What is an example of a CVE
Examples of CVEs
A classic example of a CVE is the recent Log4j vulnerability report (CVE-2021-44228). It contains detailed information about a vulnerability of the popular Java logging framework, Apache Log4j. Many service providers, like AWS, Cloudflare and Twitter, were affected by this vulnerability.
What is CVE vulnerabilities
CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability. A CVE score is often used for prioritizing the security of vulnerabilities.
What is an example of vulnerability
Physical Vulnerability may be determined by aspects such as population density levels, remoteness of a settlement, the site, design and materials used for critical infrastructure and for housing (UNISDR). Example: Wooden homes are less likely to collapse in an earthquake, but are more vulnerable to fire.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What is the most common CVE
CVE-2022-22965: The most popular CVE reported in 2022 (also known as Spring4Shell) is an extremely high-impact Injection vulnerability in Spring Framework that allows attackers to make changes remotely to a target system.
What is an example of CWE and CVE
For example, Microsoft Outlook Elevation of Privilege Vulnerability is CVE-2023-23397. CWE stands for Common Weakness Enumeration. CWE refers to the types of software weaknesses, rather than specific instances of vulnerabilities within products or systems.
How many CVE vulnerabilities are there
NVD Contains
| CVE Vulnerabilities | 220836 |
|---|---|
| Checklists | 617 |
| US-CERT Alerts | 249 |
| US-CERT Vuln Notes | 4486 |
| OVAL Queries | 10286 |
What is the cause of CVE
CVEs are most often the result of flaws or weaknesses in software that can be exploited to gain unauthorized access, steal data, or otherwise compromise the integrity of a system. In most cases this is not intentional.
What are 3 example of vulnerabilities
Vulnerability Examples
Any susceptibility to humidity, dust, soiling, natural disaster, poor encryption, or firmware vulnerability.
What are three vulnerable examples
Some common examples of vulnerable groups in society include: elderly people, people with low incomes, uninsured people, homeless people, racial or ethnic minorities, people in prison, migrant workers, pregnant women, people in the LGBTQIA community, and children.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
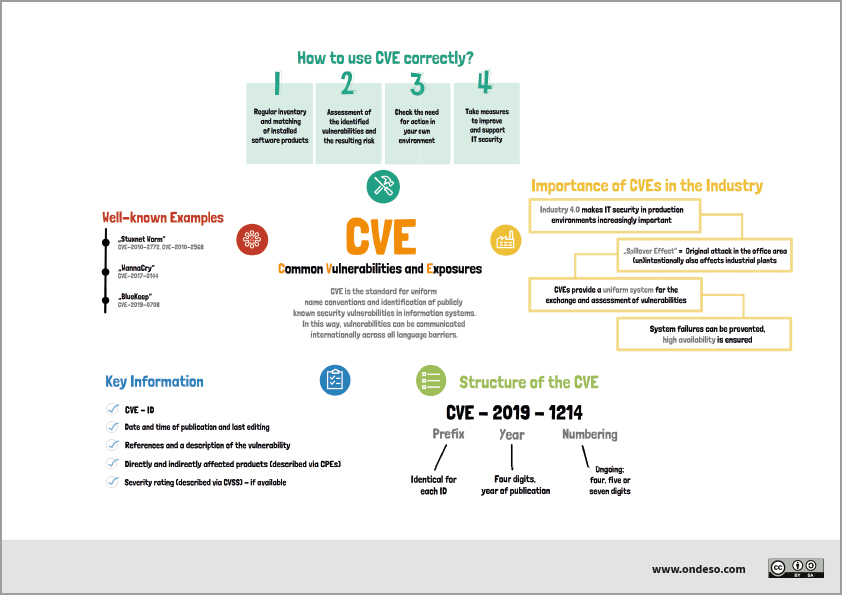
What are CVE codes
CVE usage. CVE identifiers are intended for use with respect to identifying vulnerabilities: Common Vulnerabilities and Exposures (CVE) is a dictionary of common names (i.e., CVE Identifiers) for publicly known information security vulnerabilities.
How does CVE work
CVE does this by creating a standardized identifier for a given vulnerability or exposure. CVE identifiers (also called CVE names or CVE numbers) allow security professionals to access information about specific cyber threats across multiple information sources using the same common name.
Do all vulnerabilities have a CVE
CVE stands for Common Vulnerabilities and Exposures. It is the database of publicly disclosed information on security issues. All organizations use CVEs to identify and track the number of vulnerabilities. But not all the vulnerabilities discovered have a CVE number.
What are three of the most common web vulnerabilities
Most Common Website Security VulnerabilitiesSQL Injections.Cross Site Scripting (XSS)Broken Authentication & Session Management.Insecure Direct Object References.Security Misconfiguration.Cross-Site Request Forgery (CSRF)
What is an example of most vulnerable
Some common examples of vulnerable groups in society include: elderly people, people with low incomes, uninsured people, homeless people, racial or ethnic minorities, people in prison, migrant workers, pregnant women, people in the LGBTQIA community, and children.
What are the 5 vulnerable groups
Vulnerable groupsWomen.People with children.Children.Young people.Older people.Pregnant people.People with disability and impairment.People with mental illness.
What are 3 examples of vulnerability
11 examples of vulnerabilityTelling someone when they've upset you, respectfully but honestly.Sharing something personal about yourself that you normally wouldn't.Admitting to mistakes you have made in the past.Being willing to feel difficult emotions like shame, grief, or fear.
Who creates a CVE for vulnerability
The Mitre Corporation
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
How is a CVE created
The process of creating a CVE Record begins with the discovery of a potential cybersecurity vulnerability. The information is then assigned a CVE ID by a CVE Numbering Authority (CNA), a Description and References are added by the CNA, and then the CVE Record is posted on the CVE website by the CVE Program Secretariat.
What are the 3 types of vulnerability
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
What are the 10 vulnerable groups
The vulnerable groups that face discrimination include- Women, Scheduled Castes (SC), Scheduled Tribes (ST), Children, Aged, Disabled, Poor migrants, People living with HIV/AIDS and Sexual Minorities.
What are the 6 vulnerable groups
Vulnerable groupsWomen.People with children.Children.Young people.Older people.Pregnant people.People with disability and impairment.People with mental illness.
What are the 5 types of vulnerable
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are 5 examples of social vulnerability
Disruption of communication, power supply, water supply, public services… Vulnerable residential settings (i.e. weak structure, poor protection, poor maintenance, etc.) Lack of or Limited access to critical services such as communication, transportation, power supply, water supply, sanitation, etc.