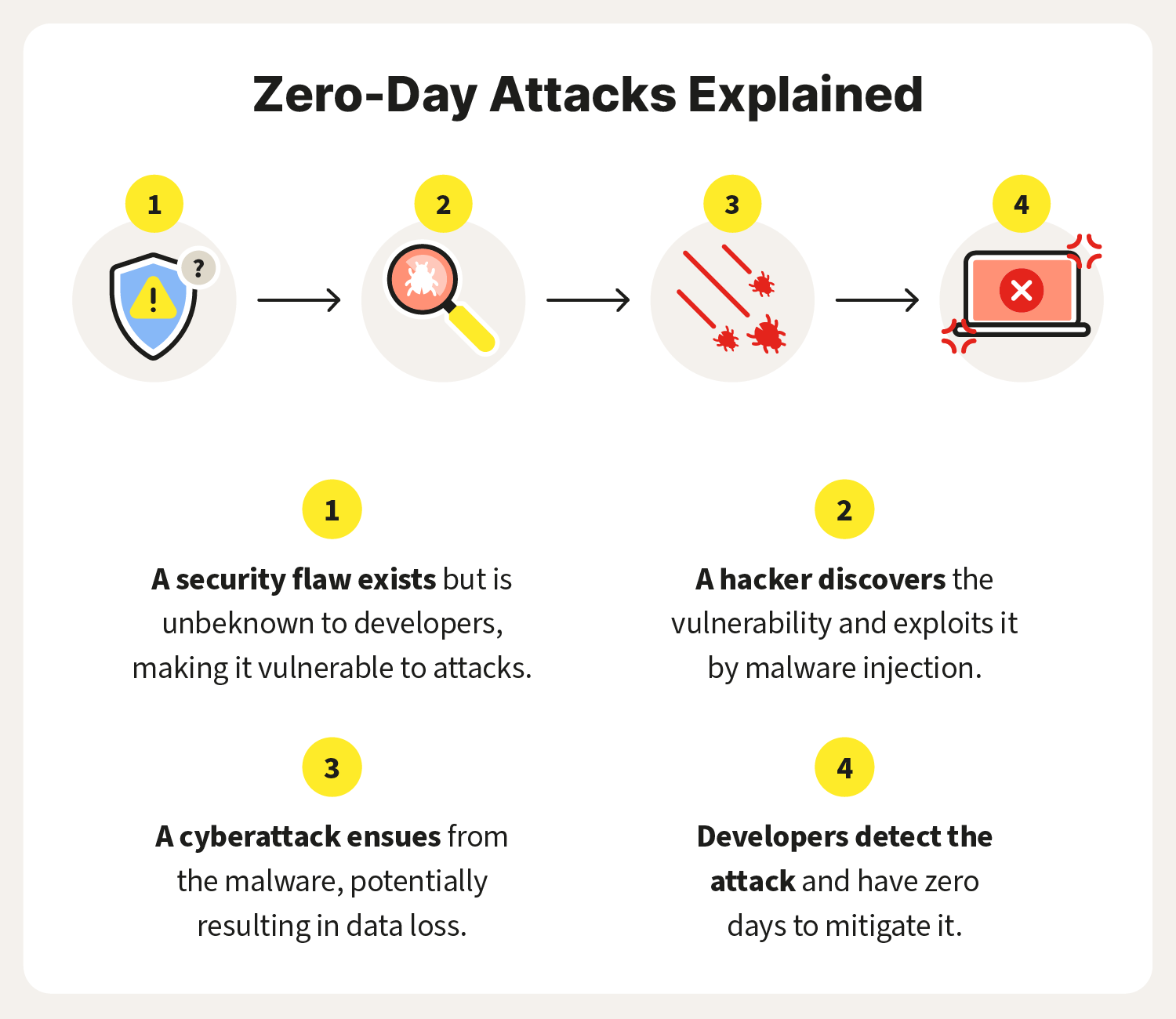
What is a zero-day vulnerability and how can it be mitigated
What is a zero-day vulnerability A zero-day vulnerability is a vulnerability in a system or device that has been disclosed but is not yet patched. An exploit that attacks a zero-day vulnerability is called a zero-day exploit.
What is a zero-day vulnerability
6 ngày trước
Zero-day attacks begin with zero-day vulnerabilities, meaning flaws or holes in security software. These can result from improper computer or security configurations or programming errors by developers themselves. Cyberattackers exploit these vulnerabilities without developers knowing.
What are the effects of zero-day attack
A zero-day exploit is one of the severest malware threats. Cyber attacks can have severe consequences for businesses, as hackers can steal money, data, or intellectual property that compromises your operations. And no companies are immune.
What is the difference between zero-day vulnerability and zero-day exploit
It is important to understand the difference: A Zero-Day Vulnerability is an unknown security vulnerability or software flaw that a threat actor can target with malicious code. A Zero-Day Exploit is the technique or tactic a malicious actor uses to leverage the vulnerability to attack a system.
