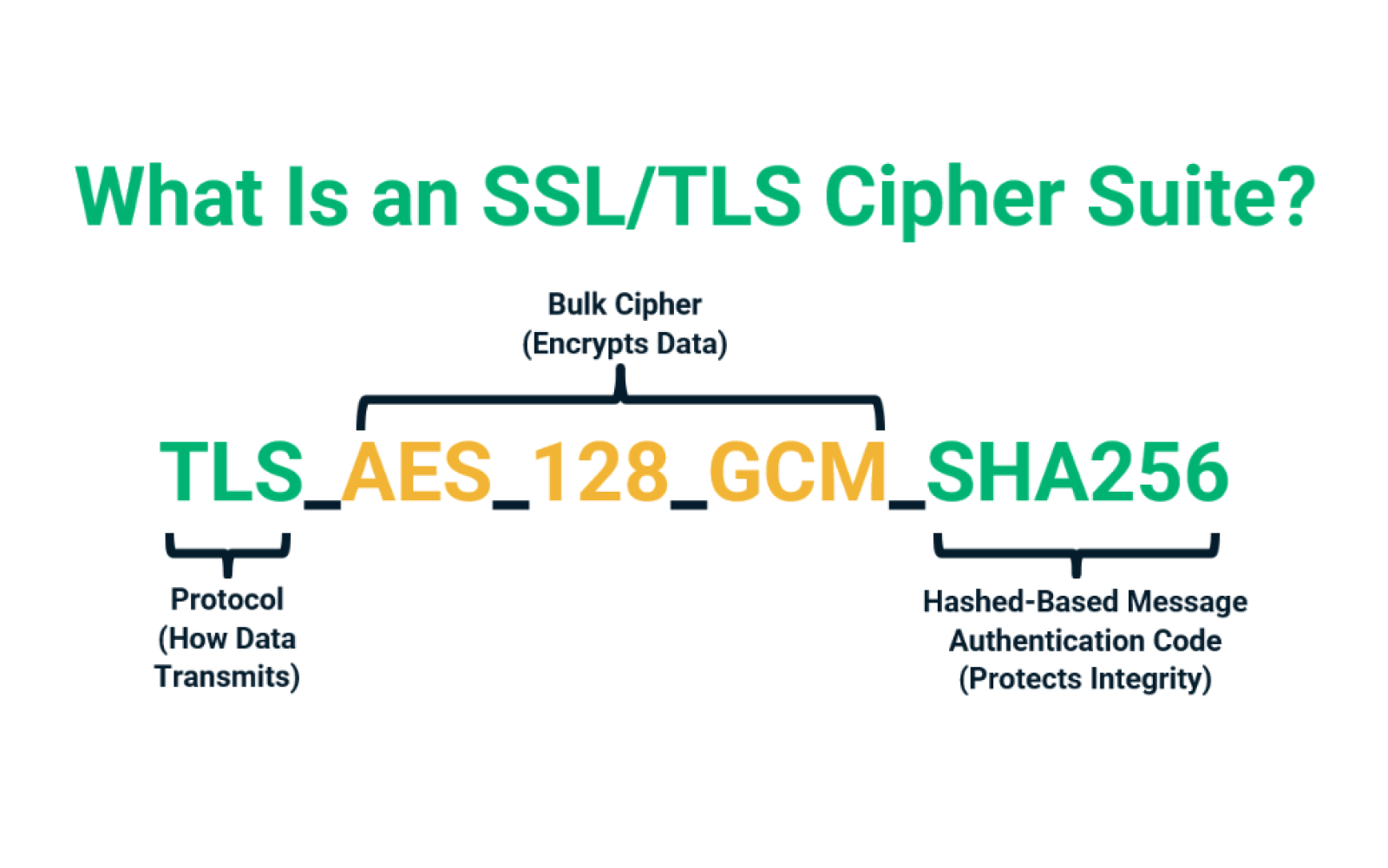
What are the weak TLS 1.2 cipher suites
A cipher suite is identified as obsolete when one or more of the mechanisms is weak. Especially weak encryption algorithms in TLS 1.2 are designated as NULL, RC2, RC4, DES, IDEA, and TDES/3DES; cipher suites using these algorithms should not be used9.
Which TLS versions are insecure
SSL version 1 and 2, SSLv2 and SSLv3 are now insecure. It is also recommended to phase out TLS 1.0 and TLS 1.1. We recommend that you disable SSLv2, SSLv3, TLS 1.0 and TLS 1.1 in your server configuration so that only the newer TLS protocols can be used. It is recommended to only enable TLS 1.3 for maximum security.
What is the vulnerability in tls1 1
The web server supports encryption through TLS 1.1, which was formally deprecated in March 2021 as a result of inherent security issues. When aiming for Payment Card Industry (PCI) Data Security Standard (DSS) compliance, it is recommended to use TLS 1.2 or higher instead.
Which TLS versions are most secure
In a nutshell, TLS 1.3 is faster and more secure than TLS 1.2. One of the changes that makes TLS 1.3 faster is an update to the way a TLS handshake works: TLS handshakes in TLS 1.3 only require one round trip (or back-and-forth communication) instead of two, shortening the process by a few milliseconds.
