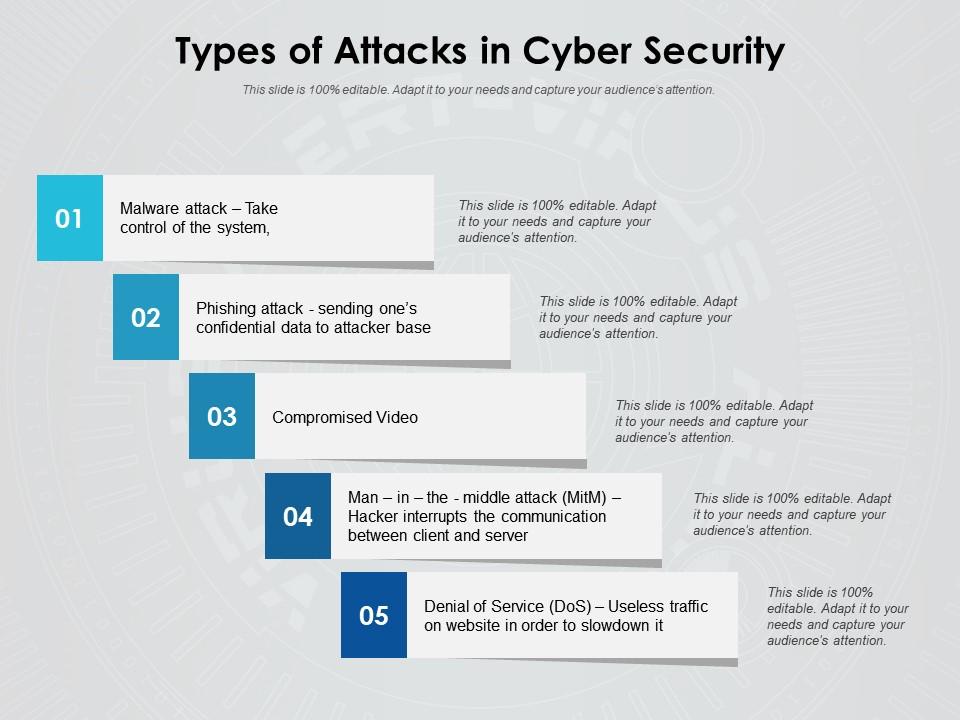
What are the 5 main types of network attack
What are the Common Types of Network AttacksUnauthorized access. Unauthorized access refers to attackers accessing a network without receiving permission.Distributed Denial of Service (DDoS) attacks.Man in the middle attacks.Code and SQL injection attacks.Privilege escalation.Insider threats.
What are the types of network security attacks
There are two main types of network attacks: passive and active. In passive network attacks, malicious parties gain unauthorized access to networks, monitor, and steal private data without making any alterations. Active network attacks involve modifying, encrypting, or damaging data.
What are 3 different attacks on a network
The different types of network attacks are as follows:Password-Based Attacks.Man-in-the-Middle Attack.Close-in Attack.Identity Spoofing.Compromised-Key Attack.Application-Layer Attack.Passive Attack.Active Attack.
What is a network attack in security
An attack is an information security threat that involves an attempt to obtain, alter, destroy, remove, implant or reveal information without authorized access or permission. It happens to both individuals and organizations.
What is the most common type of network attack
Malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any other type of malware attack that leverages software in a malicious way.
What are the five steps of a network attack
Cyber Security: Understanding the 5 Phases of IntrusionPHASE 1 OF INTRUSION: RECONNAISSANCE.PHASE 2: INITIAL EXPLOITATION.PHASE 3: ESTABLISH PERSISTENCE.PHASE 4: MOVE LATERALLY.PHASE 5: COLLECT, EXFIL, AND EXPLOIT.ATTACKER'S FOCUS: GET IN, GET OUT.HOW TO MONITOR YOUR NETWORK LOGS WITH GRAYLOG.
What are the nine types of network security
The following are some commonly used types of network security tools and software:Access control.Antivirus and antimalware.Application security.Behavioral analytics.Cloud security.Data loss prevention (DLP).Email security.Firewall.
