What are the 4 elements of cyber security
Different Elements of Cybersecurity:
Disaster Recovery Planning. Network Security. End-user Security. Operational Security.
What are the 5 elements of cybersecurity
5 Key Elements of a Modern Cybersecurity FrameworkIdentify.Protect.Detect.Respond.Recover.
What are the 3 major types of cyber security
The 3 major types of cyber security are network security, cloud security, and physical security. Your operating systems and network architecture make up your network security. It can include network protocols, firewalls, wireless access points, hosts, and servers.
What are the basic concepts of cybersecurity
Cyber Security is the process and techniques involved in protecting sensitive data, computer systems, networks, and software applications from cyber attacks. The cyber attacks are general terminology that covers a large number of topics, but some of the popular are: Tampering systems and data stored within.
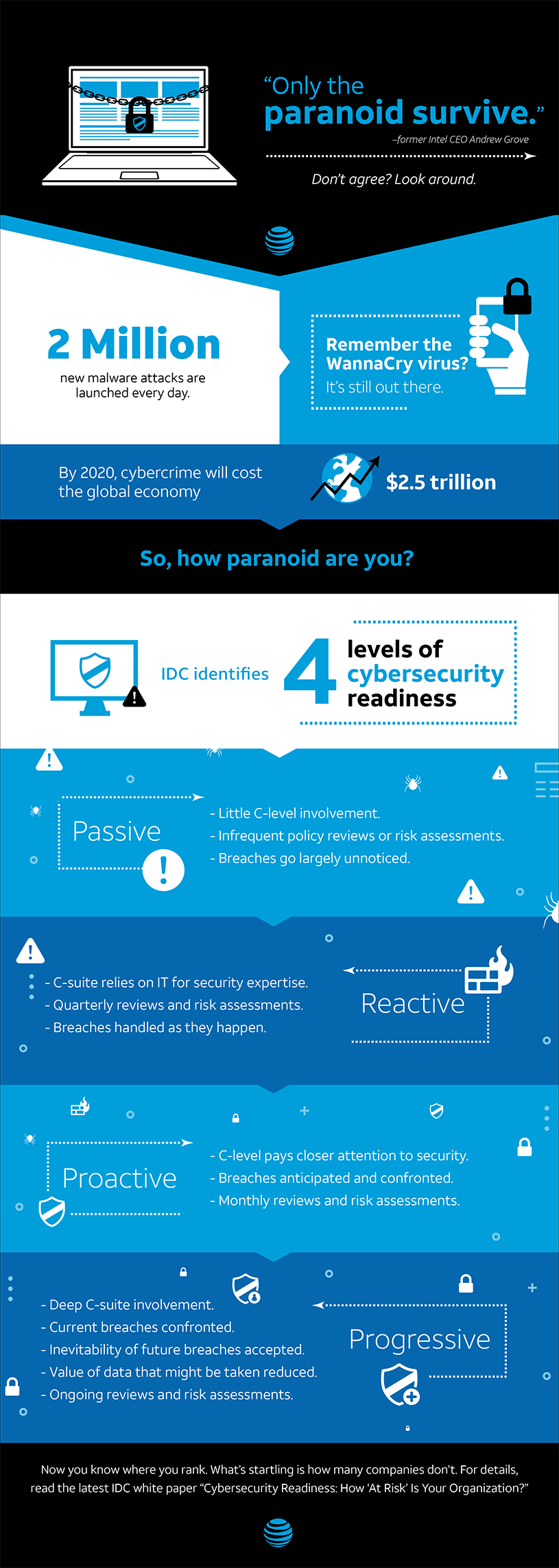
What is Level 4 cyber security Fundamentals
Learners will gain practical experience of protecting personal digital devices, such as a smartphone or personal computer. The role of social engineering in cyberattacks and the implications of cyberthreats for personal privacy are also explored in this Award. Achievement of this Award is nationally recognised.
What are 4 cyber domains
Application security, physical security, risk assessment, and threat intelligence are some of the most common domains in cyber security. An organization considers the various cybersecurity domains while building a cybersecurity policy. Therefore, you can also call them domains of cyber security policy.