Which TLS ciphers are weak
Your organization should avoid TLS versions 1.1 and below and RC4 encryption, as there have been multiple vulnerabilities discovered that render it insecure. The best way to ensure strong transport layer security is to support TLS 1.3, which is the most secure and up-to-date version of TLS.
What ciphers are weak
Weak ciphers are generally known as encryption/ decryption algorithms that use key sizes that are less than 128 bits (i.e., 16 bytes … 8 bits in a byte) in length.
Why is TLS 1.2 insecure
TLS 1.2 uses a complex cipher suite that includes support for encryption algorithms and ciphers with known cryptographic weaknesses. While the complexity results in the poor choice of the cipher suite, support for weak security mechanisms amplifies the risks of encryption attacks.
Which TLS versions are weak
Your organization should avoid TLS versions 1.1 and below and RC4 encryption, as there have been multiple vulnerabilities discovered that render it insecure. The best way to ensure strong transport layer security is to support TLS 1.3, which is the most secure and up-to-date version of TLS.
Why is TLS 1.2 not secure
In TLS 1.2 and earlier versions, the use of ciphers with cryptographic weaknesses had posed potential security vulnerabilities. TLS 1.3 includes support only for algorithms that currently have no known vulnerabilities, including any that do not support Perfect Forward Secrecy (PFS).
Is TLS 1.2 not secure
TLS 1.2 is more secure than the previous cryptographic protocols such as SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1. Essentially, TLS 1.2 keeps data being transferred across the network more secure.
What are weak TLS ciphers
A weak cipher is defined as an encryption/decryption algorithm that uses a key of insufficient length. Using an insufficient length for a key in an encryption/decryption algorithm opens up the possibility (or probability) that the encryption scheme could be broken (i.e. cracked).
What ciphers should be disabled
You should also disable weak ciphers such as DES and RC4. DES can be broken in a few hours and RC4 has been found to be weaker than previously thought. In the past, RC4 was advised as a way to mitigate BEAST attacks.
Are RSA ciphers weak
All in all, they were able to break 12,934 keys. In other words, if used carelessly, RSA encryption provides less than 99.8% security.
Is 256 AES a weak cipher
AES 128 uses 10 rounds, AES 192 uses 12 rounds, and AES 256 uses 14 rounds. The more rounds, the more complex the encryption, making AES 256 the most secure AES implementation. It should be noted that with a longer key and more rounds comes higher performance requirements.
Is TLS 1.2 vulnerable to poodle
Any server that supports SSL 3.0 and older versions of TLS is vulnerable to a POODLE attack. Modern versions of TLS are safe, and today's browsers block sites that use old versions of TLS (1.0, 1.1). A server configured to support only newer protocols (TLS 1.2, 1.3) prevents the possibility of a POODLE attack.
Does TLS 1.2 use AES 256
You can mount a file system so that all NFS traffic is encrypted in transit using Transport Layer Security 1.2 (TLS) with an industry-standard AES-256 cipher.
What are examples of weak encryption
Encryption algorithms such as TripleDES and hashing algorithms such as SHA1 and RIPEMD160 are considered to be weak. These cryptographic algorithms do not provide as much security assurance as more modern counterparts.
What are weak ciphers in use
In NIST parlance, weak ciphers are either:Deprecated (the use of the algorithm and key length is allowed, but the user must accept some risk) or;Disallowed (algorithm or key length is no longer allowed for the indicated use).
Is RSA stronger than AES
In terms of speed, RSA encryption is faster than AES encryption. This is because RSA encryption uses a smaller key, allowing it to quickly process data. However, AES encryption is more secure as it uses a longer key and is more difficult to crack.
Is 128 AES strong or weak
A machine that can crack a DES key in a second would take 149 trillion years to crack a 128-bit AES key. Hence, it is safe to say that AES-128 encryption is safe against brute-force attacks. AES has never been cracked yet and it would take large amounts of computational power to crack this key.
Is TLS 1.2 vulnerable to SWEET32
The SWEET32 (Birthday Attack) is a Medium level vulnerability which is prevalent in TLS 1.0 and TLS 1.1 which support 3DES Encryption. To resolve this issue you should deploy TLS 1.2 as a minimum (the 3DES cypher is dropped by default) and disable vulnerable ciphers.
Is AES128 more secure than AES256
There are three different sizes: 256-bit AES, 192-bit AES and 128-bit AES. The largest size, 256-bit AES, is the most secure, while 128-bit is conversely the least secure of the three.
Should I use 128 or 256 AES encryption
128-bit and 256-bit AES both have their pros and cons. AES-128 is faster and more efficient and less likely to have a full attack developed against it (due to a stronger key schedule). AES-256 is more resistant to brute force attacks and is only weak against related key attacks (which should never happen anyway).
Is DES stronger than AES
AES allows you to choose a 128-bit, 192-bit or 256-bit key, making it exponentially stronger than the 56-bit key of DES. In terms of structure, DES uses the Feistel network which divides the block into two halves before going through the encryption steps.
Which is more secure Diffie Hellman or RSA
Diffie-Hellman is used for secure key exchange, while RSA is used for encryption and decryption. Diffie-Hellman is a symmetric-key algorithm and provides perfect forward secrecy, while RSA is an asymmetric-key algorithm and provides stronger key strength.