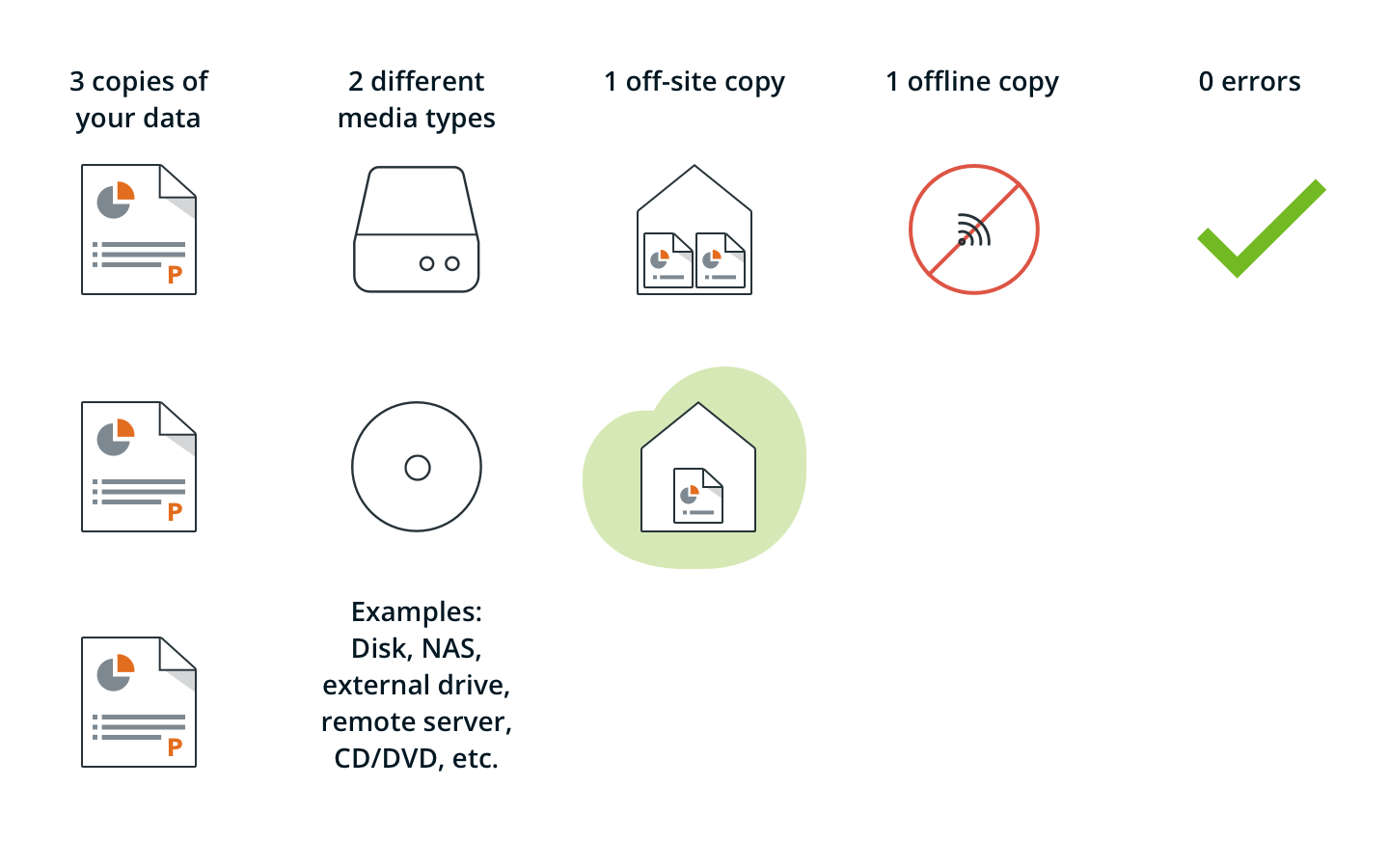
What is the 3-2-1 data rule
The 3-2-1 backup strategy simply states that you should have 3 copies of your data (your production data and 2 backup copies) on two different media (disk and tape) with one copy off-site for disaster recovery. This is depicted in the figure that follows.
What is the 3-2-1 rule in cyber security
The 3-2-1 rule states that in order to be fully protected, organizations must have three copies of their data on two different types of media, with one copy off site. The rule was created when tape was the backup media of choice and predates cloud backups, which explains why it might be due for an upgrade.
What is the 4 3-2-1 rule
One simple rule of thumb I tend to adopt is going by the 4-3-2-1 ratios to budgeting. This ratio allocates 40% of your income towards expenses, 30% towards housing, 20% towards savings and investments and 10% towards insurance.
What is 3-2-1 1 0 backup rule
You should have at least 3 copies of your data, including the production copy. At least 2 different storage media should be used; for instance, a tape and a cloud storage. At least 1 of the copies should be kept off-site, in case your machines are physically damaged.
