What is weak cipher vulnerability
Weak Cipher Definition. A weak cipher is defined as an encryption/decryption algorithm that uses a key of insufficient length. Using an insufficient length for a key in an encryption/decryption algorithm opens up the possibility (or probability) that the encryption scheme could be broken (i.e. cracked).
What are secure ciphers
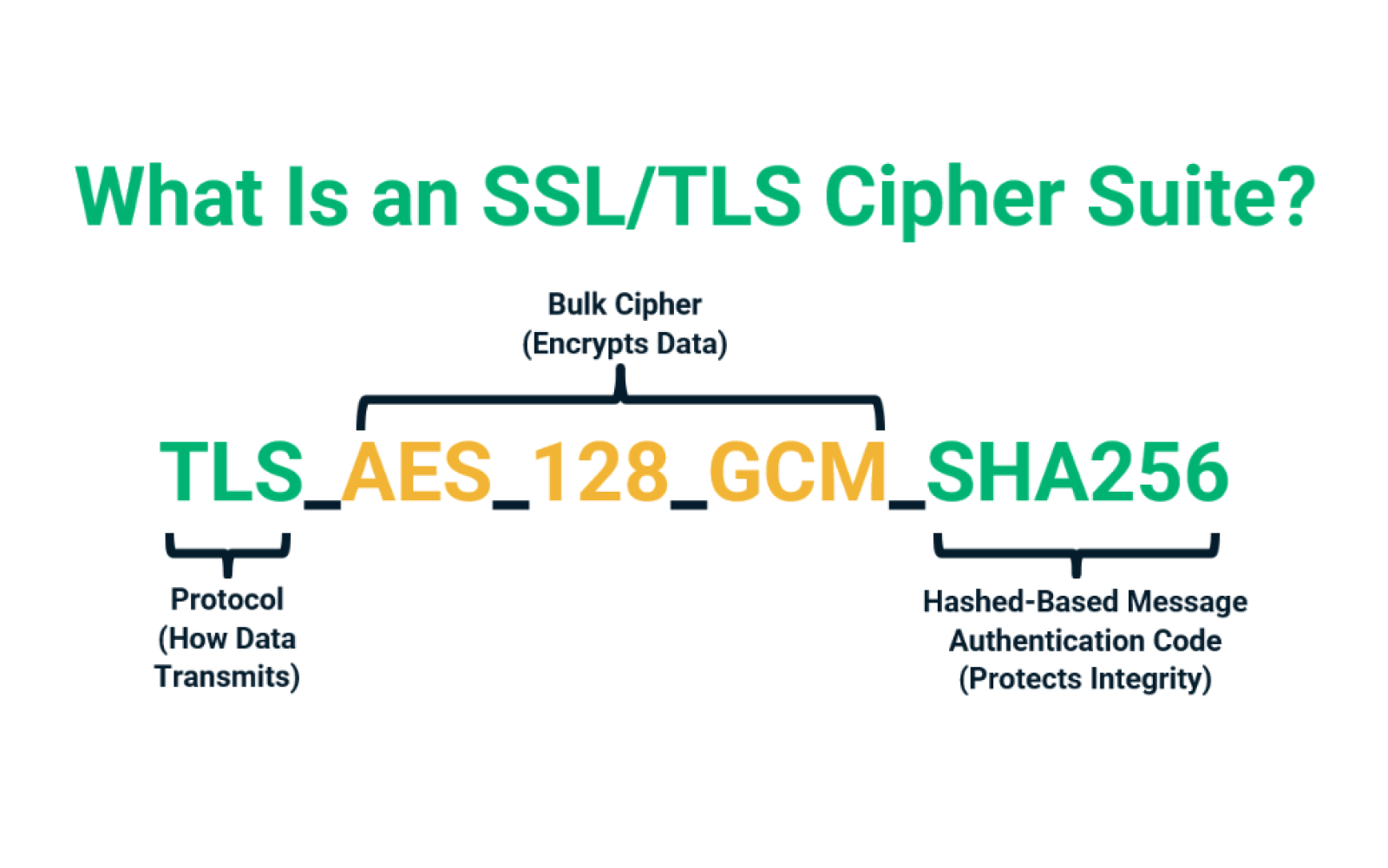
An SSL cipher, or an SSL cipher suite, is a set of algorithms or a set of instructions/steps that helps to establish a secure connection between two entities — usually the client (a user's browser) and the web server they're connecting to (your website).
What are the risks of weak SSL ciphers
Vulnerabilities in SSL Suites Weak Ciphers is a Medium risk vulnerability that is also high frequency and high visibility. This is the most severe combination of security factors that exists and it is extremely important to find it on your network and fix it as soon as possible.
What is a Cypher SSL
A cipher suite is a set of cryptographic algorithms. The schannel SSP implementation of the TLS/SSL protocols use algorithms from a cipher suite to create keys and encrypt information. A cipher suite specifies one algorithm for each of the following tasks: Key exchange. Bulk encryption.
What are stream ciphers vulnerable to
Stream ciphers are vulnerable to "key re-use" attacks, also called "two-time pad" attacks. This type of vulnerability occurs when you use the same key more than once because it is trivial to XOR the two ciphertext strings and nullify the key, which leaves only XOR'ed plain text.