What is active and passive attacks in network security
Active and passive attacks are the two forms of attacks connected to security. An attacker tries to change the content of the messages in an active attack. An attacker monitors the communications and duplicates them in a passive attack.
What are the common types of attacks
What are the 10 Most Common Types of Cyber AttacksMalware.Denial-of-Service (DoS) Attacks.Phishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.
What are the two basic types of attacks
There are two types of attacks that are related to security namely passive and active attacks. In an active attack, an attacker tries to modify the content of the messages. In a passive attack, an attacker observes the messages and copies them.
What is the most common network attack
Malware. Malware — or malicious software — is any program or code that is created with the intent to do harm to a computer, network or server.Denial-of-Service (DoS) Attacks.Phishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.
What are the two main types of network attack
Types of Network Security AttacksActive: Attackers gain unauthorized access to the network and then modify data (say, via encryption) to compromise it and affect its usability and value.Passive: Cybercriminals attack networks to monitor or steal data without making any changes to it.
What is network attack examples
For example, a user may be running a vulnerable network application to which an attacker can send malware. In some cases, without any user intervention, the application may accept the malware from the Internet and run it, creating a worm.
What are the 6 phases of a cyber attack
cyber incident response plan has 6 phases, namely, Preparation, Identification, Containment, Eradication, Recovery and Lessons Learned.
What are the 4 steps involved in a hacker attack
The Five Phases of Ethical HackingReconnaissance. Reconnaissance, also known as the preparatory phase, is where the hacker gathers information about a target before launching an attack and is completed in phases prior to exploiting system vulnerabilities.Scanning.Gain Access.Maintain Access.Cover Tracks.
What are the 7 types of network
7 Types of Computer Networks ExplainedPERSONAL AREA NETWORK (PAN) This is the smallest and most basic network that you'll find.LOCAL AREA NETWORK (LAN)WIRELESS LOCAL AREA NETWORK (WLAN)METROPOLITAN AREA NETWORK (MAN)WIDE AREA NETWORK (WAN)STORAGE AREA NETWORK (SAN)VIRTUAL PRIVATE NETWORK (VPN)
What are the 4 types of networking
Types of NetworksPAN (Personal Area Network)LAN (Local Area Network)MAN (Metropolitan Area Network)WAN (Wide Area Network)
What is the difference between active and passive attacks
In an Active attack, an attacker tries to modify the content of the messages. On the other hand, in a Passive attack, an attacker observes the messages, copy them and may use them for malicious purposes. Read this article to find out more about Active and Passive attacks and how they are different from each other.
What are the examples of active attacks and passive attacks
Example of an active attack: Hijacking session, Impersonating the user. Examples of passive attacks: Tapping, and decryption of encrypted messages.
What are 4 ways to protect yourself from cyber attacks
4 Things You Can Do To Keep Yourself Cyber SafeTurn on Multifactor Authentication. Implement multifactor authentication on your accounts and make it significantly less likely you'll get hacked.Update Your Software. Update your software.Think Before You Click. Think before you click.Use Strong Passwords.
What are basic attacks
A basic attack (also called a standard, normal, or auto attack) is the default means by which a unit deals damage.
What are 3 common WIFI attacks
The most common types of wireless network attacks are the following:packet sniffing.rogue access points.Wi-Fi phishing and evil twins.spoofing attacks.encryption cracking.MitM attacks.DoS attacks.Wi-Fi jamming.
What is an example of an active attack
An attack on the authentication protocol where the attacker transmits data to the claimant, Credential Service Provider (CSP), verifier, or Relying Party (RP). Examples of active attacks include man-in-the-middle (MitM), impersonation, and session hijacking.
What are the 7 stages of cyber security
7 stages of the cyber attack lifecycleReconnaissance. The preliminary stage of any cyber attack sees the threat actor gathering intelligence and research on their target(s).Weaponisation.Delivery.Exploitation.Installation.Command and control.Actions on objectives.
What are the 7 steps cyber incident response
7 Phases of Incident ResponsePreparation. It's nearly impossible to create a well-organized response to a cybersecurity threat in the moment.Identification. All phases of an incident response plan are important, however, identification takes precedence.Containment. Don't panic!Eradication.Recovery.Learning.Re-testing.