How do you protect against zero-day exploits
Best Practices for Zero-Day Attack PreventionMonitor Reported Vulnerabilities.Install Next-Gen Antivirus Solutions (NGAV)Perform Rigorous Patch Management.Install a Robust Web Application Firewall.Practice the Principle of Least Privilege.
How can vulnerability be reduced
Approaches to vulnerability reduction include:Implementing building codes.Insurance and social protection (risk)Emphasising economic diversity and resilient livelihoods.Knowledge and awareness raising.Preparedness measures.
What is a real life example of zero-day vulnerability
Via zero-day exploits, an APT can gain access to a large number of computing systems at high profile organizations. A prominent example was the SolarWinds supply chain attack, in which an organized cybercrime group exploited a zero-day vulnerability to breach to US government agencies and a majority of the Fortune 500.
How common are zero-day vulnerabilities
According to the Ponemon Institute, 80% of successful breaches were Zero-Day attacks.
How can zero-day attacks be prevented
Zero-day protection is a security measure that is designed to protect against zero-day attacks. This can include things like keeping your software up to date, using security software and avoiding clickbait and phishing attacks. A zero-day virus is a type of malware that takes advantage of a zero-day vulnerability.
How do you fix a zero-day attack
4 Best Practices for Protection Against Zero-Day AttacksUse Windows Defender Exploit Guard.Leverage Next-Generation Antivirus (NGAV)Implement Patch Management.Have an Incident Response Plan Ready.
What is the opposite of zero-day vulnerability
Whereas zero-days are a class of vulnerability that is unknown to a software developer or hardware manufacturer, an N-day is a flaw that is already publicly known but may or may not have a security patch available.
What are zero-day attacks and how it works
A zero-day attack (also referred to as Day Zero) is an attack that exploits a potentially serious software security weakness that the vendor or developer may be unaware of. 1 The software developer must rush to resolve the weakness as soon as it is discovered in order to limit the threat to software users.
What is the best example of a zero-day exploit
Via zero-day exploits, an APT can gain access to a large number of computing systems at high profile organizations. A prominent example was the SolarWinds supply chain attack, in which an organized cybercrime group exploited a zero-day vulnerability to breach to US government agencies and a majority of the Fortune 500.
Can vulnerability be prevented
Security vulnerabilities, such as insecure direct object references, are a major problem for web applications. Fortunately, through fuzz testing and access validation techniques, IT security experts can detect and prevent IDOR vulnerabilities, helping safeguard applications from attack.
How can we reduce vulnerability in climate change
Examples of adaptation measures include: using scarce water resources more efficiently; adapting building codes to anticipated future climate conditions and extreme weather events; building flood defences and raising the levels of dykes; developing drought-tolerant crops; choosing tree species and forestry practices …
How common are zero-day attacks
According to the Ponemon Institute, 80% of successful breaches were Zero-Day attacks.
What is the most common recovery methods for a zero-day attacks
One of the most common recovery methods for a zero-day attacks is to physically (or via a network-based firewall) remove all access from anyone who would have the ability to exploit it.
Can zero click attacks be prevented
You need to uninstall any programs you don't even use on all of your gadgets, particularly texting ones. Additionally, you must avoid "jailbreaking" or "actively searching" your phone. A variety of protection features incorporated into iOS and Android are disabled by it. Frequently store the whole of your gadgets.
How do you defend against zero days
5 Ways to Defend Against Zero-Day MalwareIn this article, you will learn:Consider segmenting your networks.Enforce the principle of least privilege.Block exploit-like behavior.Block exploit-derived malware.Uncover hidden threats.Accurate and precise.
What are the 7 ways to help prevent zero-day attacks
For best results, zero-day attack prevention steps you should take include the following:Monitor Reported Vulnerabilities.Install Next-Gen Antivirus Solutions (NGAV)Perform Rigorous Patch Management.Install a Robust Web Application Firewall.Practice the Principle of Least Privilege.
How do hackers find zero-day vulnerability
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability. Attackers have found a new route by exploiting a zero-day vulnerability in Google's Android mobile operating system.
Can zero-day exploit be prevented
One of the most effective ways to prevent zero-day attacks is deploying a web application firewall (WAF) on the network edge. A WAF reviews all incoming traffic and filters out malicious inputs that might target security vulnerabilities.
How do you stop avoiding vulnerability
How Not to Freak Out in the Face of VulnerabilityTouch base with yourself. Keep track of how you're feeling, Piorkowski recommends.Talk about it. Once you get clear on what you're feeling, bring it up with your partner.Get a reality check.Ask for what you need.Help your partner feel safe.
What are the solutions to vulnerability
Vulnerability management solutions often include features such as policy management, application scanning/testing, vulnerability remediation, network and vulnerability monitoring, and reporting (vulnerabilities, compliance issues, etc).
Can we reduce vulnerability
Approaches to vulnerability reduction include: Implementing building codes. Insurance and social protection (risk) Emphasising economic diversity and resilient livelihoods.