What are type of vulnerability scanners
Among the different types are the following:Internal scanning.External scanning.Authenticated scanning.Unauthenticated scanning.Assessment scanning.Discovery scanning.Compliance scanning.Host-based scanning.
What is the most common type of vulnerability scan
application vulnerability scanner
One of the most widely used scanner types is the application vulnerability scanner. Its primary purpose is to scan an organization's web and mobile applications across the network to find vulnerabilities and potential exploits.
What is the use of vulnerability scanner
A vulnerability scanner enables organizations to monitor their networks, systems, and applications for security vulnerabilities. Most security teams utilize vulnerability scanners to bring to light security vulnerabilities in their computer systems, networks, applications and procedures.
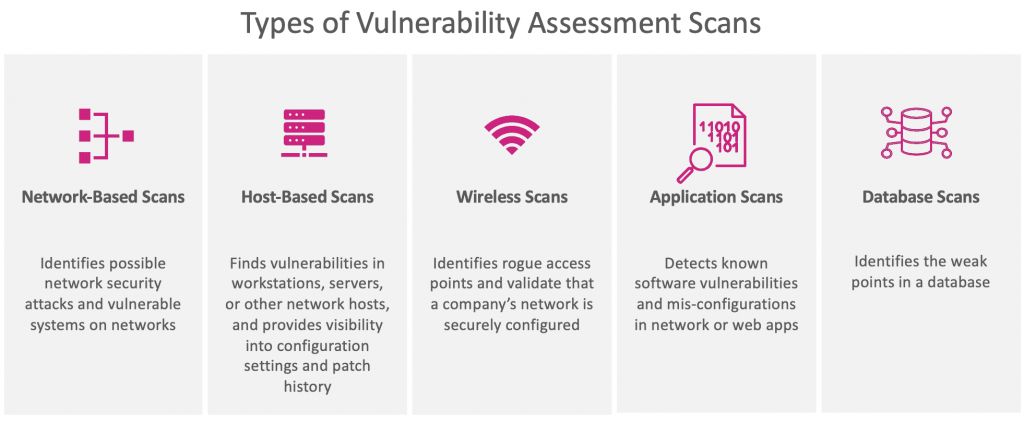
What are the different types of cyber security scans
The most common types of cybersecurity scans today are virus/malware scans, network port scans, penetration tests, rogue access point scans, program bug scans, vulnerability scans, and user permission-level scans.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What are the 5 types of scanner
Types of ScannerFlatbed Scanners. The most popular type of optical scanner is a flatbed scanner, which scans documents on a flat surface.Sheetfed Scanners. A scanner that allows the only paper to be scanned, known as sheetfed scanners.Handheld Scanner.Drum Scanner.Photo Scanner.Film Scanner.Portable Scanners.
What are the 4 types of vulnerability
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
What are the three most common types of scanners
What are 3 types of scanners There are three types of scanners available: drum scanner, flatbed, and handheld scanners. The publishing industry primarily uses drum scanners to print high-quality images, while flatbed scanners are generally used in schools and offices.
What is the first vulnerability scanner
This takes us all the way back to the late 90s and the development of the Security Administrator Tool for Analyzing Networks (SATAN). SATAN was one of the first vulnerability scanners that was created to address network vulnerabilities, as more computers became reliant on the internet.
What are the different types of scanner in detail
What types of scanners are availableFlatbed scanners are the most common type of scanner.Sheetfed scanners are designed to scan documents fed into the scanner one at a time.Handheld scanners are portable scanners that are smaller than flatbed scanners.
What are the three most common types of scanners what type of data does each scan
There are three types of scanners available: drum scanner, flatbed, and handheld scanners. The publishing industry primarily uses drum scanners to print high-quality images, while flatbed scanners are generally used in schools and offices. On the other hand, libraries and shopping malls make use of handheld scanners.
What are the 3 factors that can create vulnerability
Vulnerability relates to a number of factors, including:Physical factors. e.g. poor design and construction of buildings, unregulated land use planning, etc.Social factors.Economic factors.Environmental factors.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 4 parts of a scanner
| Item | Purpose | |
|---|---|---|
| 1. | Stepper Motor | Powers the transmission belt |
| 2. | Logic Board | Relays information to and from the scanner and the computer |
| 3. | Scanning Unit/Carriage | Contains a light source and CCD sensors |
| 4. | Transmission Belt | Moves the scanning unit across the image |
Are there four types of scanner
The Computer Revolution/Peripherals/Types of Scanners
The information will include; cost, and how its used The four common scanner types are: Flatbed, Sheet-fed, Handheld, and Drum scanners. Flatbed scanners are some of the most commonly used scanners as it has both home and office functions.
What are the different types of scanners
Types of ScannerFlatbed Scanners. The most popular type of optical scanner is a flatbed scanner, which scans documents on a flat surface.Sheetfed Scanners. A scanner that allows the only paper to be scanned, known as sheetfed scanners.Handheld Scanner.Drum Scanner.Photo Scanner.Film Scanner.Portable Scanners.
What are the three functions of scanner
The scanner's primary function is to scan or take pictures of a document, digitize the information, display it on your screen, and store it on your connected computer.
What are the two most common types of vulnerability scans
Credentialed and non-Credentialed scans (also respectively referred to as authenticated and non-authenticated scans) are the two main categories of vulnerability scanning. Non-credentialed scans, as the name suggests, do not require credentials and do not get trusted access to the systems they are scanning.
What is CVE vulnerability scan
The Common Vulnerabilities and Exposures (CVE) system identifies all vulnerabilities and threats related to the security of information systems. To do this, a unique identifier is assigned to each vulnerability. Test for free the CVE Scanner Request a demo.
What are the 4 different types of scans
This includes X-rays, a CT scan, an MRI scan and ultrasound scans.Angiography. Information on angiograms, a type of X-ray used to examine blood vessels.CT scan. Learn about CT scans and when they're used.Echocardiogram.Electrocardiogram (ECG)MRI scan.PET scan.Ultrasound scan.X-ray.
What are the 3 components of vulnerability assessment
There are three dimensions of vulnerability: exposure, sensitivity, and adaptive capacity.
What are the 4 main types of security vulnerability
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What are the 4 levels of vulnerability
The four continuous stages of identification, prioritization, remediation, and reporting are essential for an effective vulnerability management process. A vulnerability is a flaw or weakness in a system that, if exploited, would allow a user to gain unauthorized access to conduct an attack.
What are different types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What is CVE and CVSS
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.