. Third line of defense: Provides independent assurance/risk assurance.
What are the 3 types of security systems used to secure an information system
There are three main types of IT security controls including technical, administrative, and physical. The primary goal for implementing a security control can be preventative, detective, corrective, compensatory, or act as a deterrent.
What are the 7 principles of general data protection
The principles are: Lawfulness, Fairness, and Transparency; Purpose Limitation; Data Minimisation; Accuracy; Storage Limitations; Integrity and Confidentiality; and Accountability.