What is CVE 2017 11882 in Excel
As you may know, CVE-2017-11882 is a vulnerability within “EQNEDT32. EXE” that can be exploited when processing specially crafted equation data (formulas data). Equation data is imported in Excel documents as an embedded OLE object.
What is CVE 2017 11882 ml
Malware of this family exploits a vulnerability of Microsoft Equation Editor (often included in Microsoft Office). If an attack succeeds, the attacker gains the ability to execute some code under a user's account.
Where to find CVE exploits
For a full list of CVE databases, please visit our article Top 4 CVE databases.Exploit DB.Rapid7.CXSecurity.Vulnerability Lab.0day.SecurityFocus.Packet Storm Security.Google Hacking Database.
What is CVE 2017 11882 on this page
What does CVE-2017-11882 entail CVE-2017-11882 is a 17-year old memory corruption issue in Microsoft Office (including Office 360). When exploited successfully, it can let attackers execute remote code on a vulnerable machine—even without user interaction—after a malicious document is opened.
What is the CVE virus
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed information security vulnerabilities and exposures. CVE was launched in 1999 by the MITRE corporation to identify and categorize vulnerabilities in software and firmware.
What is an exploit in cyber security
An exploit is a program, or piece of code, designed to find and take advantage of a security flaw or vulnerability in an application or computer system, typically for malicious purposes such as installing malware. An exploit is not malware itself, but rather it is a method used by cybercriminals to deliver malware.
What is an example of exploit
1He has never fully exploited his talents.Top athletes are able to exploit their opponents' weaknesses.We need to exploit [=take advantage of] this opportunity/situation.exploit natural resources.
What is CVE 2017 11882 Equation Editor
In 2017, Microsoft Office suffered from a critical vulnerability that affected its Equation Editor tool, known as CVE-2017-11882[1]. It's a memory corruption vulnerability that leads to remote code execution, pretty bad.
What does CVE mean in exploit
Common Vulnerabilities and Exposures (CVE) is a database of publicly disclosed information security issues. A CVE number uniquely identifies one vulnerability from the list.
What is an exploit in vulnerability
An exploit is a program, or piece of code, designed to find and take advantage of a security flaw or vulnerability in an application or computer system, typically for malicious purposes such as installing malware. An exploit is not malware itself, but rather it is a method used by cybercriminals to deliver malware.
What is exploit vs vulnerability
A vulnerability is a gap in the armor or weakness that allows people to enter. The exploit is the mechanism that someone uses to get in. For example, a door with a fragile lock has a vulnerability. The exploit uses the keys, hammer, or lockpick to break the lock.
What is the difference between vulnerability and an exploit
A vulnerability is a gap in the armor or weakness that allows people to enter. The exploit is the mechanism that someone uses to get in. For example, a door with a fragile lock has a vulnerability. The exploit uses the keys, hammer, or lockpick to break the lock.
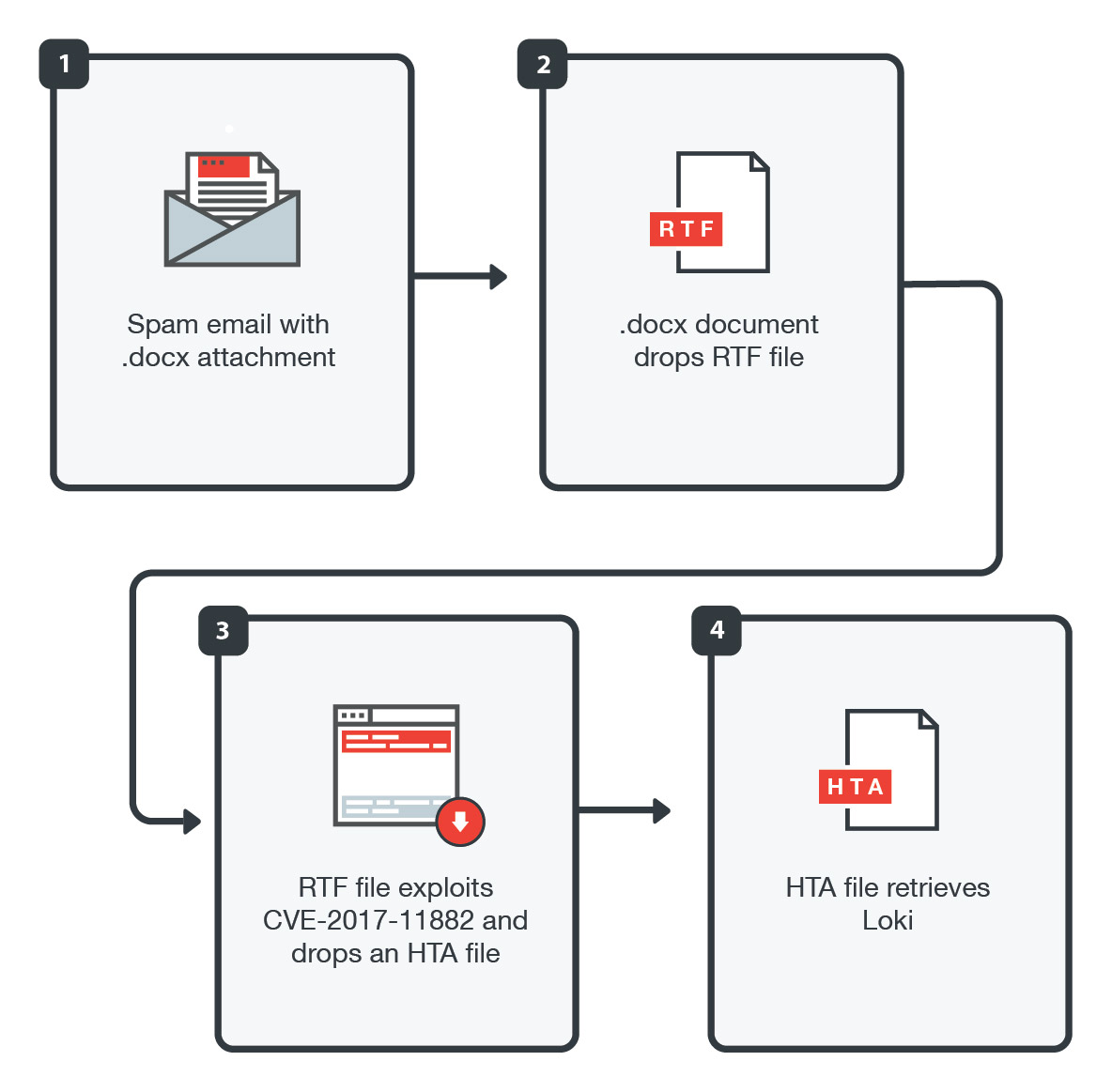
What is CVE-2017-11882 RTF exploit
