What is the NVD and CVE and CVSS
CVSS is the overall score assigned to a vulnerability. CVE is simply a list of all publicly disclosed vulnerabilities that includes the CVE ID, a description, dates, and comments. The CVSS score is not reported in the CVE listing – you must use the NVD to find assigned CVSS scores.
What is the difference between NVD and CVE
CVE Records are used in numerous cybersecurity products and services from around the world, including NVD. NVD – A vulnerability database built upon and fully synchronized with the CVE List so that any updates to CVE appear immediately in NVD.
What is the difference between CVSS and CVE
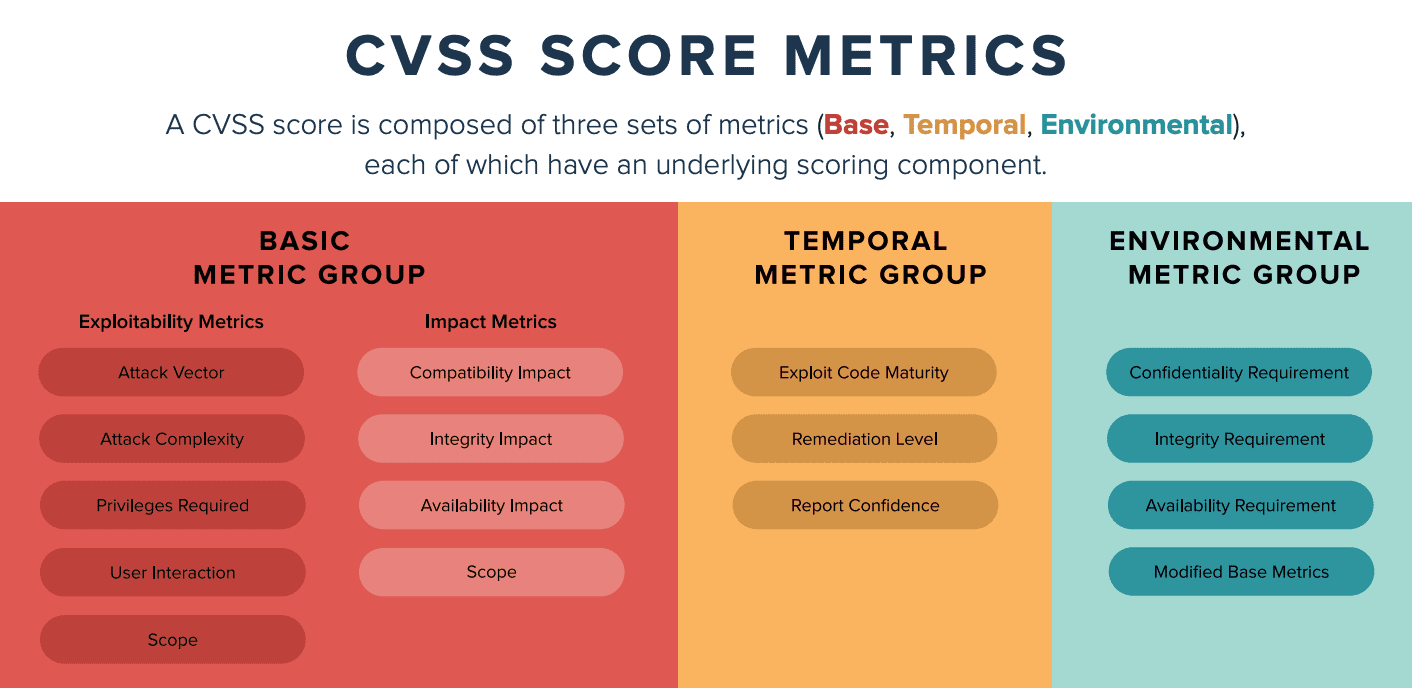
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
What is the difference between Mitre CVE and NIST NVD
CVE and NVD are separate programs. The U.S. National Vulnerability Database (NVD) was launched by the National Institute of Standards and Technology (NIST) in 2005, while the CVE List was launched by The MITRE Corporation as a community effort in 1999.
What is NVD vulnerability
The NVD is the U.S. government repository of standards based vulnerability management data represented using the Security Content Automation Protocol (SCAP). This data enables automation of vulnerability management, security measurement, and compliance.
What is NVD software
The National Vulnerability Database (NVD) is the most comprehensive publicly accessible repository of vulnerability intelligence. It is maintained by the National Institute of Standards and Technology (NIST) and draws on the work of MITRE and others.
What is the point and use of the CVE and NVD
The CVE List is a list of publicly disclosed cybersecurity vulnerabilities and exposures that is free to search, use, and incorporate into products and services. The NVD augments the CVE List with additional analysis, conversion of various data points into SCAP datatypes, a fine-grained search engine and granular APIs.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What is NVD in cyber security
The NVD is the U.S. government repository of standards based vulnerability management data represented using the Security Content Automation Protocol (SCAP). This data enables automation of vulnerability management, security measurement, and compliance.
What are the 4 main types of vulnerability in cyber security
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What is NVD in Cybersecurity
The NVD is the U.S. government repository of standards based vulnerability management data represented using the Security Content Automation Protocol (SCAP). This data enables automation of vulnerability management, security measurement, and compliance.
What is a NVD in PCI compliance
Acronym for “National Vulnerability Database.” The U.S. government repository of standards-based vulnerability management data. NVD includes databases of security checklists, security-related software flaws, misconfigurations, product names, and impact metrics.
What is the NVD process of CVE
NVD CVE Analysis
The National Vulnerability Database (NVD) is tasked with analyzing each CVE once it has been published to the CVE List, after which it is typically available in the NVD within an hour. Once a CVE is in the NVD, analysts can begin the analysis process.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 4 stages of identifying vulnerabilities
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.
What are the 5 Ds of cyber security
The 5 Ds of perimeter security (Deter, Detect, Deny, Delay, Defend) work on the 'onion skin' principle, whereby multiple layers of security work together to prevent access to your site's assets, giving you the time and intelligence you need to respond effectively.
What are the 3 types of vulnerability
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
What are the 4 levels of vulnerability
The four continuous stages of identification, prioritization, remediation, and reporting are essential for an effective vulnerability management process. A vulnerability is a flaw or weakness in a system that, if exploited, would allow a user to gain unauthorized access to conduct an attack.
What is the purpose of NVD
National Vendor Declarations (NVDs) are an important tool for the traceability of livestock. Traceability is critical for disease control, food safety, animal welfare purposes, and for providing confidence to consumers in domestic and overseas markets that Victorian-produced livestock products are safe.
What are the 4 types of vulnerability
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
What are the 4 main types of security vulnerability
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What are the 7 layers of cyber security
The 7 layers of cyber security are:Physical security.Network security.Perimeter security.Endpoint security.Application Security.Data security.User education.
What are the 7 stages of cyber security
7 stages of the cyber attack lifecycleReconnaissance. The preliminary stage of any cyber attack sees the threat actor gathering intelligence and research on their target(s).Weaponisation.Delivery.Exploitation.Installation.Command and control.Actions on objectives.
What are the 5 types of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 5 vulnerable groups
Vulnerable groupsWomen.People with children.Children.Young people.Older people.Pregnant people.People with disability and impairment.People with mental illness.