What are the different types of cyber security scans
The most common types of cybersecurity scans today are virus/malware scans, network port scans, penetration tests, rogue access point scans, program bug scans, vulnerability scans, and user permission-level scans.
What is SCaN in security
What is SCaN See, Check and Notify (SCaN) aims to help businesses and organisations maximise safety and security using their existing resources. Your people are your biggest advantage in preventing and tackling a range of threats, including criminal activity, unlawful protest and terrorism.
What are the two types of cyber security
The Different Types of CybersecurityNetwork Security. Most attacks occur over the network, and network security solutions are designed to identify and block these attacks.Cloud Security.Endpoint Security.Mobile Security.IoT Security.Application Security.Zero Trust.
What are two types of scanners that can be used to scan documents into digital format
Modern scanners come in handheld, feed-in and flatbed types and are for scanning black-and-white only or color. Flatbed scanners are the most common type of scanner. They are called "flatbed" because the document is placed on a flat surface for scanning.
What is vulnerability scan
Vulnerability scanning is the process of discovering, analyzing, and reporting on security flaws and vulnerabilities. Vulnerability scans are conducted via automated vulnerability scanning tools to identify potential risk exposures and attack vectors across an organization's networks, hardware, software, and systems.
What is the basic vulnerability scan
Vulnerability scanning is the process of identifying security weaknesses and flaws in systems and software running on them. This is an integral component of a vulnerability management program, which has one overarching goal – to protect the organization from breaches and the exposure of sensitive data.
What is Level 2 cyber security
About this qualification
The purpose of the Level 2 Certificate in Cyber Security is to provide learners with sector awareness. It will do this by introducing the knowledge and understanding in roles and issues relating to Cyber Security.
What is Cyber Security 2
Cybersecurity is the protection of internet-connected systems such as hardware, software and data from cyberthreats. The practice is used by individuals and enterprises to protect against unauthorized access to data centers and other computerized systems.
What are the two types of scanning method
Scanning has three types:Port scanning – used to list open ports and services.Network scanning – used to list IP addresses.Vulnerability scanning – used to discover the presence of known vulnerabilities.
What are the two scanning methods
Interlaced scanning and progressive scanning are the two image scanning techniques available today for reading and displaying information produced by image sensors. Interlaced scanning is used mainly in CCDs. Progressive scanning is used in either CCD or CMOS sensors.
What is CVE vulnerability scan
The Common Vulnerabilities and Exposures (CVE) system identifies all vulnerabilities and threats related to the security of information systems. To do this, a unique identifier is assigned to each vulnerability. Test for free the CVE Scanner Request a demo.
What is the difference between internal and external vulnerability scan
An internal scan is conducted within a company's network to ensure safety inside of the network, while an external scan is completed outside of the company's network to ensure there are no ways for a hacker to get into the network. What Are The Differences Between External And Internal Vulnerability Scans
Which two are software vulnerability scanners
Top 10 Vulnerability Scanner SoftwareWiz.Microsoft Defender for Cloud.Tenable Nessus.Orca Security.PingSafe.Trend Micro Hybrid Cloud Security.Snyk.Intruder.
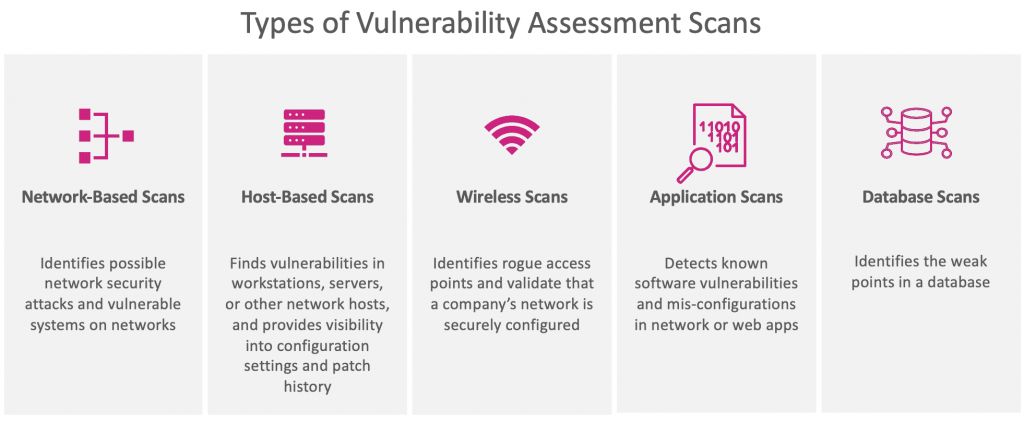
Which of the following is a type of vulnerability scan
The types of vulnerability assessments that we will look at are host-based scans, network scanning, database scanning, cloud vulnerability scanning, and application vulnerability scans.
What is a Level 2 security analyst
Information Security Analyst II completes tasks designed to ensure security of the organization's systems and information assets. Protects against unauthorized access, modification, or destruction and develops IT security policies and standards.
What are two types of cyber security attacks
What are the 10 Most Common Types of Cyber AttacksMalware.Denial-of-Service (DoS) Attacks.Phishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.
What are the three types of scans
CT scans, MRIs and X-rays are all diagnostic tools that allow doctors to see the internal structures of the body. They create images using various forms of electromagnetic energy such as radio waves and X-rays.
What is the difference between vulnerability scan and discovery scan
By its nature, full vulnerability scanning can be very noisy because you are poking and prodding at every possible corner of the network. On the other hand, discovery vulnerability scanning is only used to triage a network. Discovery scanning can be a quieter process depending on which tools you use.
What is 2 sided scanning
Duplex scanning is a feature of some computer scanners, and multifunction printers (MFPs) that support duplex printing. A duplex scanner can automatically scan a sheet of paper on both sides. Scanners without this capability can only scan both sides of a sheet of paper by reinserting it manually the other way up.
What is CVE and CVSS
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
What is CVSS vs CVE
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
What are internal vulnerability scans
Internal vulnerability scanning specifically examines an organization's security profile from the perspective of an insider or someone who has access to systems and networks behind the organization's external security perimeter.
What is the difference between active and passive vulnerability scanners
Active scanners directly interact with endpoints by querying them with test traffic packets and reviewing each response to find vulnerabilities. Passive scanners “silently” glean network data to detect weaknesses without actively interacting with endpoints.
What are the different types of vulnerability testing
Several types of vulnerability assessments can be conducted, including:Network-Based Vulnerability Assessment.Application-Based Vulnerability Assessment.Host-Based Vulnerability Assessment.Wireless Network Vulnerability Assessment.Physical Vulnerability Assessment.Social Engineering Vulnerability Assessment.
What is the most common type of vulnerability scan
application vulnerability scanner
One of the most widely used scanner types is the application vulnerability scanner. Its primary purpose is to scan an organization's web and mobile applications across the network to find vulnerabilities and potential exploits.