What is the highest CVE score
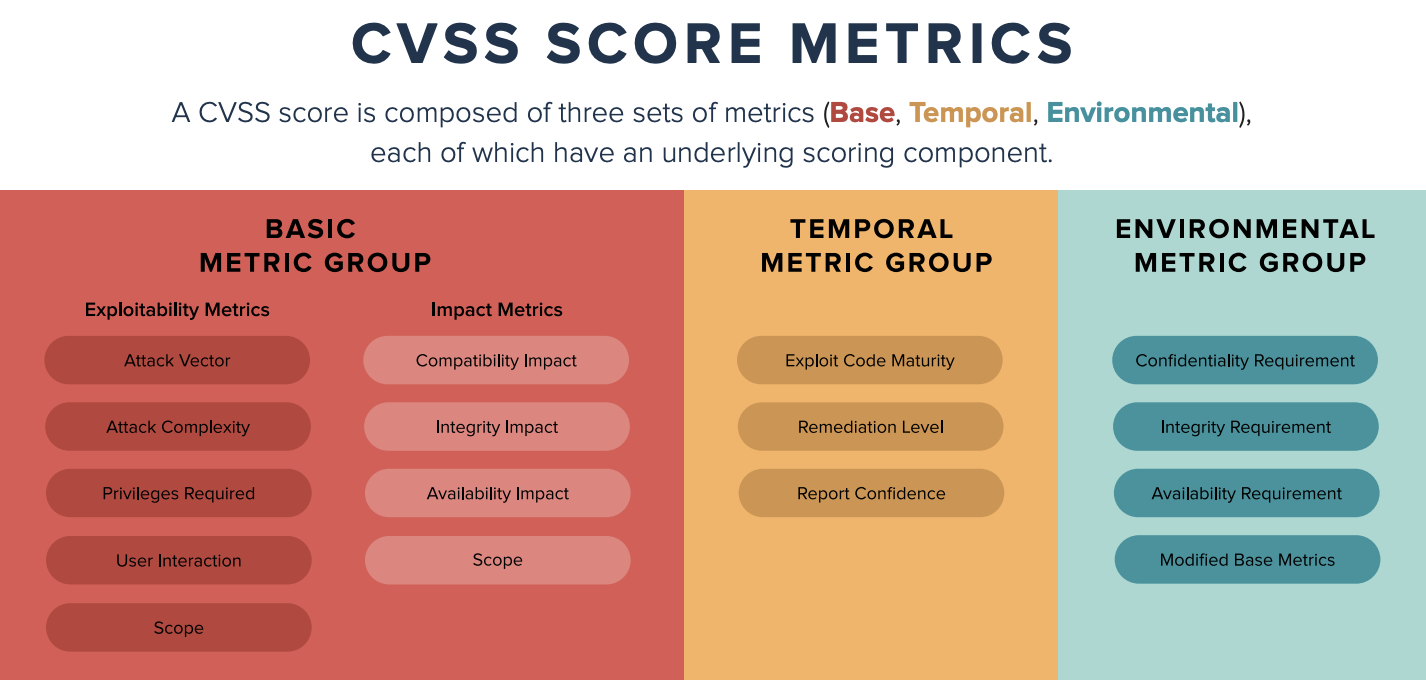
Scores range from 0 to 10, with 10 being the most severe. While many utilize only the CVSS Base score for determining severity, temporal and environmental scores also exist, to factor in availability of mitigations and how widespread vulnerable systems are within an organization, respectively.
What is a CVSS score of 10
CVSS Qualitative Ratings
| CVSS Score | Qualitative Rating |
|---|---|
| 0.1 – 3.9 | Low |
| 4.0 – 6.9 | Medium |
| 7.0 – 8.9 | High |
| 9.0 – 10.0 | Critical |
What CVSS score is high and critical
Table 14: Qualitative severity rating scale
| Rating | CVSS Score |
|---|---|
| Low | 0.1 – 3.9 |
| Medium | 4.0 – 6.9 |
| High | 7.0 – 8.9 |
| Critical | 9.0 – 10.0 |
What is the CVE standard
CVE identifiers are intended for use with respect to identifying vulnerabilities: Common Vulnerabilities and Exposures (CVE) is a dictionary of common names (i.e., CVE Identifiers) for publicly known information security vulnerabilities.
What is CVE number for vulnerabilities
CVE numbers are identifiers for common vulnerabilities and exposures. The MITRE Corporation assigns the CVE numbers and maintains records for these events in the CVE system. You can search the system by using the CVE number to find information about these events.