What are the 7 domains of cyber security
Security Associate Director, Red Sea…User Domain: The user is the first domain and represents the end-user who accesses the organization's IT infrastructure from either inside the network or outside network.Workstation domain.LAN domain:LAN to WAN domain.WAN domain:Remote access domain.System and application domains.
What are the 6 cybersecurity concepts
The standards-based content will reinforce the six GenCyber Cybersecurity Concepts (Confidentiality, Integrity, Availability, Thinking like an Adversary, Defense in Depth, and Keeping It Simple) through activities and lab exercises.
What are the 7 layers of cyber security
The 7 layers of cyber security are:Physical security.Network security.Perimeter security.Endpoint security.Application Security.Data security.User education.
What are the seven 7 categories of nice cybersecurity
The NICE Framework comprises seven categories (Securely Provision, Operate and Maintain, Oversee and Govern, Protect and Defend, Analyze, Operate and Collect, and Investigate); specialty areas; work roles; tasks; and knowledge, skills and abilities (KSAs).
What are the core concepts of the cybersecurity triad
The three letters in "CIA triad" stand for Confidentiality, Integrity, and Availability. The CIA triad is a common model that forms the basis for the development of security systems. They are used for finding vulnerabilities and methods for creating solutions.
What is C level in cyber security
Cybersecurity is becoming increasingly important for C-level executives. As high-level decision-makers, they must ensure that their organisation has robust cybersecurity practices in place to prevent cyber-attacks. Moreover, they must mitigate the risk of financial loss, reputational damage, and legal liability.
What is level 7 in cyber security
HNC: Cyber Security SCQF Level 7
Reflecting rapidly growing business needs, you will learn procedures to implement data confidentiality, integrity, availability and security controls on networks, servers, and applications. Building both technical and professional skills to pursue a career in cyber security.
What are the 4 main types of vulnerability in cyber security
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What are the 6 Ps of cyber security
These unique functions are known as "the six Ps" (planning, policy, programs, protection, people, and project management).
What are the 7 types of cyber security
It can be divided into seven main pillars:Network Security. Most attacks occur over the network, and network security solutions are designed to identify and block these attacks.Cloud Security.Endpoint Security.Mobile Security.IoT Security.Application Security.Zero Trust.
What is AAA in cyber security
Authentication, authorization, and accounting (AAA) is a security framework that controls access to computer resources, enforces policies, and audits usage.
Why is C used in cyber security
C: The C programming language can be deployed by cyber security experts to perform reverse-engineering and to facilitate the development of powerful anti-virus software. This is because the C language enables cyber security professionals to disassemble malicious software and to examine its design, spread and impact.
What is C and A in cybersecurity
The C&A process is typically used with regard to government initiatives whereby a network device or software program is being reviewed for security issues. At times, however, obtaining the needed approval for any new programs and / or devices can be a slow and costly process.
What is security level 10
At security level 10, you have no security protection. Therefore, security level 10 is not recommended. Running your server at this security level is both a security and integrity risk as you do not have the protection of the higher security levels, 40 and 50, activated and being enforced.
What is level 5 security
Level 5 information includes human-subject research containing individually identifiable information that if disclosed would create risk of criminal liability, loss of insurability or employability, or severe social, psychological, reputational, financial or other harm to an individual or group.
What are the 4 security types
Types#1 – Equity securities. It refers to a stock – common or preferred, held by investors, who are referred to as equity shareholders.#2 – Debt securities. Debt instruments are a type of loan that carries a low risk.#3 – Hybrid securities.#4 – Derivatives.Example #1.Example #2.
What are the 4 factors of vulnerability
There are many aspects of vulnerability, arising from various physical, social, economic, and environmental factors.
What are the 7 P’s in security
To clearly demonstrate how each “P” in the 7Ps framework can be employed in security contexts, a definition of each P – product, price, promotion, place, physical evidence, processes, and people – was clearly explained to the participants.
What are the 7 P’s of information security
We outline the anatomy of the AMBI-CYBER architecture adopting a balanced scorecard, multistage approach under a 7Ps stage gate model (Patient, Persistent, Persevering, Proactive, Predictive, Preventive, and Preemptive).