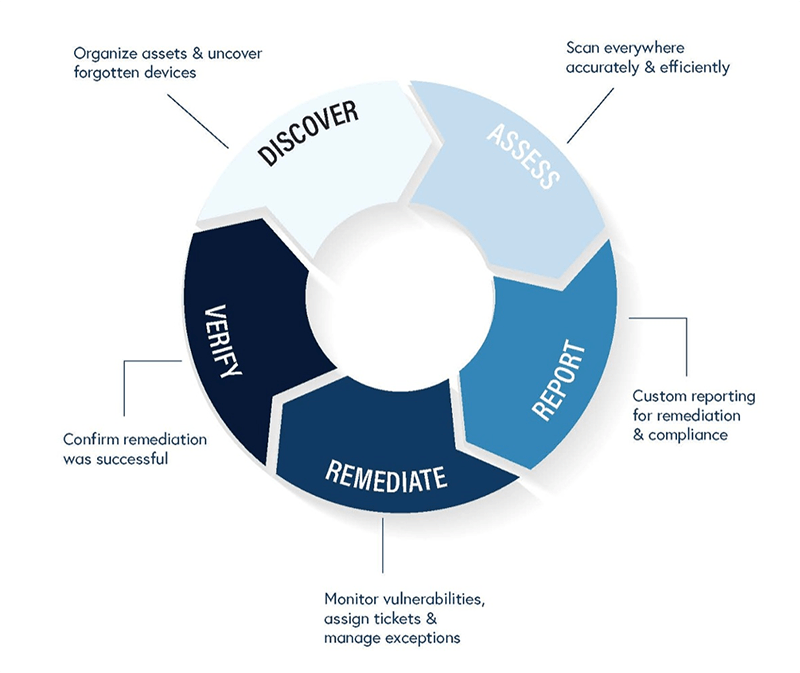
What are the 3 components of vulnerability assessment
There are three dimensions of vulnerability: exposure, sensitivity, and adaptive capacity.
What are the types of vulnerability assessment
Several types of vulnerability assessments can be conducted, including:Network-Based Vulnerability Assessment.Application-Based Vulnerability Assessment.Host-Based Vulnerability Assessment.Wireless Network Vulnerability Assessment.Physical Vulnerability Assessment.Social Engineering Vulnerability Assessment.
What is the process of vulnerability analysis
A vulnerability assessment is the testing process used to identify and assign severity levels to as many security defects as possible in a given timeframe. This process may involve automated and manual techniques with varying degrees of rigor and an emphasis on comprehensive coverage.
What is the vulnerability assessment strategy
There are several types of vulnerability assessment: Network-based assessment: Used to identify possible network security issues and can detect vulnerable systems on wired and wireless networks. Host-based assessment: Used to locate and identify vulnerabilities in servers, workstations, and other network hosts.
Which are the 4 key drivers of vulnerability
4 key drivers of customer vulnerabilityHealth. Conditions or illnesses that affect one's ability to complete day-to-day tasks, both mentally and physically.Life Events. Such as bereavement, job loss or relationship breakdown.Resilience. Low ability to withstand and manage financial or emotional shocks.Capability.
What are the 4 key drivers of vulnerability categories
health – health conditions or illnesses that affect the ability to carry out day to day tasks • life events – major life events such as bereavement or relationship breakdown • resilience – low ability to withstand financial or emotional shocks • capability – low knowledge of financial matters or low confidence in …
What are the 5 types of vulnerable
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 5 steps of vulnerability management
There are five main stages in the vulnerability management cycle include:Assess.Prioritize.Act.Reassess.Improve.
What are the three stages of vulnerability
In the PAR model, there are three stages of vulnerability. These are: Root Causes, Dynamic Pressures, and Unsafe Conditions. Together, they are called The Progression of Vulnerability.
What are the four steps to vulnerability management
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.
What are the 4 requirements of every vulnerability management program
Let us examine briefly each stage and see how Tripwire can help you.The First Stage: The Scanning Process. The first step is to identify the criticality of your organization's assets.Stage Two: Asset Discovery and Inventory.Stage Three: Vulnerability Detection.Stage Four: Reporting and Remediation.How Tripwire Helps.
What are the 4 characteristics of vulnerability
Vulnerability is more widespread than many of us realise. There are four characteristics to be aware of: poor health, experiencing a negative life event, having low financial resilience and having low capability. It's potentially a huge disadvantage as it can lead you to make poor financial decisions.
What are the 4 types of vulnerability in disaster management
In the table below four different types of vulnerability have been identified, Human-social, Physical, Economic and Environmental and their associated direct and indirect losses.
What are the 6 stages of security risk management
The stages defined in the slide are identification, asset management protection, technology implementation, security control assessment, authorization and risk monitoring.
What are the 4 factors of disaster management
Preparedness, Response, Recovery & Prevention/MitigationPreparedness – First, prepare to protect yourself, others and items of great importance in the event an emergency/disaster occurs.Response – When there is an actual occurrence, administer first aid or get medical attention for victims if necessary.
What are the 4 key disaster characteristics
Many of those who choose not to define a disaster by its origin/cause define it according to its characteristics. These may include: (1) length of forewarning, (2) magnitude of impact, (3) scope of impact, and (4) duration of impact.
What are the 5 stages of security
Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES]Identify.Protect.Detect.Respond.Recover.
What are the 4 phases of emergency management
However, preparedness is only one phase of emergency management. Current thinking defines four phases of emergency management: mitigation, preparedness, response, and recovery.
What are the 4 C’s of disaster recovery
Aligned with the founding principles of the National Voluntary Organizations Active in Disaster (National VOAD), VALs are committed to fostering the four Cs: communication, coordination, collaboration, and cooperation.
What are the 4 types of disaster
Types of DisasterGeophysical (e.g. Earthquakes, Landslides, Tsunamis and Volcanic Activity)Hydrological (e.g. Avalanches and Floods)Climatological (e.g. Extreme Temperatures, Drought and Wildfires)Meteorological (e.g. Cyclones and Storms/Wave Surges)Biological (e.g. Disease Epidemics and Insect/Animal Plagues)
What are the 4 pillars of disaster risk
The 4 Phases of Disaster ManagementMitigation.Preparedness.Response.Recovery.
What are the 4 security types
Types#1 – Equity securities. It refers to a stock – common or preferred, held by investors, who are referred to as equity shareholders.#2 – Debt securities. Debt instruments are a type of loan that carries a low risk.#3 – Hybrid securities.#4 – Derivatives.Example #1.Example #2.
What are the 4 principles of security
The Four basic security principles are discussed below with example, respectively.Confidentiality.Integrity.Availability.Accountability.Conclusion.
What are the 5 different phases in emergencies
Prevention, mitigation, preparedness, response and recovery are the five steps of Emergency Management.Prevention. Actions taken to avoid an incident.Mitigation.Preparedness.Response.Recovery.
What are the four core elements of an emergency
Four Core Elements to Incorporate into an Emergency Preparedness PlanRisk Assessment and Planning. When developing an emergency plan, organizations must complete an evaluation of the potential risks they could face and create plans to address them.Policies and Procedures.Communication Plan.Training and Testing.