CVE-2017-11882. Malware of this family exploits a vulnerability of Microsoft Equation Editor (often included in Microsoft Office). If an attack succeeds, the attacker gains the ability to execute some code under a user's account.
What is CVE-2017-11882 g5
CVE-2017-11882 Description
CVE-2017-11882 is a memory corruption glitch in Microsoft Office's Equation Editor that enables remote code execution on vulnerable devices. Hackers might exploit the flaw by tricking users into opening a specially crafted file.
What is CVE vulnerabilities
CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability. A CVE score is often used for prioritizing the security of vulnerabilities.
What do you mean by exploits
Exploit Definition
An exploit (in its noun form) is a segment of code or a program that maliciously takes advantage of vulnerabilities or security flaws in software or hardware to infiltrate and initiate a denial-of-service (DoS) attack or install malware, such as spyware, ransomware, Trojan horses, worms, or viruses.
What is considered an exploit
In video games, an exploit is the use of a bug or glitch, or use elements of a game system in a manner not intended by the game's designers, in a way that gives a substantial unfair advantage to players using it.
What are exploits attacks
An exploit (in its noun form) is a segment of code or a program that maliciously takes advantage of vulnerabilities or security flaws in software or hardware to infiltrate and initiate a denial-of-service (DoS) attack or install malware, such as spyware, ransomware, Trojan horses, worms, or viruses.
What is an example of vulnerability exploit
Operating system vulnerabilities— cybercriminals exploit these vulnerabilities to harm devices running a particular operating system. A common example includes a Denial of Service (DoS) attack that repeatedly sends fake requests to clog an operating system until it becomes overloaded.
What is the name of CVE-2017-11882
Microsoft Office Memory Corruption Vulnerability
Microsoft CVE-2017-11882: Microsoft Office Memory Corruption Vulnerability.
Is CVE short for critical vulnerabilities and exploits
CVE stands for Common Vulnerability and Exposure. CVE is a standardized, unique identifier assigned to security vulnerabilities or exposures in software and hardware products [1].
Is CVE good or bad
CVE entries are not a good source to rank products by their "overall security". The main idea behind the CVE system is to create unique identifiers for software vulnerabilities. It's not designed to be a complete and verified database of all known vulnerabilities in any product.
What are exploits in cyber security
An exploit (in its noun form) is a segment of code or a program that maliciously takes advantage of vulnerabilities or security flaws in software or hardware to infiltrate and initiate a denial-of-service (DoS) attack or install malware, such as spyware, ransomware, Trojan horses, worms, or viruses.
What is a virus exploit
Regardless of the malware type, its detectability or the person deploying it, the intent of malware use is always malicious. Exploits. An exploit is a piece of code or a program that takes advantage of a weakness (aka vulnerability) in an application or system.
What is the difference between a vulnerability and an exploit
A vulnerability is a gap in the armor or weakness that allows people to enter. The exploit is the mechanism that someone uses to get in. For example, a door with a fragile lock has a vulnerability. The exploit uses the keys, hammer, or lockpick to break the lock.