How can you implement the 3 2 1 rule
3: Create one primary backup and two copies of your data. 2: Save your backups to two different types of media. 1: Keep at least one backup file offsite.
What is meant by the 3 2 1 1 rule
The 3-2-1 backup rule has long been the standard for data protection. It says to keep three copies of your data—one primary and two backups—with two copies stored locally on two formats (network-attached storage, tape, or local drive) and one copy stored offsite in the cloud or secure storage.
What is the 4 3 2 rule security
A 4-3-2 strategy means backups are duplicated and geographically distant to offer protection from events like natural disasters. Backups are also stored on two separate networks, isolating them from production networks in the event they're compromised.
What are the three 3 principles of cyber defense
What are the 3 Principles of Information Security The basic tenets of information security are confidentiality, integrity and availability. Every element of the information security program must be designed to implement one or more of these principles. Together they are called the CIA Triad.
What is an example of a 3-2-1 backup
It means having at least three copies of your data, two local (on-site) but on different media (read: devices), and at least one copy off-site. We'll use “socialsecurity. jpg” as an example for this scenario.
What is meant by the 3-2-1 1 rule
The 3-2-1 backup rule has long been the standard for data protection. It says to keep three copies of your data—one primary and two backups—with two copies stored locally on two formats (network-attached storage, tape, or local drive) and one copy stored offsite in the cloud or secure storage.
What is the 3-2-1 summary strategy example
After, students use the 3-2-1 Summary strategy to list three new discoveries (e.g., “I learned that whales are mammals.”), two interesting facts (e.g., “Whales are not fish!”), and one question (e.g., “Are whale sharks whales or sharks”) in order to synthesize the information they learned and grow inquiries.
What is the 3-2-1 summary strategy
The most common use of 3-2-1 I've seen is in response to a reading or lesson–usually 3 things you learned, 2 things that made you curious or confused, and 1 most important thing you learned or should do with what you've learned.
What is the rule of thumb 1 3 1 3 1 3
Understanding the basic formal of 1/3, 1/3, 1/3 helps here. The basic 'rule of thumb' in service business is that one third is for wages of the staff, one third is for on-costs of employing staff, such as leave, superannuation, space, IT etc. and one third is profit for the business.
What is the rule of 3 to 1
This rule deals with minimizing the audible phasing problems when summing several microphones to mono. The rule states that the source-to-microphone distance of numerous microphones should be three times the distance between the sound source and the nearest microphone.
What is the 90 10 rule for good security
10% of security safeguards are technical. 90% of security safeguards rely on the computer user to adhere to good computing practices. Example: The lock on your car is the 10%. You remembering to close the door, lock the lock, put up the windows, and keep control of your keys is the 90%
What is security 90 10 rule
The 90/10 rule on security states that 90% of cybersecurity is about implementing the right policies and procedures, while the other 10% is about implementing the right technology. People represent your human risk, which is the least managed and mitigated risk in cybersecurity.
What are the three 3 security dimensions
confidentiality, integrity, and availability
The traditional information security objectives are confidentiality, integrity, and availability. Achieving these three objectives does not mean achieving security [1]. It is well known that a formal security policy is a prerequisite of security.
What are the 3 A’s of cyber security
AAA refers to Authentication (to prove identity), Authorization (to give permission) and Accounting (to log an audit trail). It is a framework used to control and track access within a computer network. Common network protocols providing this functionality include TACACS+, RADIUS, and Diameter.
What is the 3-2-1 strategy backup
You may have heard of the 3-2-1 backup strategy. It means having at least three copies of your data, two local (on-site) but on different media (read: devices), and at least one copy off-site. We'll use “socialsecurity.
What are 3 examples of backups
The most common backup types are a full backup, incremental backup and differential backup. Other backup types include synthetic full backups and mirroring.
What is the 3-2-1 strategy in English
The 3-2-1 Exit Slip Strategy
Students write three things they learned in today's lesson. Next, students write two things they liked or two interesting facts about the lesson. Finally, students write one question they still have about the lesson.
What is a 3-2-1 summarizer
Students are asked to write: 3 Facts they learned; 2 Questions they have about the topic; 1 Personal connection they made with the information learned.
What is the 3-2-1 summarizer for independent reading
3-2-1 Organizer
This graphic organizer is a great tool to use with any nonfiction text. Students can summarize three facts that he or she learned, identify two interesting facts, and ask one question they still have after reading.
What is 321 exit strategy
The 3-2-1 exit ticket strategy is a specific style of exit ticket that encourages students to reflect on and summarize their learning, while identifying areas that require more attention. Students are asked to answer three questions.
What is the 1 2 3 rule in business
The 1/3 – 2/3 rule of planning simply says that leaders should take a third of the time until a deadline to make a plan, and then provide their subordinates with the remaining time to develop their own plans and execute them.