Which scanner is better than Nmap
Given below is the list of Nmap Alternatives:Zenmap. Zenmap is the free cross-platform Front End (GUI) interface of Nmap.Shodan.Angry IP Scan.Advanced Port Scanner.Fing.
Is masscan better than Nmap
Speed. – Both Nmap and Masscan are free, open source tools for network discovery and produce basically the same results. However, Masscan is a really fast internet-scale port scanner that uses asynchronous mode scanning to deliver results much faster than with Nmap.
Why is Nmap so slow
By default, Nmap scans the most common 1,000 ports. On a fast network of responsive machines, this may take a fraction of a second per host. But Nmap must slow down dramatically when it encounters rate limiting or firewalls that drop probe packets without responding. UDP scans can be agonizingly slow for these reasons.
Which Nmap scan is most stealthy
TCP SYN
SYN scan is the default and most popular scan option for good reason. It can be performed quickly, scanning thousands of ports per second on a fast network not hampered by intrusive firewalls. SYN scan is relatively unobtrusive and stealthy, since it never completes TCP connections.
Are Nmap scans illegal
When used properly, Nmap helps protect your network from invaders. But when used improperly, Nmap can (in rare cases) get you sued, fired, expelled, jailed, or banned by your ISP. Reduce your risk by reading this legal guide before launching Nmap.
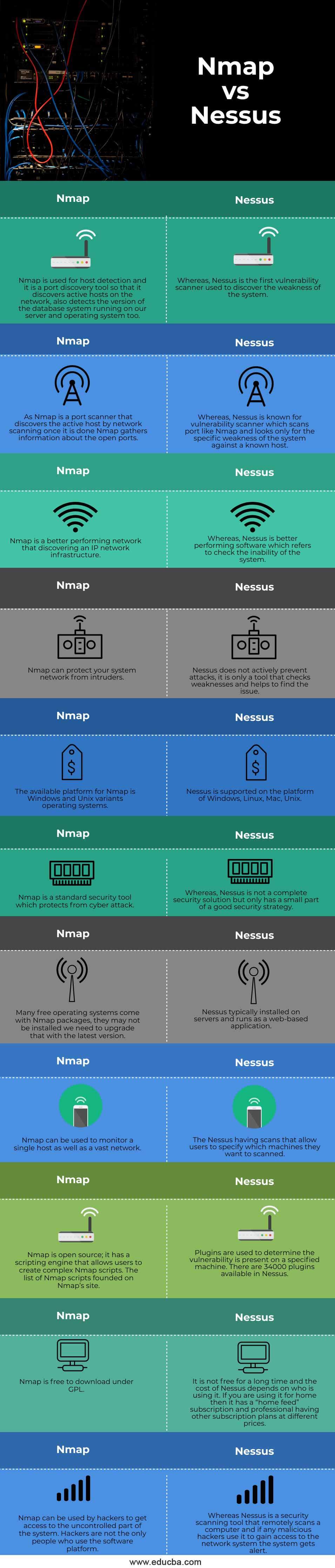
Is Nessus better than Nmap
Nessus: Best for businesses looking for a complete vulnerability scanning tool, especially for professional security auditing. Nmap: Best for organizations looking for a free scanning tool to identify open ports and services and specific vulnerabilities.
Is OpenVAS better than Nmap
The results varied between projects: OpenVAS provided some of the best results in terms of accuracy and coverage. Nmap plus Vulners provided a very false positive heavy result set that was difficult to parse or integrate with any other solution (commercial or open source).
Is Nmap illegal
When used properly, Nmap helps protect your network from invaders. But when used improperly, Nmap can (in rare cases) get you sued, fired, expelled, jailed, or banned by your ISP.
How fast is Nmap insane
Timing Templates ( -T )
| T0 | T5 | |
|---|---|---|
| Name | Paranoid | Insane |
| min-rtt-timeout | 100 ms | 50 ms |
| max-rtt-timeout | 5 minutes | 300 ms |
| initial-rtt-timeout | 5 minutes | 250 ms |
Do real hackers use Nmap
This program scans the network your computer is connected to and provides a list of ports, device names, operating systems, and other identifiers to help you understand your connection status. However, hackers can also use Nmap to access uncontrolled ports on a system.
Do hackers use Nmap
Inexperienced hackers will often use the default settings of Nmap and end up getting their IP blocked by the target IDS or their packets dropped by the network firewall. An experienced hacker will be patient and probe the target using different MAC/IP addresses to gain information about the targets system.
Do hackers use Nessus
Like most scanners, Nessus is used during penetration testing and vulnerability assessments, including malicious assaults. It is a program that scans computers for security holes that hackers could exploit.
Is Nessus the best scanner
Nessus is best at performing vulnerability scans, in fact, it gives findings and moreover accurate findings of the assessments. It does not do penetration testing or exploit the vulnerabilities because it is concerned about scanning the systems/applications.
Is OpenVAS no longer free
OpenVAS. The Open Vulnerability Assessment System, OpenVAS is a comprehensive open-source vulnerability scanning tool and vulnerability management system. It's free of cost, and its components are free software, most licensed under the GNU GPL.
Can Nmap be illegal
When used properly, Nmap helps protect your network from invaders. But when used improperly, Nmap can (in rare cases) get you sued, fired, expelled, jailed, or banned by your ISP.
Can hackers track VPN
However, a VPN keeps your browsing activity safe. Even those who can see that you use a VPN (i.e., your ISP, websites you visit, or even hackers) can't access your data, real location, or any sensitive information.
Can Nmap be traced
Log monitoring tools such as Logwatch and Swatch can certainly help, but the reality is that system logs are only marginally effective at detecting Nmap activity. Special purpose port scan detectors are a more effective approach to detecting Nmap activity. Two common examples are PortSentry and Scanlogd.
What is Nessus vs Nmap
Nessus is one of the vulnerability scanners used to find malicious attacks. Whereas, Nmap is not a full vulnerability scanner it is a reporting tool that is used to analyze the service response that is coming in packets and the reporting tool may help to identify vulnerabilities in the network.
Why is Nessus not secure
The certificate may not be considered secure because "Nessus Certification Authority" is not a trusted valid certificate authority. Because of this, when Nessus is accessed through port 8834, the browser will produce a warning regarding an unsafe connection.
What is the highest quality scanner
The best photo scanners in July 2023Epson. Perfection V600. Check Price.Plustek. Z300. Check Price.Epson. FastFoto FF-680W. Check Price.Epson. Perfection V850 Pro Photo Scanner. Check Price.Canon. P-208II. View.Canon. DR-F120. Check Price.Canon. DR-C225W II. View.Xerox. XD-Combo. Check Price.
Is Greenbone still free
Our software consists of several software components. All components are free software and can be found at GitHub.
Is Greenbone free
All Greenbone Vulnerability Management products are free software, and most components are licensed under the GNU General Public License (GPL).
Can a VPN steal passwords
Your passwords can be stolen if HTTP connections are made. In such cases, the VPN will see your passwords. If HTTPS connections to websites are built, the VPN cannot see your passwords. Malicious VPNs steal passwords by installing malware when the passwords are typed into the web browser.
Can police track a fake VPN
There is no way to track live, encrypted VPN traffic.
That's why police or government agencies who need information about websites you visited have to contact your internet service provider (ISP for short), and only then your VPN provider.
Why is Nessus scanner the best
Tenable Nessus is versatile and flexible to use. This software can be used to security scans, network scanning, vulnerability assessment and scanning. It's interface is user friendly and anyone can use it very easily. It has ability to automate scanning and reporting tasks.