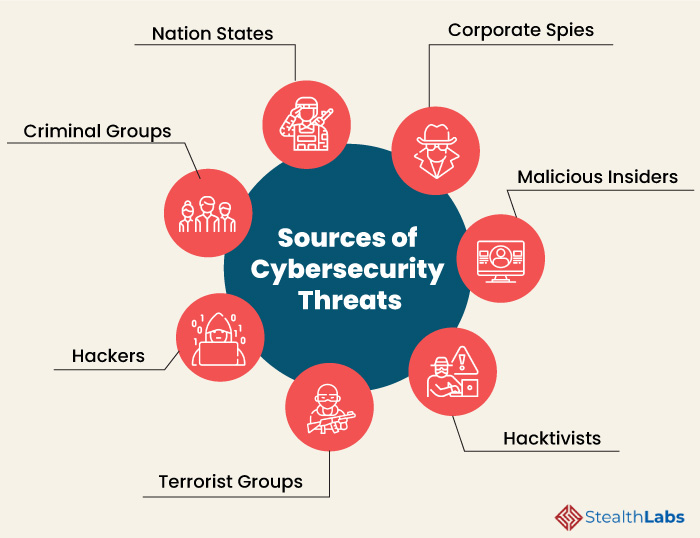
What are the major threats to cyber security
Common categories of cyber threats include malware, social engineering, man in the middle (MitM) attacks, denial of service (DoS), and injection attacks—we describe each of these categories in more detail below.
What are the 5 types of cyber attacks
What are the 10 Most Common Types of Cyber AttacksMalware.Denial-of-Service (DoS) Attacks.Phishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.
What are 5 threats to information security and provide examples
Top 10 Threats to Information SecurityTechnology with Weak Security. New technology is being released every day.Social Media Attacks.Mobile Malware.Third-party Entry.Neglecting Proper Configuration.Outdated Security Software.Social Engineering.Lack of Encryption.
What are the 5 essential elements of cyber security
5 Key Elements of a Modern Cybersecurity FrameworkIdentify.Protect.Detect.Respond.Recover.
What are the 8 common cyber threats
Inside the Top Cyber ThreatsRansomware. Ransomware is malware designed to use encryption to force the target of the attack to pay a ransom demand.Malware.Fileless Attacks.Phishing.Man-in-the-Middle (MitM) Attack.Malicious Apps.Denial of Service Attack.Zero-Day Exploit.
What are the 4 main types of vulnerability in cyber security
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What are the 4 types of threats
Threats can be classified into four different categories; direct, indirect, veiled, conditional. A direct threat identifies a specific target and is delivered in a straightforward, clear, and explicit manner.
What are the 3 major types of cyber security
The 3 major types of cyber security are network security, cloud security, and physical security. Your operating systems and network architecture make up your network security. It can include network protocols, firewalls, wireless access points, hosts, and servers.
What are the 7 domains of cyber security
Security Associate Director, Red Sea…User Domain: The user is the first domain and represents the end-user who accesses the organization's IT infrastructure from either inside the network or outside network.Workstation domain.LAN domain:LAN to WAN domain.WAN domain:Remote access domain.System and application domains.
What are the 4 elements of cyber security
Different Elements of Cybersecurity:
Disaster Recovery Planning. Network Security. End-user Security. Operational Security.
What are the 4 factors of vulnerability
There are many aspects of vulnerability, arising from various physical, social, economic, and environmental factors.
What are the 4 levels of vulnerability
The four continuous stages of identification, prioritization, remediation, and reporting are essential for an effective vulnerability management process. A vulnerability is a flaw or weakness in a system that, if exploited, would allow a user to gain unauthorized access to conduct an attack.
What are the 4 levels of cyber security
Level 1: Basic safeguarding of FCI (Federal Contract Information) Level 2: Transition step to protect CUI. Level 3: Protecting CUI. Levels 4-5: Protecting CUI and reducing risk of APT.
What are the 7 layers of cyber security
The 7 layers of cyber security are:Physical security.Network security.Perimeter security.Endpoint security.Application Security.Data security.User education.
What are the 6 cybersecurity concepts
The standards-based content will reinforce the six GenCyber Cybersecurity Concepts (Confidentiality, Integrity, Availability, Thinking like an Adversary, Defense in Depth, and Keeping It Simple) through activities and lab exercises.
What are the 5 vulnerable people
Some common examples of vulnerable groups in society include: elderly people, people with low incomes, uninsured people, homeless people, racial or ethnic minorities, people in prison, migrant workers, pregnant women, people in the LGBTQIA community, and children.
What are the 6 vulnerable groups
Vulnerable groupsWomen.People with children.Children.Young people.Older people.Pregnant people.People with disability and impairment.People with mental illness.
What are the 7 types of cyber security
It can be divided into seven main pillars:Network Security. Most attacks occur over the network, and network security solutions are designed to identify and block these attacks.Cloud Security.Endpoint Security.Mobile Security.IoT Security.Application Security.Zero Trust.
What are the 7 stages of cyber security
7 stages of the cyber attack lifecycleReconnaissance. The preliminary stage of any cyber attack sees the threat actor gathering intelligence and research on their target(s).Weaponisation.Delivery.Exploitation.Installation.Command and control.Actions on objectives.
What are the 4 vulnerable areas
Four areas of the body are particularly sensitive: the eyes, nose, neck and knees. Gouge, poke or scratch your attacker's eyes to inflict pain and blur vision. Strike up under your attacker's nose with the bottom of your palm if you're being approached from in front of you.
What are the 10 vulnerable groups
The vulnerable groups that face discrimination include- Women, Scheduled Castes (SC), Scheduled Tribes (ST), Children, Aged, Disabled, Poor migrants, People living with HIV/AIDS and Sexual Minorities.
What are the 6 phases of cyber security
cyber incident response plan has 6 phases, namely, Preparation, Identification, Containment, Eradication, Recovery and Lessons Learned. Any organisation that is serious about its cybersecurity requires a solid cyber incident response plan.
What are the 13 strands of vulnerability
Dorset Police outline 13 strands of vulnerability which is recognised nationally as:adults at risk.child abuse and neglect.female genital mutilation.honour based abuse.child sexual exploitation.human trafficking and modern day slavery.managing offenders.prostitution.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What are the 4 main types of security vulnerability
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.