How are vulnerabilities defined
A vulnerability is a weakness in an IT system that can be exploited by an attacker to deliver a successful attack. They can occur through flaws, features or user error, and attackers will look to exploit any of them, often combining one or more, to achieve their end goal.
What is vulnerability with example
Vulnerability is the state of being open to injury, or appearing as if you are. It might be emotional, like admitting that you're in love with someone who might only like you as a friend, or it can be literal, like the vulnerability of a soccer goal that's unprotected by any defensive players.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What is vulnerability and types of vulnerability
Vulnerability describes the characteristics and circumstances of a community, system or asset that make it susceptible to the damaging effects of a hazard. There are many aspects of vulnerability, arising from various physical, social, economic, and environmental factors.
How are vulnerabilities identified
Vulnerability identification (testing)
Security analysts test the security health of applications, servers or other systems by scanning them with automated tools, or testing and evaluating them manually.
What is a vulnerability in software
A security flaw, glitch, or weakness found in software code that could be exploited by an attacker (threat source).
What are 5 example of vulnerability
To illustrate the principles above, here are 11 specific examples of vulnerability: Telling someone when they've upset you, respectfully but honestly. Sharing something personal about yourself that you normally wouldn't. Admitting to mistakes you have made in the past.
What is the best example of vulnerability
Examples of vulnerability
Vulnerability will look different for everyone, but here are some common examples Anderson shared: Telling others when they've done something to upset you. Sharing with someone something personal about yourself that you would normally hold back. Having the willingness to feel pride or shame.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 4 stages of identifying vulnerabilities
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.
How do attackers find vulnerabilities
Scanning can be considered a logical extension (and overlap) of active reconnaissance that helps attackers identify specific vulnerabilities. It's often that attackers use automated tools such as network scanners and war dialers to locate systems and attempt to discover vulnerabilities.
What is vulnerability in software and hardware
Hardware vulnerability does not have an immediate impact on security but lives for decades as compared to software. Software vulnerability has a more immediate impact on security but is shorter-lived as compared to hardware.
What are the vulnerabilities of a computer
A computer vulnerability is a flaw in an IT system that an attacker can use to launch a successful assault. They can be in the form of bugs, feature gaps, or user mistakes, and attackers will try to take advantage of any, or all, of them to accomplish their purpose.
What are 3 example of vulnerabilities
Vulnerability Examples
Any susceptibility to humidity, dust, soiling, natural disaster, poor encryption, or firmware vulnerability.
What are 2 examples of vulnerability
11 examples of vulnerabilityTelling someone when they've upset you, respectfully but honestly.Sharing something personal about yourself that you normally wouldn't.Admitting to mistakes you have made in the past.Being willing to feel difficult emotions like shame, grief, or fear.
What are 3 examples of vulnerability
Different types of Security Vulnerabilities:Unpatched Software.Misconfiguration.Weak Credentials.Easy-to-phish-users.Trust Relationship.Compromised Credentials.Malicious Insider.Missing/Poor Encryption.
What are the 3 points of vulnerability
Vulnerability is a weakness which allows an attacker to reduce a system's information assurance. Vulnerability is the intersection of three elements : a system susceptibility or defect, attacker access to the defect, and attacker capability to exploit the defect.
What are the 5 phases of vulnerability assessment
The Five Phases of Penetration Testing. There are five penetration testing phases: reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Let's take a closer look at the 5 Penetration Testing phases.
What are the 3 components of vulnerability assessment
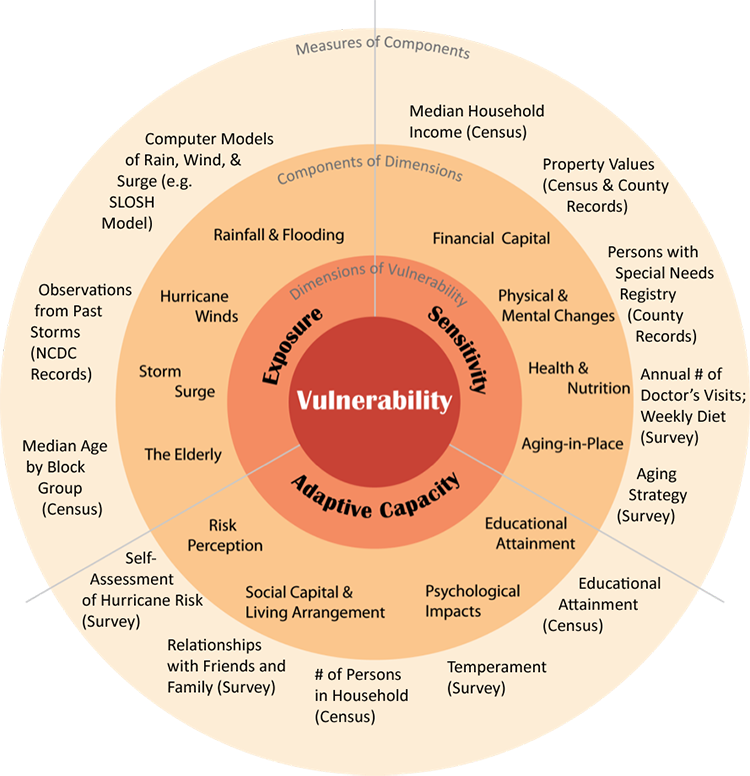
There are three dimensions of vulnerability: exposure, sensitivity, and adaptive capacity.
How do hackers exploit vulnerabilities
Network Scans and Exploitation
A hacker will scan through the digital infrastructure of a company to look for vulnerabilities. Hackers will then usually exploit vulnerabilities in communication channels, database access, and open-source software.
What is vulnerability in a software
A flaw or weakness in system security procedures, design, implementation, or internal controls that could be exercised (accidentally triggered or intentionally exploited) and result in a security breach or a violation of the system's security policy.
What are vulnerabilities in computer software
The most common computer security vulnerabilities include:Bugs.Weak passwords.Software that is already infected with virus.Missing data encryption.OS command injection.SQL injection.Buffer overflow.Missing authorization.
What are vulnerabilities of technology
Technological vulnerability refers to the chance that a technological system may fail due to outside impacts. The usual approaches to studying technological risk are not so useful for studying vulnerabilities of major systems such as energy, communication, or defense.
What are vulnerabilities in software
A software vulnerability is a defect in software that could allow an attacker to gain control of a system.
What are the 5 types of vulnerable
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.