Which ciphers are vulnerable to robot
The ROBOT vulnerability is quite severe for hosts that use only RSA encryption key exchanges. In such cases, attackers can record SSL/TLS traffic and use it for malicious purposes by later decryption. Hosts that support RSA encryption modes but use forward secrecy are not high risk.
What is TLS vs cipher
Cipher suites are sets of instructions that enable secure network connections through Transport Layer Security (TLS), often still referred to as Secure Sockets Layer (SSL). Behind the scenes, these cipher suites provide a set of algorithms and protocols required to secure communications between clients and servers.
What is cipher vs encryption
Ciphers, also called encryption algorithms, are systems for encrypting and decrypting data. A cipher converts the original message, called plaintext, into ciphertext using a key to determine how it is done.
Are ciphers secure
A cipher suite is as secure as the algorithms that it contains. If the version of encryption or authentication algorithm in a cipher suite have known vulnerabilities the cipher suite and TLS connection may then vulnerable. Therefore, a common attack against TLS and cipher suites is known as a downgrade attack.
Does TLS 1.2 have weak ciphers
Especially weak encryption algorithms in TLS 1.2 are designated as NULL, RC2, RC4, DES, IDEA, and TDES/3DES; cipher suites using these algorithms should not be used9. TLS 1.3 removes these cipher suites, but implementations that support both TLS 1.3 and TLS 1.2 should be checked for obsolete cipher suites.
Why is it called a cypher
A cipher is a secret code, usually one that's created using a mathematical algorithm. Sometimes the message written in code is itself called a cipher. Cipher comes from the Arabic sifr, which means "nothing" or "zero." The word came to Europe along with the Arabic numeral system.
What are substitution ciphers vulnerable to
Substitution ciphers are easy to implement and understand, but they are also vulnerable to frequency analysis, which means that an attacker can guess the key by looking at the most common letters or patterns in the ciphertext.
What is stream cipher in cyber security
A stream cipher is an encryption algorithm that uses a symmetric key to encrypt and decrypt a given amount of data. A symmetric cipher key, as opposed to an asymmetric cipher key, is an encryption tool that is used in both encryption and decryption.
Which cipher is safest
AES encryption
One of the most secure encryption types, Advanced Encryption Standard (AES) is used by governments and security organizations as well as everyday businesses for classified communications. AES uses “symmetric” key encryption.
Is TLS 1.2 a cipher
A cipher suite is a set of cryptographic algorithms. This is used to encrypt messages between clients/servers and other servers. Dataverse is using the latest TLS 1.2 cipher suites as approved by Microsoft Crypto Board.
Is TLS 1.1 a cipher
TLS 1.1 uses the same cipher suites as TLS 1.0, therefore OpenSSL does not make a distinction between the two. When it supports a cipher suite for TLS 1.1, it also supports it for TLS 1.0, and vice versa.
Why is it called cipher
A cipher is a secret code, usually one that's created using a mathematical algorithm. Sometimes the message written in code is itself called a cipher. Cipher comes from the Arabic sifr, which means "nothing" or "zero." The word came to Europe along with the Arabic numeral system.
Which cipher is most secure
AES 256-bit encryption
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. While it is theoretically true that AES 256-bit encryption is harder to crack than AES 128-bit encryption, AES 128-bit encryption has never been cracked.
Is cipher good or bad
Cipher, along with Brixton Lore, is one of the two Fast & Furious villains to be Pure Evil.
What are the vulnerable TLS 1.2 ciphers
A cipher suite is identified as obsolete when one or more of the mechanisms is weak. Especially weak encryption algorithms in TLS 1.2 are designated as NULL, RC2, RC4, DES, IDEA, and TDES/3DES; cipher suites using these algorithms should not be used9.
Does TLS 1.2 have vulnerabilities
Any software is going to have vulnerabilities – flaws that an attacker can exploit. In the case of TLS, parts of the protocol carried over from its early days in the 1990s resulted in several high-profile vulnerabilities persisting in TLS 1.2.
What does cypher mean in technology
What is a cipher In cryptology, the discipline concerned with the study of cryptographic algorithms, a cipher is an algorithm for encrypting and decrypting data. Symmetric key encryption, also called secret key encryption, depends on the use of ciphers, which operate symmetrically.
What is the meaning of ciphers
A cipher is a secret code, usually one that's created using a mathematical algorithm. Sometimes the message written in code is itself called a cipher. Cipher comes from the Arabic sifr, which means "nothing" or "zero." The word came to Europe along with the Arabic numeral system.
What are the vulnerabilities of stream ciphers
Security vulnerabilities− Stream ciphers are vulnerable to security threats such as brute force attacks and cryptanalysis. One of the reasons for this is because the keystream generated in stream ciphers can be predicted or reused, making them more exposed to attacks.
Which cipher is best for encryption
The Advanced Encryption Standard (AES)
The Advanced Encryption Standard (AES) is the trusted standard algorithm used by the United States government, as well as other organizations. Although extremely efficient in the 128-bit form, AES also uses 192- and 256-bit keys for very demanding encryption purposes.