What is the CVE score of log4j vulnerability
a 10 out of 10
It's described as a zero-day (0 day) vulnerability and rated the highest severity under the Common Vulnerability Scoring System (CVSS; CVE-2021-44228). It was rated a 10 out of 10 on the CVSS, due to the potential impact that it can have if leveraged by attackers.
What is a CVSS score of 4
NVD Vulnerability Severity Ratings
| CVSS v2.0 Ratings | CVSS v3.0 Ratings | |
|---|---|---|
| Severity | Base Score Range | Severity |
| Low | 0.0-3.9 | Low |
| Medium | 4.0-6.9 | Medium |
| High | 7.0-10.0 | High |
What is an acceptable CVSS score
Scores range from 0 to 10.0, with 4.0 or higher indicating failure to comply with PCI standards. Any asset that contains at least one vulnerability with CVSS score of 4.0 or higher is considered non-compliant. And, if at least one asset is non-compliant, the entire organization is considered to be non-compliant.
What is CVSS score v3 range
Table 14: Qualitative severity rating scale
| Rating | CVSS Score |
|---|---|
| Low | 0.1 – 3.9 |
| Medium | 4.0 – 6.9 |
| High | 7.0 – 8.9 |
| Critical | 9.0 – 10.0 |
How are CVEs rated
CVEs are given a rating using the Common Vulnerability Scoring System (CVSS). The base score is composed of six metrics which can be used to calculate a severity score of 0-10. These metrics are: Access vector – The way in which a vulnerability can be exploited (e.g., locally or remotely)
What is 7 zip vulnerability CVE
CVE-2022-29072
7-Zip vulnerability or CVE-2022-29072 is an active zero-day vulnerability and is characterized as allowing privilege escalation and command execution for Windows when a file with the .
Is 1.2 of log4j vulnerable
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
Is log4j 2.17 vulnerable
3 or 2.17. 0: from these versions onwards, only the JAVA protocol is supported in JNDI connections. Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
What is 9.8 CVSS score
CVSS score 9.8 vs 10.0
At the same time, the highest possible score when the scope is unchanged is 9.8. This is when all impact scores are high and all exploitability metrics are most severe. This is also the only way to get a CVSS base score of 9.8.
What is a CVE critical vulnerability
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed information security vulnerabilities and exposures. CVE was launched in 1999 by the MITRE corporation to identify and categorize vulnerabilities in software and firmware.
What is 7-Zip 21.07 vulnerability
Privilege escalation vulnerability was found in 7-Zip. Malicious users can exploit this vulnerability to gain privileges and execute arbitrary code by dragging and dropping file with the . 7z extension to the Help>Contents area. The vulnerability announced in version 21.07 and disputed by vendor.
Is Log4j 1.2 17 Safe
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
Is Log4j 2.17 0 vulnerable
3 or 2.17. 0: from these versions onwards, only the JAVA protocol is supported in JNDI connections. Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
Is Log4j 2.16 still vulnerable
December 20, 2021
Log4j 2.17 has been released to address a Denial of Service (DoS) vulnerability found in v2. 16 and earlier. Log4j 2.16 and earlier does not always protect from infinite recursion in lookup evaluation, which can lead to DoS attacks. This is considered a High (7.5) vulnerability on the CVSS scale.
Is Log4j 1.2 affected by vulnerability
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
Does a CVSS score of 9.1 represent a critical vulnerability or a low priority finding
What is the Common Vulnerability Scoring System (CVSS)
| Severity | Score |
|---|---|
| Low | 0.1-3.9 |
| Medium | 4.0-6.9 |
| High | 7.0-8.9 |
| Critical | 9.0-10.0 |
What is used to score the severity of a CVE
The Common Vulnerability Scoring System (CVSS) is a method used to supply a qualitative measure of severity.
Is CVE good or bad
CVE entries are not a good source to rank products by their "overall security". The main idea behind the CVE system is to create unique identifiers for software vulnerabilities. It's not designed to be a complete and verified database of all known vulnerabilities in any product.
What is 7-Zip cve 2016 7804 untrusted search path vulnerability
Untrusted search path vulnerability in 7 Zip for Windows 16.02 and earlier allows remote attackers to gain privileges via a Trojan horse DLL in an unspecified directory. Note: References are provided for the convenience of the reader to help distinguish between vulnerabilities.
What is the CVE severity of log4j
Log4j is a software library built in Java that's used by millions of computers worldwide running online services. It's described as a zero-day (0 day) vulnerability and rated the highest severity under the Common Vulnerability Scoring System (CVSS; CVE-2021-44228).